CyberArk secret-sen practice test
Secrets Manager
Question 1
When working with Summon, what is the purpose of the secrets.yml file?
- A. It is where Summon outputs the secret value after retrieval.
- B. It is where you define which secrets to retrieve.
- C. It is where you store the Conjur URL and host API key.
- D. It is the log file for Summon.
Answer:
B
Question 2
You are deploying Kubernetes resources/objects as Conjur identities.
In addition to Namespace and Deployment, from which options can you choose? (Choose two.)
- A. ServiceAccount
- B. Replica sets
- C. Secrets
- D. Tokenreviews
- E. StatefulSet
Answer:
A, E
Question 3
You modified a Conjur host policy to change its annotations for authentication.
How should you load the policy to make those changes?
- A. Use the default “append” method (e.g. conjur policy load <branch> <policy-file>).
- B. Use the “replace” method (e.g. conjur policy load – –replace <branch> <policy-file>).
- C. Use the “delete” method (e.g. conjur policy load – –delete <branch> <policy-file>).
- D. Use the “update” method (e.g. conjur policy load – –update <branch> <policy-file>).
Answer:
B
Question 4
When installing the Vault Conjur Synchronizer, you see this error:
Forbidden
Logon Token is Empty – Cannot logon
Unauthorized
What must you ensure to remediate the issue?
- A. This admin user must not be logged in to other sessions during the Vault Conjur Synchronizer installation process.
- B. You specified the correct url for Conjur and it is listed as a SAN on that url’s certificate.
- C. You correctly URI encoded the url in the installation script.
- D. You ran powershell as Administrator and there is sufficient space on the server on which you are running the installation.
Answer:
B
Question 5
Refer to the exhibit.
In which example will auto-failover occur?
A)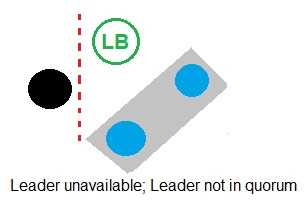
B)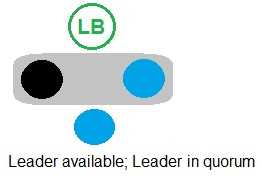
C)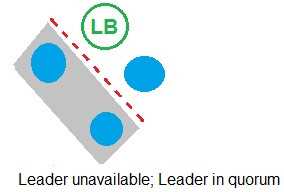
D)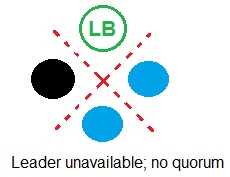
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
B
Question 6
An application is having authentication issues when trying to securely retrieve credential’s from the
Vault using the CCP webservices RESTAPI. CyberArk Support advised that further debugging should
be enabled on the CCP server to output a trace file to review detailed logs to help isolate the
problem.
What best describes how to enable debug for CCP?
- A. Edit web.config. change the “AIMWebServiceTrace” value, restart Windows Web Server (IIS)
- B. In the PVWA, go to the Applications tab, select the Application in question, go to Options > Logging and choose Debug.
- C. From the command line, run appprvmgr.exe update_config logging=debug.
- D. Edit the basic_appprovider.conf, change the “AIMWebServiceTrace" value, and restart the provider.
Answer:
A
Question 7
When working with Credential Providers in a Privileged Cloud setting, what is a special
consideration?
- A. If there are installation issues, troubleshooting may need to involve the Privileged Cloud support team.
- B. Credential Providers are not supported in a Privileged Cloud setting.
- C. The AWS Cloud account number must be defined in the file main appprovider.conf. <platform>.<version> found in the AppProviderConf Safe.
- D. Debug logging for Credential Providers deployed in a Privileged Cloud setting can inadvertently exhaust available disk space.
Answer:
A
Question 8
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know
the secret onboarding process was completed, the secret is in the expected safe with the expected
object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
- A. The application ID or Application Provider does not have the correct permissions on the safe.
- B. The client certificate fingerprint is not trusted.
- C. The service account running the application does not have the correct permissions on the safe.
- D. The OS user does not have the correct permissions on the safe
Answer:
A
Question 9
You are setting up a Kubernetes integration with Conjur. With performance as the key deciding factor,
namespace and service account will be used as identity characteristics.
Which authentication method should you choose?
- A. JWT-based authentication
- B. Certificate-based authentication
- C. API key authentication
- D. Connect (OIDC) authentication
Answer:
A
Question 10
When attempting to retrieve a credential, you receive an error 401 – Malformed Authorization
Token.
What is the cause of the issue?
- A. The token is not correctly encoded.
- B. The token you are trying to retrieve does not exist.
- C. The host does not have access to the credential with the current token.
- D. The credential has not been initialized.
Answer:
A
Question 11
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
- A. one Follower in each AZ. load balancer for the region
- B. two Followers in each region, load balanced for the region
- C. two Followers in each AZ. load balanced for the region
- D. two Followers in each region, load balanced across all regions
Answer:
A
Question 12
While installing the first CP in an environment, errors that occurred when the environment was
created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
- A. Continue configuring the application to use the CP. No further action is needed since the successful installation makes the error message benign.
- B. Review the lag file 'CreateEnv.loq' and investigate any error messages it contains.
- C. Run setup.exe again and select 'Recreate Vault Environment'. Provide the details of a user with more privileges when prompted by the installer.
- D. Review the PV WA lags to determine which REST API call used during the installation failed.
Answer:
B
Question 13
What is the correct process to upgrade the CCP Web Service?
- A. Run “sudo yum update aimprv” from the CLI.
- B. Double-click the Credential Provider installer executable and select upgrade.
- C. Double-click the AimWebService.msi and select upgrade.
- D. Uninstall and reinstall the CCP Web Service.
Answer:
D
Question 14
In a 3-node auto-failover cluster, the Leader has been brought down for patching that lasts longer
than the configured TTL. A Standby has been promoted.
Which steps are required to repair the cluster when the old Leader is brought back online?
- A. On the new Leader, generate a Standby seed for the old Leader node and add it to the cluster member list. Rebuild the old Leader as a new Standby and then re-enroll the node to the cluster.
- B. Generate a Standby seed for the newly promoted Leader. Stop and remove the container on the new Leader, then rebuild it as a new Standby. Re-enroll the Standby to the cluster and re-base replication of the 3rd Standby back to the old Leader.
- C. Generate standby seeds for the newly-promoted Leader and the 3rd Standby Stop and remove the containers and then rebuild them as new Standbys. On both new Standbys, re-enroll the node to the cluster.
- D. On the new Leader, generate a Standby seed for the old Leader node and re-upload the auto- failover policy in “replace” mode. Rebuild the old Leader as a new Standby, then re-enroll the node to the cluster.
Answer:
A
Question 15
When using the Seed Fetcher to deploy Kubernetes Followers, an error occurs in the Seed Fetcher
container. You check the logs and discover that although the Seed Fetcher was able to authenticate, it
shows a 500 error in the log and does not successfully retrieve a seed file. What is the cause?
- A. The certificate based on the Follower DNS name is not present on the Leader.
- B. The host you configured does not have access to see the certificates.
- C. The synchronizer service crashed and needs to be restarted.
- D. The Leader does not have the authenticator webservice enabled.
Answer:
A