CyberArk pam-sen practice test
cyberark sentry – pam
Question 1
The account used to install a PVWA must have ownership of which safes? (Choose two.)
- A. VaultInternal
- B. PVWAConfig
- C. System
- D. Notification Engine
- E. PVWAReports
Answer:
ac
Question 2
What is a valid combination of primary and secondary layers of authentication to a company's two-factor authentication policy?
- A. RSA SecurID Authentication (in PVWA) and LDAP Authentication
- B. CyberArk Authentication and RADIUS Authentication
- C. Oracle SSO (in PVWA) and SAML Authentication
- D. LDAP Authentication and RADIUS Authentication
Answer:
a
Question 3
You are installing multiple PVWAs behind a load balancer.
Which statement is correct?
- A. Port 1858 must be opened between the load balancer and the PVWAs.
- B. The load balancer must be configured in DNS round robin.
- C. The load balancer must support "sticky sessions".
- D. The LoadBalancerClientAddressHeader parameter in the PVWA.ini file must be set.
Answer:
c
Question 4
In large-scale environments, it is important to enable the CPM to focus its search operations on specific Safes instead of scanning all Safes it sees in the Vault.
How is this accomplished?
- A. Administration Options > CPM Settings
- B. AllowedSafe Parameter on each platform policy
- C. MaxConcurrentConnection parameter on each platform policy
- D. Administration > Options > CPM Scanner
Answer:
b
Question 5
What is the recommended method to determine if a PVWA is unavailable and should be disabled in a load balancing pool?
- A. Monitor Port 443 on the PVWA server
- B. Monitor Port 1858 on the PVWA server
- C. Ping the PVWA server
- D. Monitor Port 3389 on the PVWA server
Answer:
a
Question 6
DRAG DROP Arrange the steps to install the Password Vault Web Access (PVWA) in the correct sequence.
Answer:
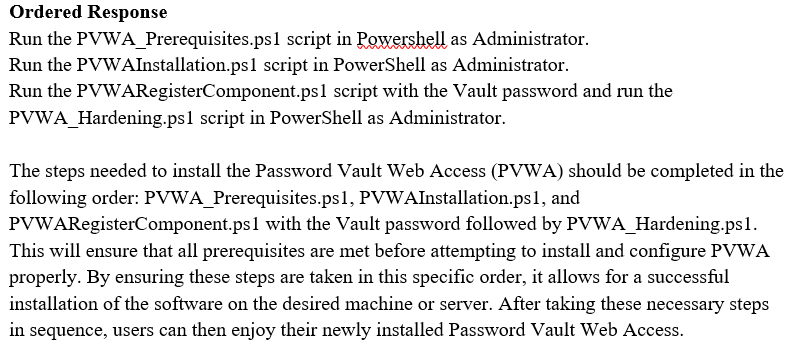
Question 7
Which parameter must be identical for both the Identity Provider (IdP) and the PVWA?
- A. IdP EntityID and PartnerIdentityProvider Name in PVWA saml.config file
- B. IdP User name and SingleSignOnServiceUrl in PVWA saml.config file
- C. IdP Audience and ServiceProviderName in the PVWA saml.config file
- D. IdP Secure hash algorithm and Certificate in the PVWA saml.config file
Answer:
d
Question 8
Which command should be executed to harden a Vault after registering it to Azure?
- A. HardenAzureFW.ps1
- B. ExecuteStage ./Hardening/HardeningConf.xml
- C. HardenVaultFW.ps1
- D. ExecuteStage ./PostInstallation/PostInstallation.xml
Answer:
c
Question 9
How should you configure PSM for SSH to support load balancing?
- A. by using a network load balancer
- B. in PVWA > Options > PSM for SSH Proxy > Servers
- C. in PVWA > Options > PSM for SSH Proxy > Servers > VIP
- D. by editing sshd.config on the all the PSM for SSH servers
Answer:
c
Question 10
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA_Hardening.ps1 perform when run? (Choose two.)
- A. performs IIS hardening
- B. configures all group policy settings
- C. renames the local Administrator Account
- D. configures Windows Firewall
- E. imports the CyberArk INF configuration
Answer:
ad