Exclusive access allows only one person to check-out an account at a time. One-time password schedules an account for a password change after the MinValidityPeriod period expires
DRAG DROP
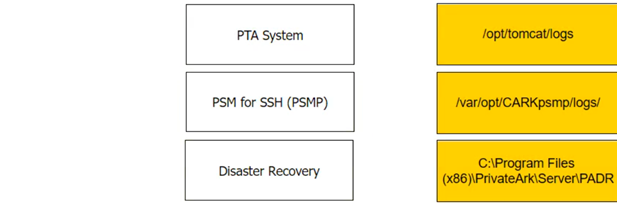
Match each component to its respective Log File location.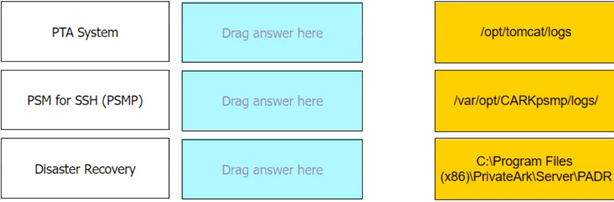
Which statement about the Master Policy best describes the differences between one-time password and exclusive access functionality?
d
Exclusive access allows only one person to check-out an account at a time. One-time password schedules an account for a password change after the MinValidityPeriod period expires
What are common ways that organizations leverage the CyberArk Blueprint for Identity Security Success? (Choose three.)
ade
Due to corporate storage constraints, you have been asked to disable session monitoring and recording for 500 testing accounts used for your lab environment.
How do you accomplish this?
b
Correct answer is A
Which accounts can be selected for use in the Windows discovery process? (Choose two.)
bd
AB Select the user who will perform the scan. Either select an account from the Vault or manually specify a user and password: Select from Vault – Select a Vault account to run the scan. This is recommended for recurrent scans. Click Click to select an account from the Vault; a list of Vault accounts appears. These are all domain accounts in the specified domain
A and B.https://docs.cyberark.com/pam-self-hosted/latest/en/content/pasimp/managing-discovery-processes.htm
Which dependent accounts does the CPM support out-of-the-box? (Choose three.)
cef
https://docs.cyberark.com/pam-self-hosted/13.0/en/content/landing%20pages/lpserviceplugins.htm
the answer BCE who make this answer
You want to generate a license capacity report.
Which tool accomplishes this?
c
the answer is B who made this dum???
Which processes reduce the risk of credential theft? (Choose two.)
ab
Answeres are BD, b'cause AnD are for preventing from behavior activities and accessing vault in irregular day/hour
Answeres are BD, b'cause AnD are for preventing from behavior activities and accessing vault in irregular day/hour
Where can reconcile and/or logon accounts be linked to an account? (Choose two.)
ae
https://docs.cyberark.com/privilege-cloud-standard/latest/en/content/pasimp/linked-pas-accounts.htm?TocPath=Administrators%7CManage%20your%20accounts%7C_____4
It can be done at account level and platform level configuration
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
a
The EVD can do this task
PTA System -> /opt/tomcat/logs; PSM for SSH -> /var/opt/CARKpsmp/logs/; Disaster Recovery -> C:\Program Files(x86)\PrivateArk\Server\PADR\