crowdstrike ccfh-202 practice test
CrowdStrike Certified Falcon Hunter
Question 1
Which of the following is a suspicious process behavior?
- A. PowerShell running an execution policy of RemoteSigned
- B. An Internet browser (eg, Internet Explorer) performing multiple DNS requests
- C. PowerShell launching a PowerShell script
- D. Non-network processes (eg, notepad exe) making an outbound network connection
Answer:
D
Explanation:
Non-network processes are processes that are not expected to communicate over the network, such
as notepad.exe. If they make an outbound network connection, it could indicate that they are
compromised or maliciously used by an adversary. PowerShell running an execution policy of
RemoteSigned is a default setting that allows local scripts to run without digital signatures. An
Internet browser performing multiple DNS requests is a normal behavior for web browsing.
PowerShell launching a PowerShell script is also a common behavior for legitimate tasks.
Reference:
https://www.crowdstrike.com/blog/tech-center/detect-malicious-use-of-non-network-
processes/
Question 2
Which field should you reference in order to find the system time of a *FileWritten event?
- A. ContextTimeStamp_decimal
- B. FileTimeStamp_decimal
- C. ProcessStartTime_decimal
- D. timestamp
Answer:
A
Explanation:
ContextTimeStamp_decimal is the field that shows the system time of the event that triggered the
sensor to send data to the cloud. In this case, it would be the time when the file was written.
FileTimeStamp_decimal is the field that shows the last modified time of the file, which may not be
the same as the time when the file was written. ProcessStartTime_decimal is the field that shows the
start time of the process that performed the file write operation, which may not be the same as the
time when the file was written. Timestamp is the field that shows the time when the sensor data was
received by the cloud, which may not be the same as the time when the file was written.
Reference:
https://www.crowdstrike.com/blog/tech-center/understanding-timestamps-in-
crowdstrike-falcon/
Question 3
What Search page would help a threat hunter differentiate testing, DevOPs, or general user activity
from adversary behavior?
- A. Hash Search
- B. IP Search
- C. Domain Search
- D. User Search
Answer:
D
Explanation:
User Search is a search page that allows a threat hunter to search for user activity across endpoints
and correlate it with other events. This can help differentiate testing, DevOPs, or general user activity
from adversary behavior by identifying anomalous or suspicious user actions, such as logging into
multiple systems, running unusual commands, or accessing sensitive files.
Reference: https://www.crowdstrike.com/blog/tech-center/user-search-in-crowdstrike-falcon/
Question 4
An analyst has sorted all recent detections in the Falcon platform to identify the oldest in an effort to
determine the possible first victim host What is this type of analysis called?
- A. Visualization of hosts
- B. Statistical analysis
- C. Temporal analysis
- D. Machine Learning
Answer:
C
Explanation:
Temporal analysis is a type of analysis that focuses on the timing and sequence of events in order to
identify patterns, trends, or anomalies. By sorting all recent detections in the Falcon platform to
identify the oldest, an analyst can perform temporal analysis to determine the possible first victim
host and trace back the origin of an attack.
Reference:
https://www.crowdstrike.com/blog/tech-center/temporal-analysis-in-crowdstrike-falcon/
Question 5
Refer to Exhibit.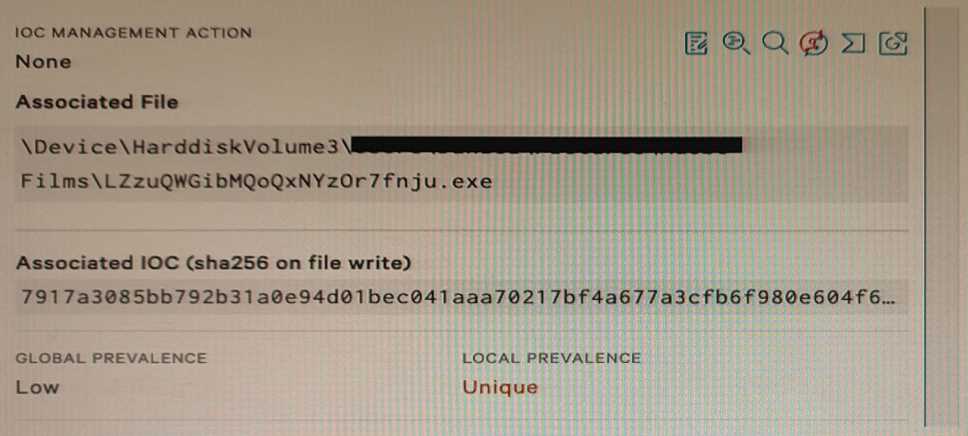
Falcon detected the above file attempting to execute. At initial glance; what indicators can we use to
provide an initial analysis of the file?
- A. VirusTotal, Hybrid Analysis, and Google pivot indicator lights enabled
- B. File name, path, Local and Global prevalence within the environment
- C. File path, hard disk volume number, and IOC Management action
- D. Local prevalence, IOC Management action, and Event Search
Answer:
B
Explanation:
The file name, path, Local and Global prevalence are indicators that can provide an initial analysis of
the file without relying on external sources or tools. The file name can indicate the purpose or origin
of the file, such as if it is a legitimate application or a malicious payload. The file path can indicate
where the file was located or executed from, such as if it was in a temporary or system directory. The
Local and Global prevalence can indicate how common or rare the file is within the environment or
across all Falcon customers, which can help assess the risk or impact of the file.
Reference:
https://www.crowdstrike.com/blog/tech-center/understanding-file-prevalence-in-
crowdstrike-falcon/
Question 6
A benefit of using a threat hunting framework is that it:
- A. Automatically generates incident reports
- B. Eliminates false positives
- C. Provides high fidelity threat actor attribution
- D. Provides actionable, repeatable steps to conduct threat hunting
Answer:
D
Explanation:
A threat hunting framework is a methodology that guides threat hunters in planning, executing, and
improving their threat hunting activities. A benefit of using a threat hunting framework is that it
provides actionable, repeatable steps to conduct threat hunting in a consistent and efficient manner.
A threat hunting framework does not automatically generate incident reports, eliminate false
positives, or provide high fidelity threat actor attribution, as these are dependent on other factors
such as data sources, tools, and analysis skills.
Reference: https://www.crowdstrike.com/blog/tech-center/threat-hunting-framework/
Question 7
Which of the following is an example of a Falcon threat hunting lead?
- A. A routine threat hunt query showing process executions of single letter filename (e.g., a.exe) from temporary directories
- B. Security appliance logs showing potentially bad traffic to an unknown external IP address
- C. A help desk ticket for a user clicking on a link in an email causing their machine to become unresponsive and have high CPU usage
- D. An external report describing a unique 5 character file extension for ransomware encrypted files
Answer:
A
Explanation:
A Falcon threat hunting lead is a piece of information that can be used to initiate or guide a threat
hunting activity within the Falcon platform. A routine threat hunt query showing process executions
of single letter filename (e.g., a.exe) from temporary directories is an example of a Falcon threat
hunting lead, as it can indicate potential malicious activity that can be further investigated using
Falcon data and features. Security appliance logs, help desk tickets, and external reports are not
examples of Falcon threat hunting leads, as they are not directly related to the Falcon platform or
data.
Reference:
https://www.crowdstrike.com/blog/tech-center/threat-hunting-leads-in-crowdstrike-
falcon/
Question 8
The Falcon Detections page will attempt to decode Encoded PowerShell Command line parameters
when which PowerShell Command line parameter is present?
- A. -Command
- B. -Hidden
- C. -e
- D. -nop
Answer:
A
Explanation:
The Falcon Detections page will attempt to decode Encoded PowerShell Command line parameters
when the -Command parameter is present. The -Command parameter allows PowerShell to execute
a specified script block or string. If the script block or string is encoded using Base64 or other
methods, the Falcon Detections page will try to decode it and show the original command. The -
Hidden, -e, and -nop parameters are not related to encoding or decoding PowerShell commands.
Reference:
https://www.crowdstrike.com/blog/tech-center/decoding-powershell-commands-in-
crowdstrike-falcon/
Question 9
Which structured analytic technique contrasts different hypotheses to determine which is the best
leading (prioritized) hypothesis?
- A. Model hunting framework
- B. Competitive analysis
- C. Analysis of competing hypotheses
- D. Key assumptions check
Answer:
C
Explanation:
Analysis of competing hypotheses is a structured analytic technique that contrasts different
hypotheses to determine which is the best leading (prioritized) hypothesis. It involves listing all the
possible hypotheses, identifying the evidence and assumptions for each hypothesis, evaluating the
consistency and reliability of the evidence and assumptions, and rating the likelihood of each
hypothesis based on the evidence and assumptions.
Reference: https://www.crowdstrike.com/blog/tech-center/analysis-of-competing-hypotheses/
Question 10
Which SPL (Splunk) field name can be used to automatically convert Unix times (Epoch) to UTC
readable time within the Flacon Event Search?
- A. utc_time
- B. conv_time
- C. _time
- D. time
Answer:
C
Explanation:
_time is the SPL (Splunk) field name that can be used to automatically convert Unix times (Epoch) to
UTC readable time within the Falcon Event Search. It is a default field that shows the timestamp of
each event in a human-readable format. utc_time, conv_time, and time are not valid SPL field names
for converting Unix times to UTC readable time.
Reference:
https://www.crowdstrike.com/blog/tech-center/understanding-timestamps-in-
crowdstrike-falcon/
Question 11
Which of the following would be the correct field name to find the name of an event?
- C. EVENT_SIMPLE_NAME
- D. event_simpleName
Answer:
A
Explanation:
Event_SimpleName is the correct field name to find the name of an event in Falcon Event Search. It is
a field that shows the simplified name of each event type, such as ProcessRollup2, DnsRequest, or
FileDelete. Event_Simple_Name, EVENT_SIMPLE_NAME, and event_simpleName are not valid field
names for finding the name of an event.
Reference: https://www.crowdstrike.com/blog/tech-center/event-search-in-crowdstrike-falcon/
Question 12
Event Search data is recorded with which time zone?
- A. PST
- B. GMT
- C. EST
- D. UTC
Answer:
D
Explanation:
Event Search data is recorded with UTC (Coordinated Universal Time) time zone. UTC is a standard
time zone that is used as a reference point for other time zones. PST (Pacific Standard Time), GMT
(Greenwich Mean Time), and EST (Eastern Standard Time) are not the time zones that Event Search
data is recorded with.
Reference:
https://www.crowdstrike.com/blog/tech-center/understanding-timestamps-in-
crowdstrike-falcon/
Question 13
Which of the following Event Search queries would only find the DNS lookups to the domain: www
randomdomain com?
- A. event_simpleName=DnsRequest DomainName=www randomdomain com
- B. event_simpleName=DnsRequest DomainName=randomdomain com ComputerName=localhost
- C. Dns=randomdomain com
- D. ComputerName=localhost DnsRequest "randomdomain com"
Answer:
A
Explanation:
This Event Search query would only find the DNS lookups to the domain www randomdomain com,
as it specifies the exact event type and domain name to match. The other queries would either find
other events or domains that are not relevant to the question.
Reference: https://www.crowdstrike.com/blog/tech-center/event-search-in-crowdstrike-falcon/
Question 14
How do you rename fields while using transforming commands such as table, chart, and stats?
- A. By renaming the fields with the "rename" command after the transforming command e.g. "stats count by ComputerName | rename count AS total_count"
- B. You cannot rename fields as it would affect sub-queries and statistical analysis
- C. By using the "renamed" keyword after the field name eg "stats count renamed totalcount by ComputerName"
- D. By specifying the desired name after the field name eg "stats count totalcount by ComputerName"
Answer:
A
Explanation:
The rename command is used to rename fields while using transforming commands such as table,
chart, and stats. It can be used after the transforming command and specify the old and new field
names with the AS keyword. You can rename fields as it would not affect sub-queries and statistical
analysis, as long as you use the correct field names in your queries. The renamed keyword and the
desired name after the field name are not valid ways to rename fields.
Reference: https://docs.splunk.com/Documentation/Splunk/8.2.3/SearchReference/Rename
Question 15
SPL (Splunk) eval statements can be used to convert Unix times (Epoch) into UTC readable time
Which eval function is correct^
- A. now
- B. typeof
- C. strftime
- D. relative time
Answer:
C
Explanation:
The strftime eval function is used to convert Unix times (Epoch) into UTC readable time. It takes two
arguments: a Unix time field and a format string that specifies how to display the time. The now,
typeof, and relative_time eval functions are not used to convert Unix times into UTC readable time.
Reference:
https://docs.splunk.com/Documentation/Splunk/8.2.3/SearchReference/CommonEvalFunctions