comptia n10-009 practice test
CompTIA Network+
Question 1
A client wants to increase overall security after a recent breach. Which of the following would be
best to implement? (Select two.)
- A. Least privilege network access
- B. Dynamic inventeries
- C. Central policy management
- D. Zero-touch provisioning
- E. Configuration drift prevention
- F. Subnet range limits
Answer:
A,C
Explanation:
To increase overall security after a recent breach, implementing least privilege network access and
central policy management are effective strategies.
Least Privilege Network Access: This principle ensures that users and devices are granted only the
access necessary to perform their functions, minimizing the potential for unauthorized access or
breaches. By limiting permissions, the risk of an attacker gaining access to critical parts of the
network is reduced.
Central Policy Management: Centralized management of security policies allows for consistent and
streamlined implementation of security measures across the entire network. This helps in quickly
responding to security incidents, ensuring compliance with security protocols, and reducing the
chances of misconfigurations.
Network Reference:
CompTIA Network+ N10-007 Official Certification Guide: Discusses network security principles,
including least privilege and policy management.
Cisco Networking Academy: Provides training on implementing security policies and access controls.
Network+ Certification All-in-One Exam Guide: Covers strategies for enhancing network security and
managing policies effectively.
Question 2
A network administrator needs to connect two routers in a point-to-point configuration and conserve
IP space. Which of the following subnets should the administrator use?
- A. 724
- B. /26
- C. /28
- D. /30
Answer:
D
Explanation:
Using a /30 subnet mask is the most efficient way to conserve IP space for a point-to-point
connection between two routers. A /30 subnet provides four IP addresses, two of which can be
assigned to the router interfaces, one for the network address, and one for the broadcast address.
This makes it ideal for point-to-point links where only two usable IP addresses are needed.Reference:
CompTIA Network+ study materials and subnetting principles.
Question 3
A network administrator determines that some switch ports have more errors present than
expected. The administrator traces the cabling associated with these ports. Which of the following
would most likely be causing the errors?
- A. arp
- B. tracert
- C. nmap
- D. ipconfig
Answer:
D
Question 4
A user notifies a network administrator about losing access to a remote file server. The network
administrator is able to ping the server and verifies the current firewall rules do not block access to
the network fileshare. Which of the following tools wold help identify which ports are open on the
remote file server?
- A. Dig
- B. Nmap
- C. Tracert
- D. nslookup
Answer:
B
Explanation:
Nmap (Network Mapper) is a powerful network scanning tool used to discover hosts and services on
a computer network. It can be used to identify which ports are open on a remote server, which can
help diagnose access issues to services like a remote file server.
Port Scanning: Nmap can perform comprehensive port scans to determine which ports are open and
what services are running on those ports.
Network Discovery: It provides detailed information about the host’s operating system, service
versions, and network configuration.
Security Audits: Besides troubleshooting, Nmap is also used for security auditing and identifying
potential vulnerabilities.
Network Reference:
CompTIA Network+ N10-007 Official Certification Guide: Covers network scanning tools and their
uses.
Nmap Documentation: Official documentation provides extensive details on how to use Nmap for
port scanning and network diagnostics.
Network+ Certification All-in-One Exam Guide: Discusses various network utilities, including Nmap,
and their applications in network troubleshooting.
Question 5
Which of the following allows for the interception of traffic between the source and destination?
- A. Self-signed certificate
- B. VLAN hopping
- C. On-path attack
- D. Phishing
Answer:
C
Explanation:
An on-path attack (formerly known as a man-in-the-middle (MITM) attack) involves intercepting and
potentially altering communications between two parties without their knowledge. This can be done
via techniques like ARP poisoning, rogue access points, or SSL stripping.
Breakdown of Options:
A . Self-signed certificate – These are untrusted SSL certificates but do not intercept traffic.
B . VLAN hopping – VLAN hopping exploits VLAN misconfigurations but does not necessarily intercept
communications.
C . On-path attack – Correct answer. This intercepts and modifies traffic between two endpoints.
D . Phishing – Phishing tricks users into revealing credentials rather than intercepting network traffic.
Reference:
CompTIA Network+ (N10-009) Official Study Guide – Domain 3.2: Explain common security concepts.
NIST SP 800-115: Guide to Security Testing and Assessments
Question 6
A network technician is terminating a cable to a fiber patch panel in the MDF. Which of the following
connector types is most likely in use?
- A. F-type
- B. RJ11
- C. BNC
- D. SC
Answer:
D
Explanation:
In a fiber patch panel, the SC (Subscriber Connector or Standard Connector) is commonly used
because of its push-pull design and reliability in enterprise environments.
Breakdown of Options:
A . F-type – Used for coaxial cables (e.g., cable TV), not fiber.
B . RJ11 – Used for telephone lines, not fiber.
C . BNC – Used for coaxial connections, not fiber.
✅
D . SC –
Correct answer. A standard fiber optic connector used in patch panels.
Reference:
CompTIA Network+ (N10-009) Official Study Guide – Domain 1.1: Compare and contrast physical
network connectors.
Question 7
A network administrator is planning to implement device monitoring to enhance network visibility.
The security that the solution provides authentication and encryption. Which of the following meets
these requirements?
- A. SIEM
- B. Syslog
- C. NetFlow
- D. SNMPv3
Answer:
D
Explanation:
SNMPv3 (Simple Network Management Protocol version 3) provides device monitoring with
authentication and encryption. This enhances network visibility and security by ensuring that
monitoring data is securely transmitted and access to network devices is authenticated.
Authentication: SNMPv3 includes robust mechanisms for authenticating users accessing network
devices.
Encryption: It provides encryption to protect the integrity and confidentiality of the data being
transmitted.
Network Management: SNMPv3 allows for detailed monitoring and management of network
devices, ensuring better control and security.
Network Reference:
CompTIA Network+ N10-007 Official Certification Guide: Covers SNMP versions, their features, and
security enhancements in SNMPv3.
Cisco Networking Academy: Provides training on implementing and securing SNMP for network
management.
Network+ Certification All-in-One Exam Guide: Explains the benefits and security features of SNMPv3
for network monitoring.
Question 8
A network engineer is designing a secure communication link between two sites. The entire data
stream needs to remain confidential. Which of the following will achieve this goal?
- A. GRE
- B. IKE
- C. ESP
- D. AH
Answer:
C
Explanation:
Definition of ESP (Encapsulating Security Payload):
ESP is a part of the IPsec protocol suite designed to provide confidentiality, integrity, and authenticity
of data by encrypting the payload and optional ESP trailer.
Ensuring Confidentiality:
Encryption: ESP encrypts the payload, ensuring that the data remains confidential during
transmission. Only authorized parties with the correct decryption keys can access the data.
Modes of Operation: ESP can operate in transport mode (encrypts only the payload) or tunnel mode
(encrypts the entire IP packet), both providing strong encryption to secure data between sites.
Comparison with Other Protocols:
GRE (Generic Routing Encapsulation): A tunneling protocol that does not provide encryption or
security features.
IKE (Internet Key Exchange): A protocol used to set up a secure, authenticated communications
channel, but it does not encrypt the data itself.
AH (Authentication Header): Provides integrity and authentication for IP packets but does not
encrypt the payload.
Implementation:
Use ESP as part of an IPsec VPN configuration to encrypt and secure communication between two
sites. This involves setting up IPsec policies and ensuring both endpoints are configured to use ESP
for data encryption.
Reference:
CompTIA Network+ study materials on IPsec and secure communication protocols.
Question 9
Which of the following allows a remote user to connect to the network?
- A. Command-line interface
- B. API gateway
- C. Client-to-site VPN
- D. Jump box
Answer:
C
Explanation:
A Client-to-Site VPN allows a remote user to securely connect to a company's internal network,
providing access as if they were physically on-site.
Question 10
Following a fire in a data center, the cabling was replaced. Soon after, an administrator notices
network issues. Which of the following are the most likely causes of the network issues? (Select
two).
- A. The switches are not the correct voltage.
- B. The HVAC system was not verified as fully functional after the fire.
- C. The VLAN database was not deleted before the equipment was brought back online.
- D. The RJ45 cables were replaced with unshielded cables.
- E. The wrong transceiver type was used for the new termination.
- F. The new RJ45 cables are a higher category than the old ones.
Answer:
D,E
Explanation:
Unshielded cables (D) are more prone to interference and may not be suitable for certain
environments, especially after a fire where interference could be heightened.
Using the wrong transceiver (E) for new terminations can lead to compatibility issues, causing
network failures.
=================
Question 11
Which of the following could provide a lightweight and private connection to a remote box?
- A. Site-to-site VPN
- B. Telnet
- C. Console
- D. Secure Shell
Answer:
D
Explanation:
Secure Shell (SSH) is a protocol used to securely access remote devices over an unsecured network. It
provides encrypted command-line access and is a lightweight and secure method of remote
administration.
A . Site-to-site VPN connects entire networks, not just a single host.
B . Telnet is not secure; it transmits data (including credentials) in plaintext.
C . Console access is direct via serial cable, not remote.
Reference:
CompTIA Network+ N10-009 Official Objectives: 2.6 – Configure and troubleshoot remote access.
Question 12
A network technician is troubleshooting network latency and has determined the issue to be
occuring two network switches( Switch10 and Switch11). Symptoms reported included poor video
performance and slow file copying. Given the following informtion: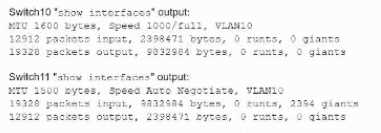
Which of the following should the technician most likely do to resolve the issue?
- A. Disable automatic negotiation on Switch11.
- B. Modify Switch10 MTU value to 1500.
- C. Configure STP on both switches.
- D. Change the native VLAN on the ports.
Answer:
B
Question 13
Which of the following network devices converts wireless signals to electronic signals?
- A. Router
- B. Firewall
- C. Access point
- D. Load balancer
Answer:
C
Explanation:
Role of an Access Point (AP):
Wireless to Wired Conversion: An access point (AP) is a device that allows wireless devices to
connect to a wired network using Wi-Fi. It converts wireless signals (radio waves) into electronic
signals that can be understood by wired network devices.
Functionality:
Signal Conversion: The AP receives wireless signals from devices such as laptops, smartphones, and
tablets, converts them into electronic signals, and transmits them over the wired network.
Connectivity: APs provide a bridge between wireless and wired segments of the network, enabling
seamless communication.
Comparison with Other Devices:
Router: Directs traffic between different networks and may include built-in AP functionality but is not
primarily responsible for converting wireless to electronic signals.
Firewall: Protects the network by controlling incoming and outgoing traffic based on security rules,
not involved in signal conversion.
Load Balancer: Distributes network or application traffic across multiple servers to ensure reliability
and performance, not involved in signal conversion.
Deployment:
APs are commonly used in environments where wireless connectivity is needed, such as offices,
homes, and public spaces. They enhance mobility and provide flexible network access.
Reference:
CompTIA Network+ study materials on wireless networking and access points.
Question 14
Which of the following disaster recovery metrics is used to describe the amount of data that is lost
since the last backup?
- A. MTTR
- B. RTO
- C. RPO
- D. MTBF
Answer:
C
Explanation:
Definition of RPO:
Recovery Point Objective (RPO) is a disaster recovery metric that describes the maximum acceptable
amount of data loss measured in time. It indicates the point in time to which data must be recovered
to resume normal operations after a disaster.
For example, if the RPO is set to 24 hours, then the business could tolerate losing up to 24 hours'
worth of data in the event of a disruption.
Why RPO is Important:
RPO is critical for determining backup frequency and helps businesses decide how often they need to
back up their data. A lower RPO means more frequent backups and less potential data loss.
Comparison with Other Metrics:
MTTR (Mean Time to Repair): Refers to the average time required to repair a system or component
and return it to normal operation.
RTO (Recovery Time Objective): The maximum acceptable length of time that a computer, system,
network, or application can be down after a failure or disaster occurs.
MTBF (Mean Time Between Failures): The predicted elapsed time between inherent failures of a
system during operation.
How RPO is Used in Disaster Recovery:
Organizations establish RPOs to ensure that they can recover data within a timeframe that is
acceptable to business operations. This involves creating a backup plan that meets the RPO
requirements.
Reference:
CompTIA Network+ study materials and certification guides.
Question 15
Which of the following fiber connector types is the most likely to be used on a network interface
card?
- A. LC
- B. SC
- C. ST
- D. MPO
Answer:
A
Explanation:
Definition of Fiber Connector Types:
LC (Lucent Connector): A small form-factor fiber optic connector with a push-pull latching
mechanism, commonly used for high-density applications.
SC (Subscriber Connector or Standard Connector): A larger form-factor connector with a push-pull
latching mechanism, often used in datacom and telecom applications.
ST (Straight Tip): A bayonet-style connector, typically used in multimode fiber optic networks.
MPO (Multi-fiber Push On): A connector designed to support multiple fibers (typically 12 or 24
fibers), used in high-density cabling environments.
Common Usage:
LC Connectors: Due to their small size, LC connectors are widely used in network interface cards
(NICs) and high-density environments such as data centers. They allow for more connections in a
smaller space compared to SC and ST connectors.
SC and ST Connectors: These are larger and more commonly used in patch panels and older fiber
installations but are less suitable for high-density applications.
MPO Connectors: Primarily used for trunk cables in data centers and high-density applications but
not typically on individual network interface cards.
Selection Criteria:
The small form-factor and high-density capabilities of LC connectors make them the preferred choice
for network interface cards, where space and connection density are critical considerations.
Reference:
CompTIA Network+ study materials on fiber optics and connector types.