comptia fc0-u71 practice test
CompTIA Tech+
Question 1
Which of the following is the most important consideration when opening a file on an OS GUI?
- A. File extension
- B. Default permissions
- C. Backup policy
- D. Data compression
Answer:
A
Explanation:
The file extension determines which application the OS uses to open the file in a GUI environment.
It's the key factor the OS checks to associate the file with the appropriate program (e.g., .docx with
Word, .jpg with an image viewer). The other options are relevant in broader contexts but not
immediately critical when simply opening a file.
Question 2
A database has the following schema: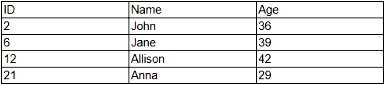
Which of the following is the number of records in the schema?
- A. 3
- B. 4
- C. 12
- D. 21
Answer:
B
Explanation:
Each row in the table (excluding the header row) represents a record in the database schema. The
table has 4 data rows (John, Jane, Allison, Anna), so the number of records is 4.
Question 3
Which of the following devices extends the range of a network?
- A. Modem
- B. Server
- C. Host firewall
- D. Access point
Answer:
D
Explanation:
An access point extends the range of a wireless network by allowing more devices to connect and by
covering additional physical areas. The other options serve different purposes:
● Modem connects to the internet,
● Server provides services,
● Host firewall protects a device but does not extend network range.
Question 4
A user receives a notification about a new software vulnerability. Which of the following is the best
way to secure the software?
- A. Configuring a firewall
- B. Applying updates
- C. Enabling authentication
- D. Uninstalling the program
Answer:
B
Explanation:
Applying updates (also called patching) is the most effective way to secure software after a
vulnerability is discovered. Vendors typically release patches that fix security flaws. While firewalls
and authentication add layers of protection, they do not directly fix vulnerabilities. Uninstalling the
program may not be practical or necessary.
Question 5
Which of the following is used to determine whether users accessed inappropriate online content?
- A. System logs
- B. Cookie data
- C. Location tracking
- D. Web browser history
Answer:
D
Explanation:
Web browser history shows the websites that a user has visited and is the most direct way to
determine if inappropriate online content was accessed.
Other options:
● System logs typically track system events,
● Cookie data stores session or site preferences,
● Location tracking shows physical location, not browsing activity.
Question 6
A company updates its password policy to require that all passwords be reset every 60 days. Which
of the following best describes this requirement?
- A. Password complexity
- B. Password management
- C. Password expiration
- D. Password privacy
Answer:
C
Explanation:
Password expiration refers to the requirement that passwords must be changed after a certain
period—in this case, every 60 days.
Other options:
● Password complexity involves rules about characters used,
● Password management is a broader concept including storage and retrieval,
● Password privacy refers to keeping passwords confidential.
Question 7
Which of the following encryption types protects data at rest?
- A. File-level
- B. VPN
- C. HTTPS
- D. Plaintext
Answer:
A
Explanation:
File-level encryption protects data at rest by encrypting files stored on a disk or drive, ensuring that
data is secure even when not actively being transmitted.
Other options:
● VPN and HTTPS protect data in transit,
● Plaintext offers no encryption or protection.
Question 8
Which of the following is the smallest storage unit?
- A. Petabyte
- B. Terabyte
- C. Kilobyte
- D. Megabyte
Answer:
C
Explanation:
In terms of size from smallest to largest: Kilobyte < Megabyte < Terabyte < Petabyte.
Question 9
A user lives in a remote area that does not have cabling or towers available. The user wants to
connect to the internet. Which of the flowing is the best solution?
- A. Fiber optic
- B. IDSL
- C. Cellular
- D. Satellite
Answer:
D
Explanation:
Satellite internet is ideal for remote areas without access to physical infrastructure like cabling or
cellular towers.
Other options:
● Fiber optic and DSL require physical lines,
● Cellular needs tower coverage, which may not be available in remote locations.
Question 10
Which of the following display types is bidirectional?
- A. DisplayPort
- B. VGA
- C. DVI
- D. USB-C
Answer:
D
Explanation:
USB-C supports bidirectional communication, meaning it can send and receive data (including video)
over the same connection.
DisplayPort, VGA, and DVI are primarily unidirectional display interfaces designed to send video from
a source to a display.
Question 11
A user needs to read documentation on a device while walking around outdoors in bright sunlight.
Which of the following is the best type of device for this purpose?
- A. Laptop
- B. Tablet
- C. E-reader
- D. ISmartphone
Answer:
C
Explanation:
E-readers use e-ink displays, which are highly readable in bright sunlight and have long battery life —
ideal for outdoor use.
Laptops, tablets, and smartphones often have glare or brightness issues in direct sunlight.
Question 12
A user attempts to log in to a website and receives a prompt to update their password. Which of the
following is this an example of?
- A. Password privacy
- B. Password history
- C. Password complexity
- D. Password expiration
Answer:
D
Explanation:
A prompt to update a password during login typically indicates that the password has expired based
on the system's policy.
Other options:
● Password history prevents reuse of old passwords,
● Password complexity sets rules for character requirements,
● Password privacy involves keeping the password confidential.
Question 13
Which of the following types of AI is used to edit images?
- A. Assistive
- B. Predictive
- C. Chatbot
- D. Generative
Answer:
D
Explanation:
Generative AI creates or modifies content, such as editing images, generating art, or producing
media.
Other options:
● Assistive AI supports tasks,
● Predictive AI forecasts outcomes,
● Chatbots simulate conversation but do not edit images.
Question 14
Given the following pseudocode:
<BODY>
<P>This is a paragraph.</P>
</BODY>
Which of the following best represents the type of language used by this code?
- A. Markup
- B. Query
- C. Compiled
- D. Scripting
Answer:
A
Explanation:
The code shown uses HTML tags like <BODY> and <P>, which are part of a markup language. Markup
languages describe the structure and presentation of text, not logic or computation.
Other options:
● Query languages retrieve data (e.g., SQL),
● Compiled languages are turned into machine code (e.g., C++),
● Scripting languages execute instructions (e.g., Python, JavaScript).
Question 15
Which of the following can be used to input commands for a computer to execute?
- A. Services
- B. Attributes
- C. Process
- D. Console
Answer:
D
Explanation:
A console (or command-line interface) allows users to input commands for the computer to execute
directly.
Other options:
● Services run background tasks,
● Attributes describe properties of objects,
● Process refers to a running program, not a command input method.