comptia cas-004 practice test
CompTIA Advanced Security Practitioner (CASP+) CAS-004
Question 1
A high-severity vulnerability was found on a web application and introduced to the enterprise. The vulnerability could allow an unauthorized user to utilize an open- source library to view privileged user information. The enterprise is unwilling to accept the risk, but the developers cannot fix the issue right away.
Which of the following should be implemented to reduce the risk to an acceptable level until the issue can be fixed?
- A. Scan the code with a static code analyzer, change privileged user passwords, and provide security training.
- B. Change privileged usernames, review the OS logs, and deploy hardware tokens.
- C. Implement MFA, review the application logs, and deploy a WAF.
- D. Deploy a VPN, configure an official open-source library repository, and perform a full application review for vulnerabilities.
Answer:
d
Reference:
https://www.microfocus.com/en-us/what-is/sast
Question 2
A company has instituted a new policy in which all outbound traffic must go over TCP ports 80 and 443 for all its managed mobile devices. No other IP traffic is allowed to be initiated from a device. Which of the following should the organization consider implementing to ensure internet access continues without interruption?
- A. CYOD
- B. MDM
- C. WPA3
- D. DoH
Answer:
d
Question 3
A Chief Information Officer (CIO) wants to implement a cloud solution that will satisfy the following requirements:
Support all phases of the SDLC.
Use tailored website portal software.
Allow the company to build and use its own gateway software.
Utilize its own data management platform.
Continue using agent-based security tools.
Which of the following cloud-computing models should the CIO implement?
- A. SaaS
- B. PaaS
- C. MaaS
- D. IaaS
Answer:
d
Reference:
https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
Question 4
A digital forensics expert has obtained an ARM binary suspected of including malicious behavior. The expert would like to trace and analyze the ARM binarys execution. Which of the following tools would BEST support this effort?
- A. objdump
- B. OllyDbg
- C. FTK Imager
- D. Ghidra
Answer:
b
Question 5
A host on a company's network has been infected by a worm that appears to be spreading via SMB. A security analyst has been tasked with containing the incident while also maintaining evidence for a subsequent investigation and malware analysis.
Which of the following steps would be best to perform FIRST?
- A. Turn off the infected host immediately.
- B. Run a full anti-malware scan on the infected host.
- C. Modify the smb.conf file of the host to prevent outgoing SMB connections.
- D. Isolate the infected host from the network by removing all network connections.
Answer:
d
Question 6
An organization collects personal data from its global customers. The organization determines how that data is going to be used, why it is going to be used, and how it is manipulated for business processes. Which of the following will the organization need in order to comply with GDPR? (Choose two.)
- A. Data processor
- B. Data custodian
- C. Data owner
- D. Data steward
- E. Data controller
- F. Data manager
Answer:
ae
Question 7
An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice.
Which of the following should the organization consider FIRST to address this requirement?
- A. Implement a change management plan to ensure systems are using the appropriate versions.
- B. Hire additional on-call staff to be deployed if an event occurs.
- C. Design an appropriate warm site for business continuity.
- D. Identify critical business processes and determine associated software and hardware requirements.
Answer:
c
Reference:
https://searchdisasterrecovery.techtarget.com/definition/warm-site
Question 8
A security engineer thinks the development team has been hard-coding sensitive environment variables in its code.
Which of the following would BEST secure the company's CI/CD pipeline?
- A. Utilizing a trusted secrets manager
- B. Performing DAST on a weekly basis
- C. Introducing the use of container orchestration
- D. Deploying instance tagging
Answer:
a
Reference:
https://about.gitlab.com/blog/2021/04/09/demystifying-ci-cd-variables/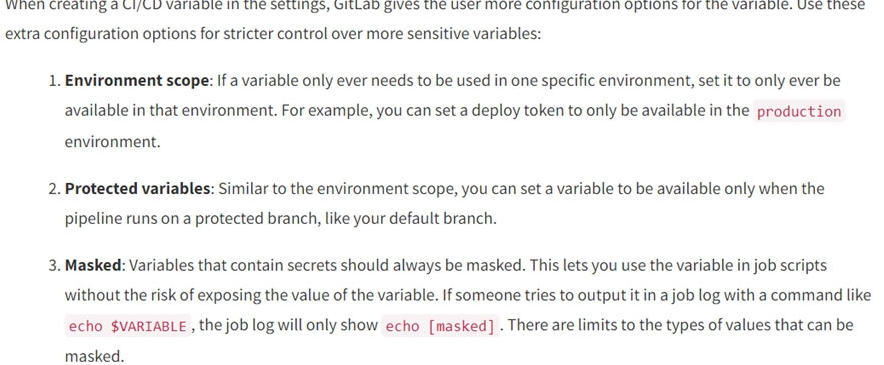
Question 9
A security engineer is reviewing a record of events after a recent data breach incident that involved the following:
A hacker conducted reconnaissance and developed a footprint of the companys Internet-facing web application assets.
A vulnerability in a third-party library was exploited by the hacker, resulting in the compromise of a local account.
The hacker took advantage of the accounts excessive privileges to access a data store and exfiltrate the data without detection.
Which of the following is the BEST solution to help prevent this type of attack from being successful in the future?
- A. Dynamic analysis
- B. Secure web gateway
- C. Software composition analysis
- D. User behavior analysis
- E. Stateful firewall
Answer:
c
Question 10
A recent data breach revealed that a company has a number of files containing customer data across its storage environment. These files are individualized for each employee and are used in tracking various customer orders, inquiries, and issues. The files are not encrypted and can be accessed by anyone. The senior management team would like to address these issues without interrupting existing processes.
Which of the following should a security architect recommend?
- A. A DLP program to identify which files have customer data and delete them
- B. An ERP program to identify which processes need to be tracked
- C. A CMDB to report on systems that are not configured to security baselines
- D. A CRM application to consolidate the data and provision access based on the process and need
Answer:
c
Reference:
https://searchdatacenter.techtarget.com/definition/configuration-management-database#:~:text=A%20configuration%20management%20database%
20(CMDB,the%20relationships%20between%20those%20components