cisco 352-001 practice test
ccde design written
Question 1
You are hired to design a solution that will improve network availability for users on a campus network with routed access. If the budget limits you to three components, which three components would you recommend in your design proposal? (Choose three.)
- A. redundant power supplies in the access routers
- B. standby route processors for SSO in the core routers
- C. standby route processors for SSO in the distribution routers
- D. standby route processors for SSO in the access routers
- E. replace copper links between devices with fiber links
Answer:
ade
Question 2
A service provider is offering a QoS-based transport service. Three classes have been defined in the core, including an Expedited Forwarding (EF) class for VoIP traffic. Which tool should be used at the ingress for the EF class?
- A. policing
- B. shaping
- C. WRED
- D. CB-WFQ
Answer:
a
Question 3
Company X will be integrating an IPv6 application into their network and wants to develop a test environment to evaluate application performance across the network. This application will require both unicast and multicast communications. The company can do this implementation only in certain areas of its existing
IPv4-only network, but wants all areas to communicate with each other. When developing the design to provide connectivity between these testing locations, what tunneling technology would work in this scenario?
- A. ISATAP
- B. 6to4
- C. DMVPN
- D. 6vPE
- E. 6PE
Answer:
c
Question 4
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during
TCN in a Layer 2 switched network with many VLANs?
- A. STP
- B. MST
- C. PVRSTP
- D. PVSTP+
Answer:
d
Question 5
Refer to the exhibit. The design is being proposed for use within the network. The CE devices are
OSPF graceful restart-capable, and the core devices are OSPF graceful restart-aware. The WAN advertisements received from BGP are redistributed into OSPF.
A forwarding supervisor failure event takes place on CE A. During this event, how will the routes learned from the WAN be seen on the core devices?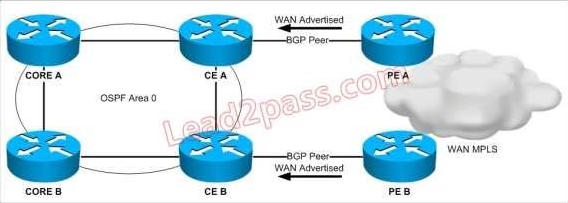
- A. via CE A and CE B
- B. via CE A
- C. via CE B
- D. no WAN routes will be accessible
Answer:
c
Question 6
Refer to the exhibit. Your junior design engineer presents this configuration design. What is the next-hop router for CE3, and why?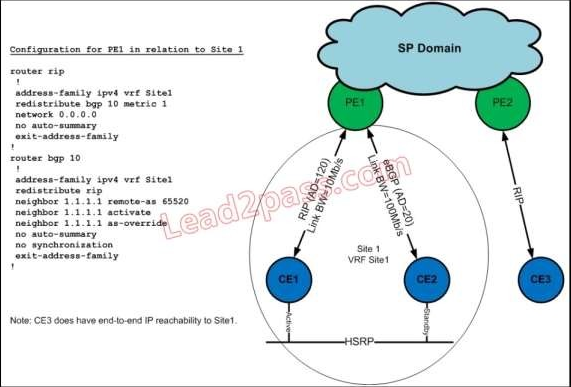
- A. CE1. BGP weight is higher than CE2.
- B. CE2. EBGP administrative distance is lower than RIP.
- C. CE2. The link between CE2 and PE1 has more bandwidth than CE1-to-PE1.
- D. CE1. HSRP on CE1 is in active state.
Answer:
a
Question 7
Two MPLS service providers (SP1 and SP2) are offering inter-provider RFC 2547/4364-based IP-VPN service to an enterprise customer. IP traffic among some of the customer's sites has to traverse both of the service providers. The service providers and the enterprise do not know what the minimum MTU is along the end- to-end path.
What could be done to guarantee that large packets are not dropped for MTU-related reasons?
- A. enable Path MTU Discovery on all devices within SP1 and SP2
- B. enable Path MTU Discovery on all devices within the enterprise
- C. configure the IP sender or senders to set the DF flag in the IP header
- D. configure the IP sender or senders to clear the DF flag in the IP header
Answer:
b
Question 8
FIFO queuing is being used on all routers in a network. The primary application running on the network is data backup using FTP. At certain times, users experience cyclical performance degradation.
What two things might mitigate this problem and help ensure bandwidth is used effectively in the network? (Choose two.)
- A. traffic shaping
- B. CB-WFQ
- C. traffic policing
- D. WRED
- E. MDRR
Answer:
bd
Question 9
You are designing the QoS features for a large enterprise network that includes DMVPN. When would you need to configure QoS preclassify?
- A. when you are marking packets with the DSCP bits
- B. when you are marking packets with the TOS bits
- C. when your service provider requires the DSCP bits be set
- D. when the QoS policy cannot be based on DSCP ToS bits
Answer:
d
Question 10
Refer to the exhibit. All routers in this network are configured to place all interfaces in OSPF area 5. R3 is the designated router on the 10.1.5.0/24 network. If you examine the OSPF database on R4, what would the network (type 2) LSA, generated by R3, contain?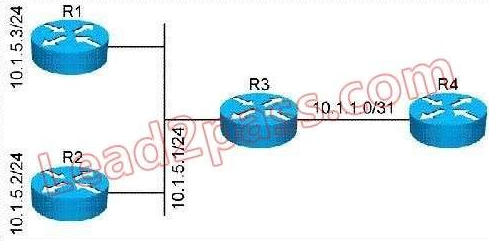
- A. a connection to 10.1.5.0/24 and links to R3, R2, and R1
- B. a connection to 10.1.5.0/24 and links to R2 and R1
- C. connections to 10.1.5.0/24 and 10.1.1.0/31
- D. no connections, R3 does not generate a network (type 2) LSA in this network
Answer:
a