cisco 350-701 practice test
Implementing and Operating Cisco Security Core Technologies
Question 1 Topic 1
Topic 1
Which functions of an SDN architecture require southbound APIs to enable communication?
- A. SDN controller and the network elements
- B. management console and the SDN controller
- C. management console and the cloud
- D. SDN controller and the cloud
Answer:
A
Question 2 Topic 1
Topic 1
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.)
- A. put
- B. options
- C. get
- D. push
- E. connect
Answer:
A C
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
Question 3 Topic 1
Topic 1
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a
network?
- A. SDN controller and the cloud
- B. management console and the SDN controller
- C. management console and the cloud
- D. SDN controller and the management solution
Answer:
D
Question 4 Topic 1
Topic 1
What is a feature of the open platform capabilities of Cisco DNA Center?
- A. application adapters
- B. domain integration
- C. intent-based APIs
- D. automation adapters
Answer:
C
Question 5 Topic 1
Topic 1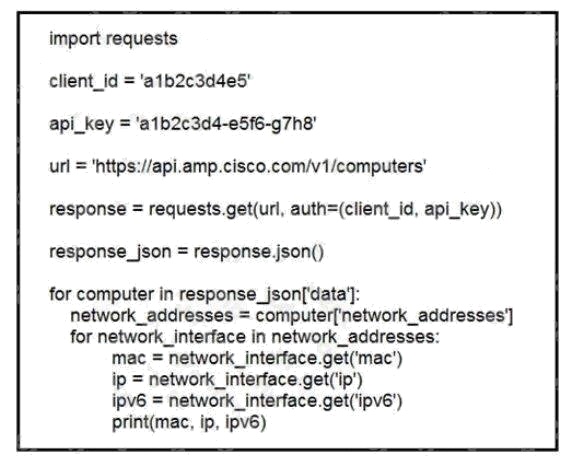
Refer to the exhibit. What does the API do when connected to a Cisco security appliance?
- A. create an SNMP pull mechanism for managing AMP
- B. gather network telemetry information from AMP for endpoints
- C. get the process and PID information from the computers in the network
- D. gather the network interface information about the computers AMP sees
Answer:
D
Question 6 Topic 1
Topic 1
Which form of attack is launched using botnets?
- A. TCP flood
- B. DDOS
- C. DOS
- D. virus
Answer:
B
Question 7 Topic 1
Topic 1
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
- A. smurf
- B. distributed denial of service
- C. cross-site scripting
- D. rootkit exploit
Answer:
C
Question 8 Topic 1
Topic 1
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
- A. user input validation in a web page or web application
- B. Linux and Windows operating systems
- C. database
- D. web page images
Answer:
C
Explanation:
Reference: https://tools.cisco.com/security/center/resources/sql_injection
Question 9 Topic 1
Topic 1
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. A spear phishing campaign is aimed at a specific person versus a group of people.
- C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Answer:
B
Question 10 Topic 1
Topic 1
Which two behavioral patterns characterize a ping of death attack? (Choose two.)
- A. The attack is fragmented into groups of 16 octets before transmission.
- B. The attack is fragmented into groups of 8 octets before transmission.
- C. Short synchronized bursts of traffic are used to disrupt TCP connections.
- D. Malformed packets are used to crash systems.
- E. Publicly accessible DNS servers are typically used to execute the attack.
Answer:
B D
Explanation:
Reference: https://en.wikipedia.org/wiki/Ping_of_death
Question 11 Topic 1
Topic 1
Which two mechanisms are used to control phishing attacks? (Choose two.)
- A. Enable browser alerts for fraudulent websites.
- B. Define security group memberships.
- C. Revoke expired CRL of the websites.
- D. Use antispyware software.
- E. Implement email filtering techniques.
Answer:
A E
Question 12 Topic 1
Topic 1
Which attack is commonly associated with C and C++ programming languages?
- A. cross-site scripting
- B. water holing
- C. DDoS
- D. buffer overflow
Answer:
D
Explanation:
Reference: https://en.wikipedia.org/wiki/Buffer_overflow
Question 13 Topic 1
Topic 1
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.)
- A. Check integer, float, or Boolean string parameters to ensure accurate values.
- B. Use prepared statements and parameterized queries.
- C. Secure the connection between the web and the app tier.
- D. Write SQL code instead of using object-relational mapping libraries.
- E. Block SQL code execution in the web application database login.
Answer:
A B
Explanation:
Reference: https://en.wikipedia.org/wiki/SQL_injection
Question 14 Topic 1
Topic 1
Which two kinds of attacks are prevented by multifactor authentication? (Choose two.)
- A. phishing
- B. brute force
- C. man-in-the-middle
- D. DDOS
- E. tear drop
Answer:
B C
Question 15 Topic 1
Topic 1
What are two rootkit types? (Choose two.)
- A. registry
- B. buffer mode
- C. user mode
- D. bootloader
- E. virtual
Answer:
C D