cisco 350-501 practice test
implementing and operating cisco service provider network core technologies (spcor)
Question 1
Which core component of MDT describes the data that an MDT-capable device streams to a collector?
- A. sensor path
- B. encoder
- C. transport protocol
- D. subscription
Answer:
d
Question 2
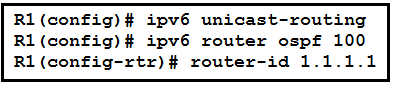
Refer to the exhibit. An engineer is configuring router R1 for OSPFv3 as shown. Which additional configuration must be performed so that the three active interfaces on the router will advertise routes and participate in OSPF IPv6 processes?
A.
B.
C.
D.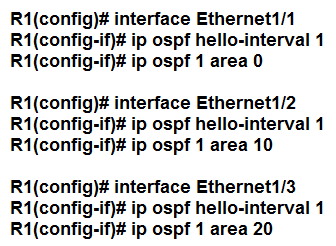
Answer:
c
Question 3

Refer to the exhibits. Which information is provided for traceback analysis when this configuration is applied?
- A. source interface
- B. packet size distribution
- C. IP sub flow cache
- D. BGP version
Answer:
c
Question 4
A router RP is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization message to a neighbor to establish an LDP session? (Choose three.)
- A. Learn from Neighbor (N) flag, set to 1
- B. Recovery Time field
- C. Type-9 LSA
- D. Reconnect Timeout field
- E. Graceful restart capability in OPEN message
- F. Learn from Network (L) flag, set to 1
Answer:
bdf
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_ha/configuration/xe-16-8/mp-ha-xe-16-8-book/nsf-sso-mpls-ldp-and-ldp-graceful-restart.html
Question 5
You are creating new Cisco MPLS TE tunnels. Which type of RSVP message does the headend router send to reserve bandwidth on the path to the tailend router?
- A. path
- B. tear
- C. error
- D. reservation
Answer:
a
Reference:
https://packetpushers.net/rsvp-te-protocol-deep-dive/
Question 6
DRAG DROP Drag and drop the functions from the left onto the correct Path Computation Element Protocol roles on the right.
Select and Place: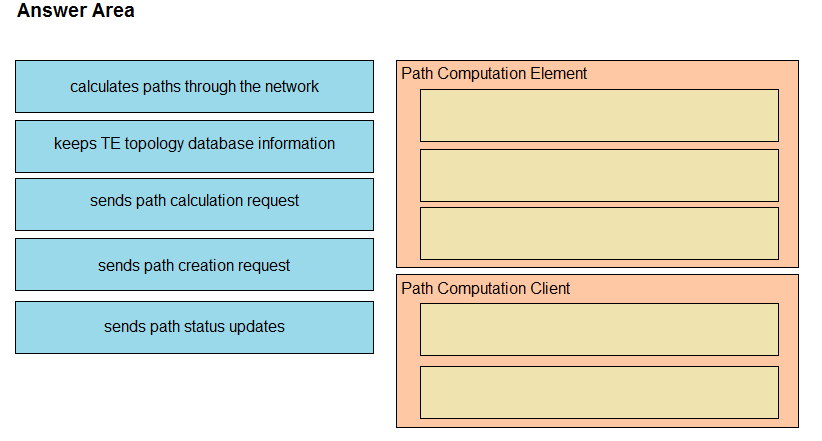
Answer:
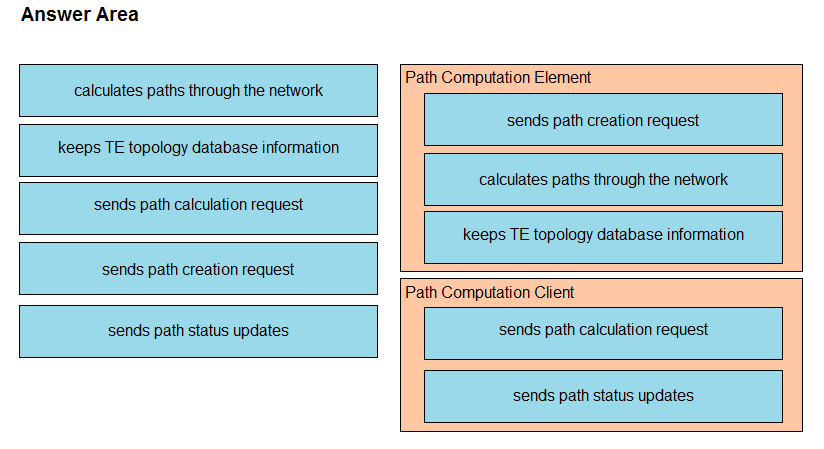
Question 7
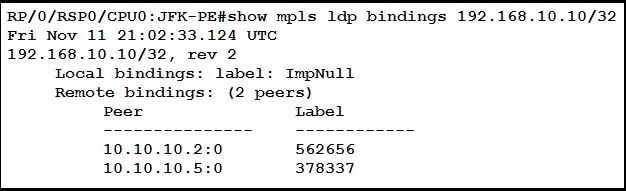
Refer to the exhibit. After implementing a new design for the network, a technician reviews the pictures CLI output as part of the MOP.
Which two elements describe what the technician can ascertain from the ImpNull output? (Choose two.)
- A. Ultimate Hop Popping is in use for the prefix displayed.
- B. Penultimate Hop Popping is in use for the prefix displayed.
- C. Label 0 is used for the prefix displayed, but will not be part of the MPLS label stack for packets destined for 192.168.10.10.
- D. Label 3 is in use for the prefix displayed and will be part of the MPLS label stack for packets destined for 192.168.10.10.
- E. Label 0 is used for the prefix displayed and will be part of the MPLS label stack for packets destined for 192.168.10.10.
Answer:
bd
Question 8
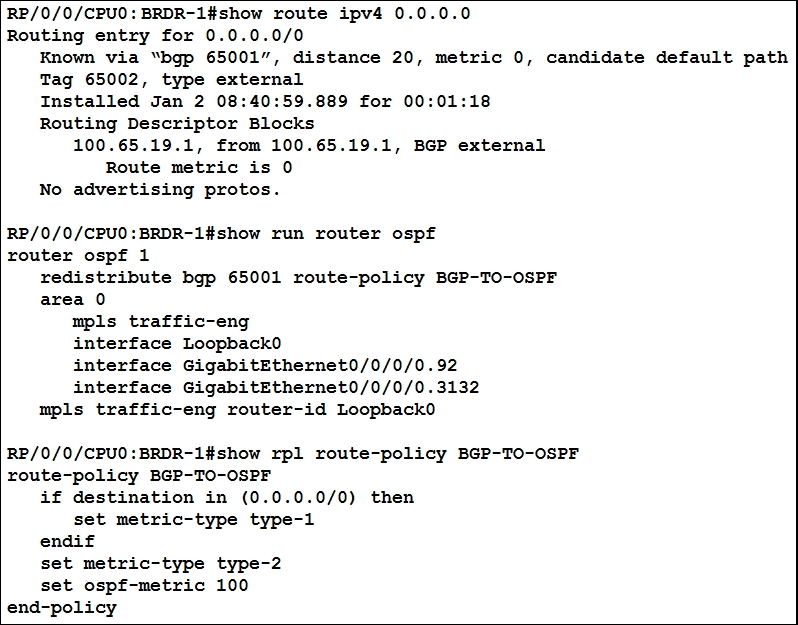
Refer to the exhibit. Router BRDR-1 is configured to receive the 0.0.0.0/0 and 172.17.1.0/24 networks via BGP and advertise them into OSPF area 0. An engineer has noticed that the OSPF domain is receiving only the 172.17.1.0/24 route and default route 0.0.0.0/0 is still missing. Which configuration must an engineer apply to resolve the problem?
- A. router ospf 1 redistribute bgp 65001 metric 100 route-policy BGP-TO-OSPF end
- B. router ospf 1 default-information originate end
- C. router ospf 1 default-metric 100 end
- D. router ospf 1 default-information originate always end
Answer:
b
Question 9
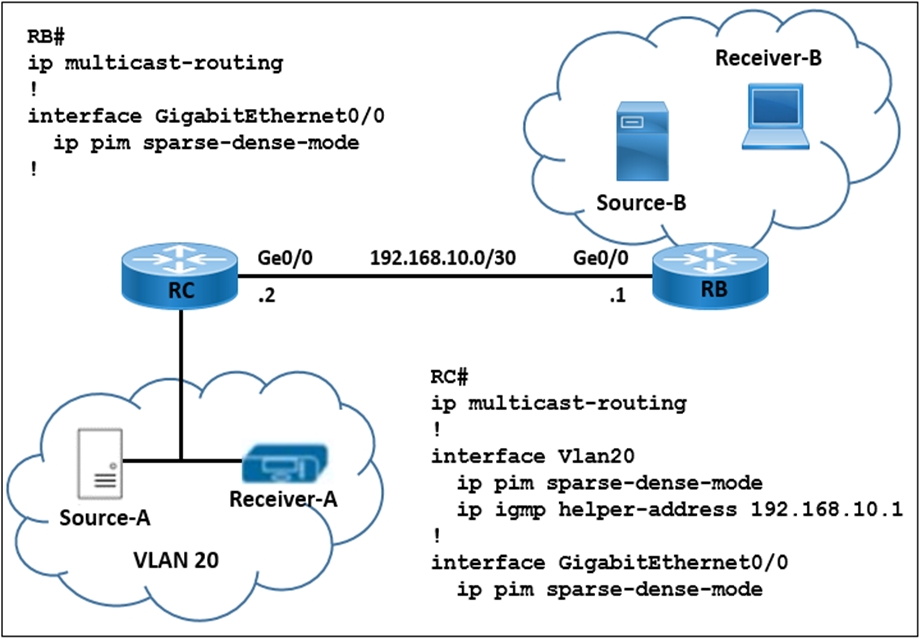
Refer to the exhibit. A network engineer is implementing multicast Source-A to send a multicast stream for Receiver-A, and multicast Source-B to send a multicast stream for Receiver-B. Router RC forwards the IGMP host a report and leaves messages to IP address 192.168.10.1. How must the multicast features be implemented to prevent RB from receiving multicast flooding from Source-A?
- A. Change the helper-address value to 192.168.10.2 on RC.
- B. Enable ip pim neighbor-filter on RC interface Ge0/0.
- C. Configure PIM-SSM on RB and RC interface Ge 0/0.
- D. Enable ip pim passive on RB interface Ge0/0.
Answer:
d
Question 10
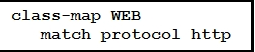
Refer to the exhibit. Which statement describes the effect of this configuration?
- A. It matches HTTP traffic for use in a policy map.
- B. It applies a service policy to all interfaces remarking HTTP traffic.
- C. It creates an ACL named WEB that filters HTTP traffic.
- D. It modifies the default policy map to allow all HTTP traffic through the router.
Answer:
a