cisco 350-401 practice test
Implementing Cisco Enterprise Network Core Technologies (ENCOR)
Question 1
Which protocol does Cisco Catalyst SD-WAN use to protect control plane communication?
- A. OMP
- B. STUN
- C. DTLS
- D. IPsec
Answer:
C
Question 2
In which two ways does PIM dense mode function in the network? (Choose two.)
- A. It waits to forward multicast traffic until a downstream router requests the traffic.
- B. It utilizes the designated forwarder election to avoid multicast packet loops.
- C. It receives traffic from only one Reverse Path Forwarding interface.
- D. It forwards multicast traffic on all interfaces until a downstream router requests that forwarding stop.
- E. It uses a push method, and fallback occurs when RP information is lost.
Answer:
A,D
Question 3
Which characteristic applies to the endpoint security aspect of the Cisco Threat Defense
architecture?
- A. detect and block ransomware in email attachments
- B. cloud-based analysis of threats
- C. outbound URL analysis and data transfer controls
- D. user context analysis
Answer:
D
Question 4
Refer to the exhibit. A customer reports occasional brief audio dropouts on its Cisco Wi-Fi phones.
The environment consists of a Cisco Catalyst 9800 Series WLC with Catalyst 9120 APs running RRM.
The phones connect on the 5-GHz band. Which action resolves this issue?
- A. Enable Media Stream Multicast-direct.
- B. Disable Coverage Hole Detection.
- C. Set WMM Policy to Required.
- D. Enable Defer Priority 6.
Answer:
C
Question 5
Why is a Type 1 hypervisor more efficient than a Type 2 hypervisor?
- A. Type 1 hypervisor is the only type of hypervisor that supports hardware acceleration techniques.
- B. Type 1 hypervisor runs directly on the physical hardware of the host machine without relying on the underlying OS.
- C. Type 1 hypervisor enables other operating systems to run on it.
- D. Type 1 hypervisor relies on the existing OS of the host machine to access CPU, memory, storage, and network resources.
Answer:
B
Question 6
Refer to the exhibit.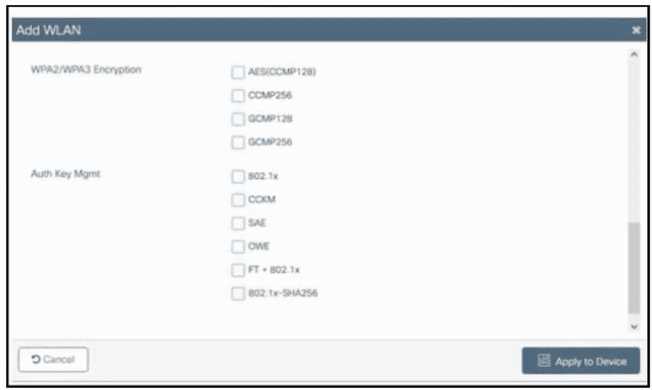
Refer to the exhibit. A customer asks an engineer to create a new secure WLAN to support only
WPA3. Users must connect using a passphrase. Which encryption and key management
configuration is required?
- A. CCMP256 encryption with CCKM key management
- B. GCMP128 encryption with OWE key management
- C. CCMP128 encryption with SAE key management
- D. GCMP256 encryption with 802.1x key management
Answer:
C
Question 7
Refer to the exhibit.
Refer to the exhibit. What is displayed when the code is run?
- A. The answer is 5
- B. The answer is 25
- C. The answer is 100
- D. The answer is 70
Answer:
B
Question 8
Refer to the exhibit.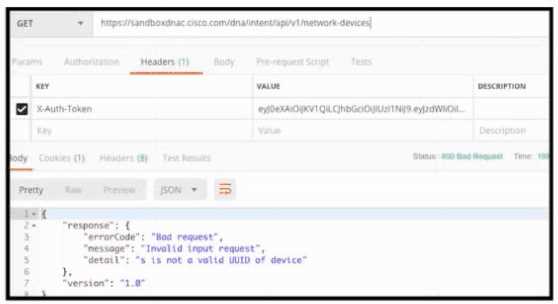
Refer to the exhibit. POSTMAN is showing an attempt to retrieve network device information from
Cisco Catalyst Center (formerly DNA Center) API. What is the issue?
- A. The token has expired
- B. The URI string is incorrect
- C. Authentication has failed
- D. The JSON payload contains the incorrect UUID
Answer:
D
Question 9
DRAG DROP
Drag and drop the Cisco Catalyst Center (formerly DNA Center) northbound API characteristics from
the left to the right. Not all options are used.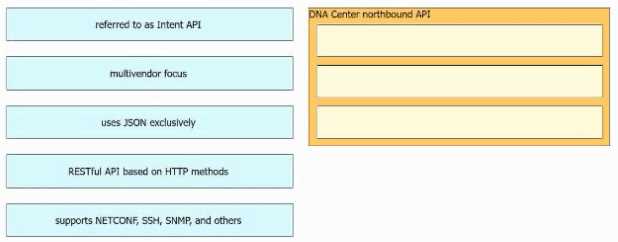
Answer:
Explanation:
Question 10
In a Cisco SD-Access wireless architecture, which device manages endpoint ID to edge node
bindings?
- A. fabric control plane node
- B. fabric edge node
- C. fabric border node
- D. fabric wireless controller
Answer:
A
Question 11
Refer to the exhibit.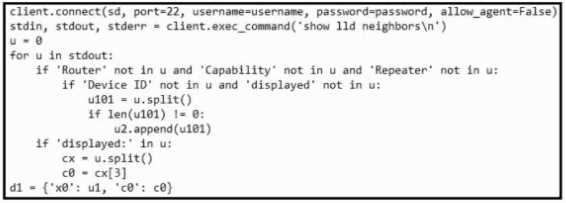
Refer to the exhibit. What is achieved by this Python script?
- A. It displays the output from show lldp neighbors into a standard output.
- B. It reads the neighbor count from show lldp neighbors into a dictionary list.
- C. It displays the Layer 3 neighbors from show lldp neighbors on the terminal screen.
- D. It reads the output from show lldp neighbors into an array object.
Answer:
B
Question 12
Which design principle states that a user has no access by default to any resource, and unless a
resource is explicitly granted, it should be denied?
- A. economy of mechanism
- B. fail-safe defaults
- C. complete mediation
- D. least privilege
Answer:
B
Question 13
DRAG DROP
Refer to the exhibit.
Refer to the exhibit. Drag and drop the snippets into the RESTCONF request to form the request that
returns this response. Not all options are used.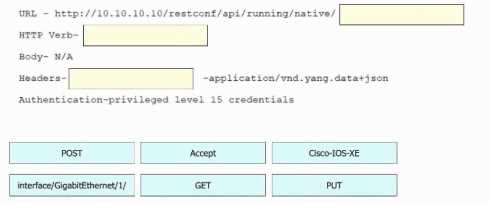
Answer:
Explanation: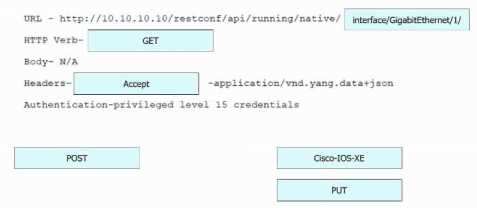
Question 14
When using a Cisco Catalyst 9800 Series WLC, which tag/profile can be applied to APs to change the
mode to FlexConnect in a specific location?
- A. policy tag
- B. site tag
- C. AP join profile
- D. flex profile
Answer:
B
Question 15
What is the role of the vSmart controller in a Cisco Catalyst SD-WAN environment?
- A. It is the centralized network management system.
- B. It manages the data plane.
- C. It manages the control plane.
- D. It performs authentication and authorization.
Answer:
C