cisco 350-201 practice test
performing cyberops using core security technologies (cbrcor)
Question 1
An engineer wants to review the packet overviews of SNORT alerts. When printing the SNORT alerts, all the packet headers are included, and the file is too large to utilize. Which action is needed to correct this problem?
- A. Modify the alert rule to output alert_syslog: output log
- B. Modify the output module rule to output alert_quick: output filename
- C. Modify the alert rule to output alert_syslog: output header
- D. Modify the output module rule to output alert_fast: output filename
Answer:
a
Reference:
https://snort-org-site.s3.amazonaws.com/production/document_files/files/000/000/249/original/snort_manual.pdf?X-Amz-Algorithm=AWS4-HMAC-
SHA256&X-Amz-Credential=AKIAIXACIED2SPMSC7GA%2F20201231%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20201231T141156Z&X-Amz-
Expires=172800&X-Amz-SignedHeaders=host&X-Amz-Signature=e122ab6eb1659e13b3bc6bb2451ce693c0298b76c1962c3743924bc5fd83d382
Question 2
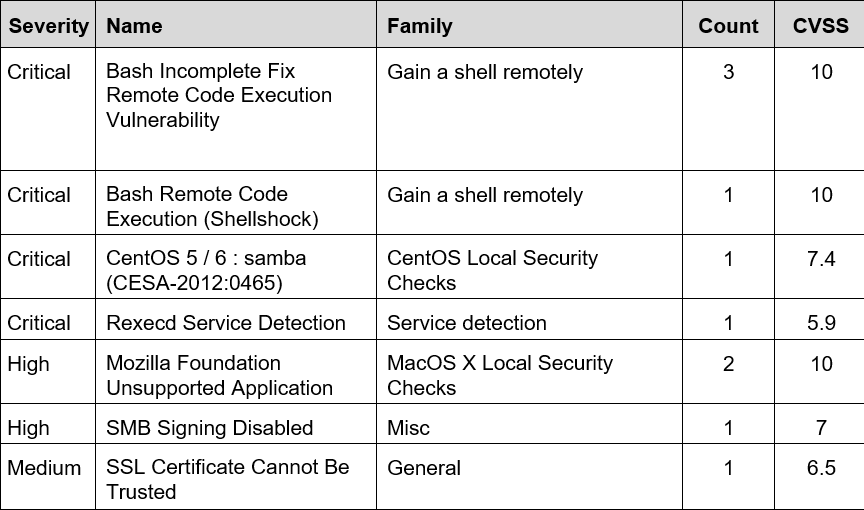
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
- A. Evaluate service disruption and associated risk before prioritizing patches.
- B. Perform root cause analysis for all detected vulnerabilities.
- C. Remediate all vulnerabilities with descending CVSS score order.
- D. Temporarily shut down unnecessary services until patch deployment ends.
Answer:
b
Question 3
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
- A. IaaS
- B. PaaS
- C. DaaS
- D. SaaS
Answer:
a
Question 4
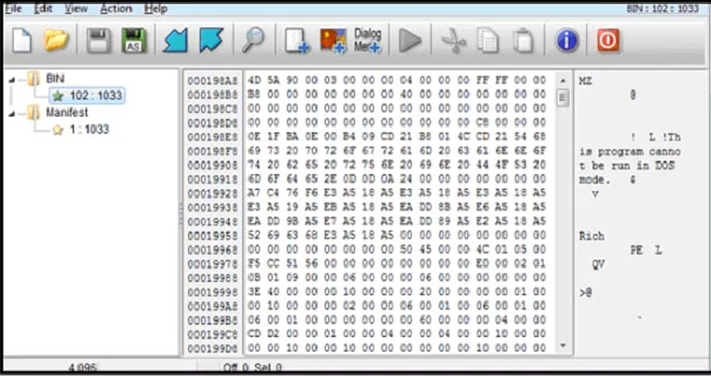
Refer to the exhibit. An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
- A. a DOS MZ executable format
- B. a MS-DOS executable archive
- C. an archived malware
- D. a Windows executable file
Answer:
d
Reference:
https://stackoverflow.com/questions/2577545/why-is-this-program-cannot-be-run-in-dos-mode-text-present-in-dll-files#:~:text=The%20linker%20places
%20a%20default,using%20the%20%2FSTUB%20linker%20option.&text=This%20information%20enables%20Windows%20to,has%20an%20MS-DOS%20stub
.
Question 5
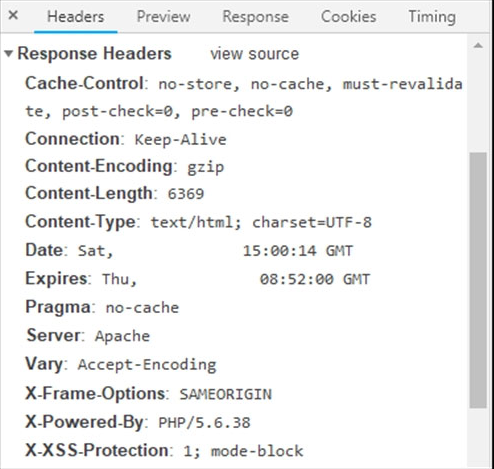
Refer to the exhibit. Where are the browser page rendering permissions displayed?
- A. X-Frame-Options
- B. X-XSS-Protection
- C. Content-Type
- D. Cache-Control
Answer:
c
Question 6
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
- A. Perform a vulnerability assessment
- B. Conduct a data protection impact assessment
- C. Conduct penetration testing
- D. Perform awareness testing
Answer:
b
Reference:
https://apdcat.gencat.cat/web/.content/03-documentacio/Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
Question 7
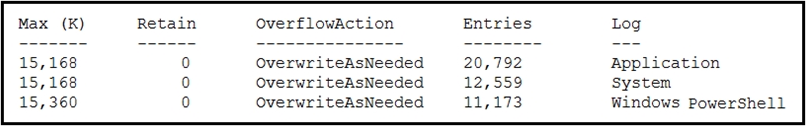
Refer to the exhibit. An employee is a victim of a social engineering phone call and installs remote access software to allow an `MS Support` technician to check his machine for malware. The employee becomes suspicious after the remote technician requests payment in the form of gift cards. The employee has copies of multiple, unencrypted database files, over 400 MB each, on his system and is worried that the scammer copied the files off but has no proof of it. The remote technician was connected sometime between 2:00 pm and 3:00 pm over https. What should be determined regarding data loss between the employee's laptop and the remote technician's system?
- A. No database files were disclosed
- B. The database files were disclosed
- C. The database files integrity was violated
- D. The database files were intentionally corrupted, and encryption is possible
Answer:
c
Question 8
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization's service area. What are the next steps the engineer must take?
- A. Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
- B. Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
- C. Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
- D. Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
Answer:
a
Question 9
DRAG DROP Drag and drop the function on the left onto the mechanism on the right.
Select and Place: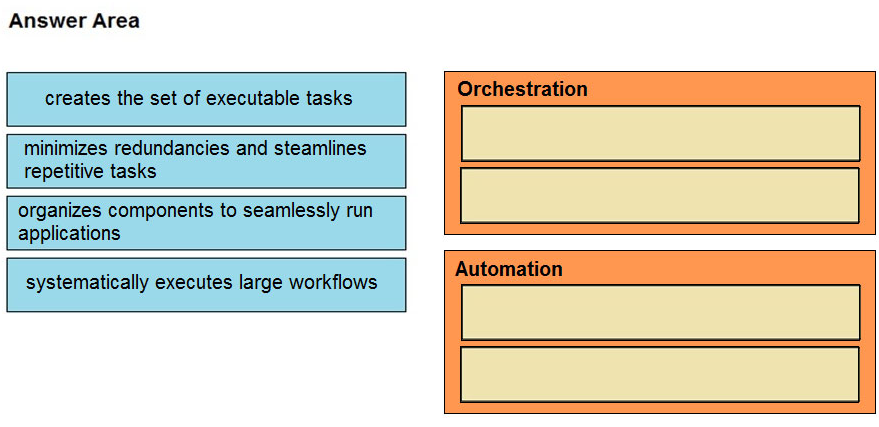
Answer:
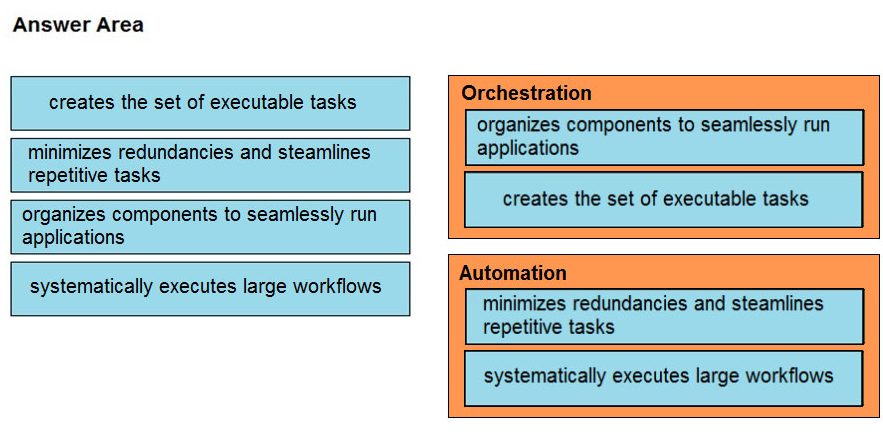
Question 10
A logistic company must use an outdated application located in a private VLAN during the migration to new technologies. The IPS blocked and reported an unencrypted communication. Which tuning option should be applied to IPS?
- A. Allow list only authorized hosts to contact the application's IP at a specific port.
- B. Allow list HTTP traffic through the corporate VLANS.
- C. Allow list traffic to application's IP from the internal network at a specific port.
- D. Allow list only authorized hosts to contact the application's VLAN.
Answer:
d