cisco 300-910 practice test
implementing devops solutions and practices using cisco platforms (devops)
Question 1
What are two advantages of using Configuration Management Tools? (Choose two.)
- A. reduction in policy violations caused by human errors
- B. reduction in administration costs
- C. reduction in network changes already performed automatically
- D. reduction of on-premises networking equipment
- E. reduction in networking team skills
Answer:
bc
Question 2
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
- A. Apply
- B. Install
- C. Deploy
- D. Create
- E. Expose
Answer:
ae
Question 3
A precheck validation is being designed for the network state in a Cl/CD pipeline This design requires:
the CI/CD pipeline to spin up test instances.
instances must be used to validate changes.
changes must be validated prior to a continuous deployment workflow, and
then push the changes to production
How should the pipeline target the required environment?
- A. Use separate CI servers for each environment
- B. Use different pipelines for each environment
- C. Use separate Git repositories for each environment
- D. Use different inventory files for each environment
Answer:
d
Question 4
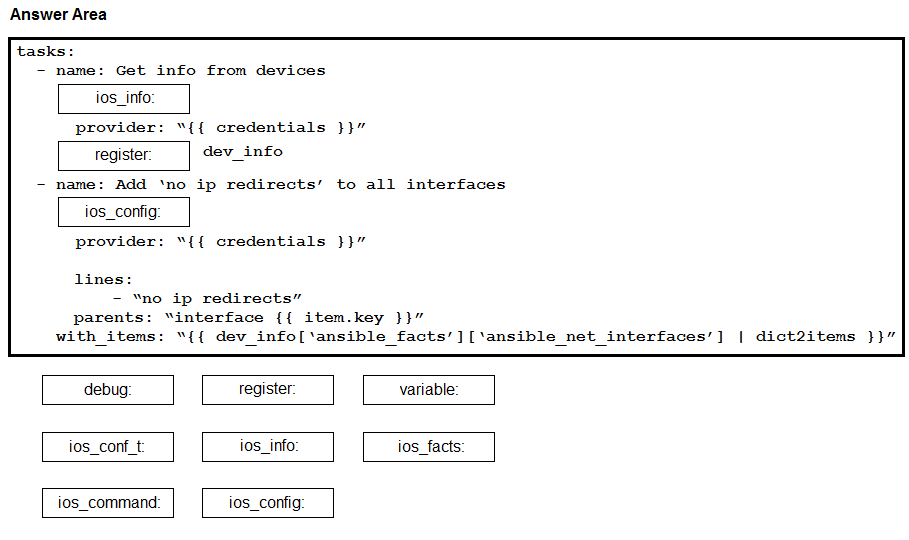
DRAG DROP Construct an Ansible script to gather information about target routers and then use it to apply no ip redirects to every interface on each device. Drag and drop the code from the bottom onto the correct location in the exhibit to complete the tasks section of the Ansible playbook so that it accomplishes your goal.
Select and Place: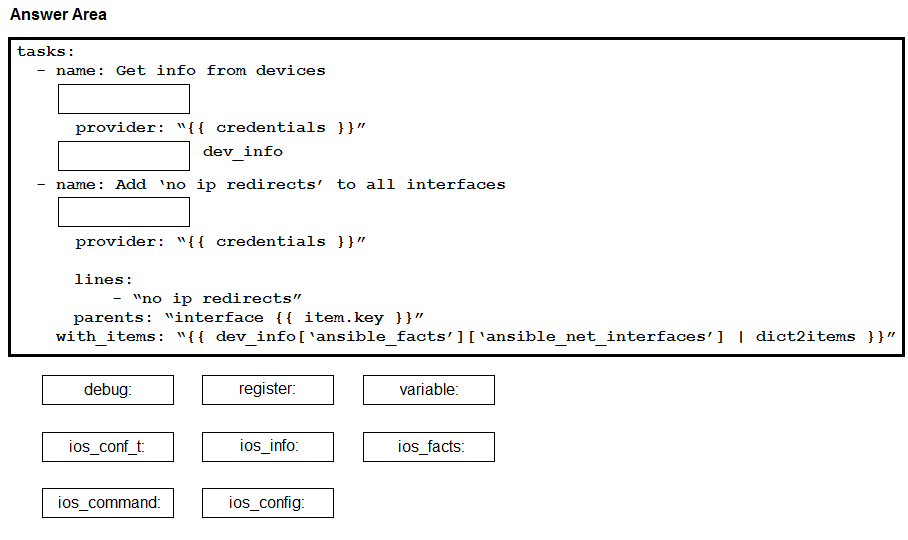
Answer:
Question 5
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?
- A. EXPOSE 8080
- B. FIREWALL ADD-PORT 8080
- C. PORT 8080
- D. OPEN PORT 8080
Answer:
a
Question 6
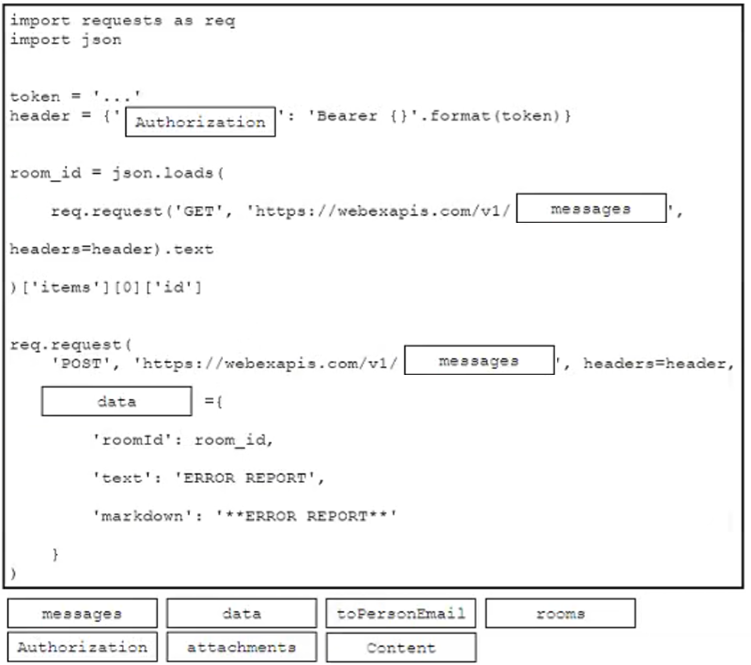
DRAG DROP
Drag and drop the code from the bottom onto the box where the code is missing to post a message to a Cisco Webex space. Not all options are used.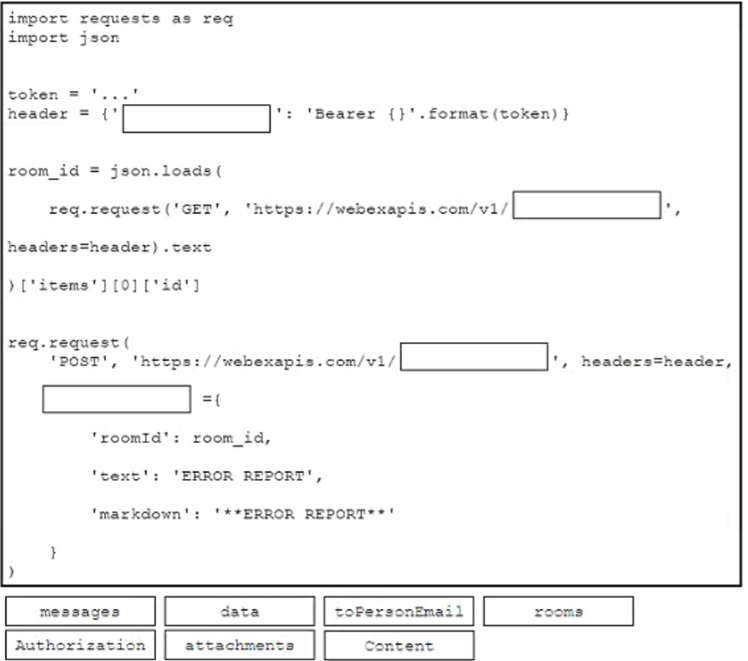
Answer:
Question 7
DRAG DROP
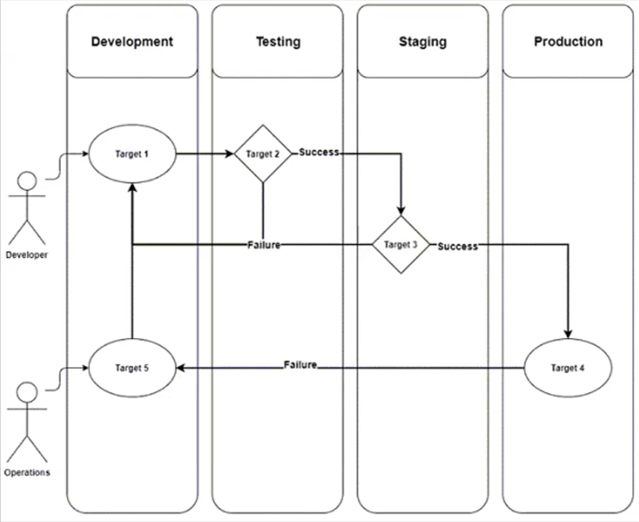
Refer to the exhibit. A development team is designing an application that will include multiple components and services. To streamline the process, CO/CD must be implemented.
Drag and drop the CI/CD pipeline stages from the left onto the targets on the right.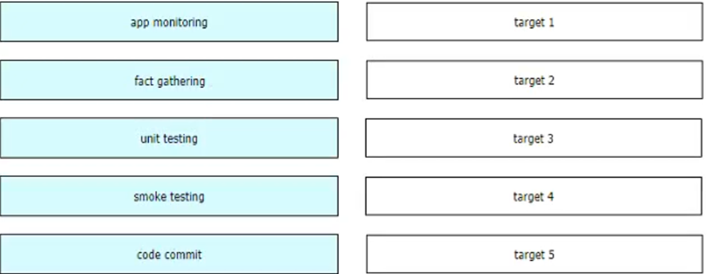
Answer:
Question 8
Which two actions help limit the attack surface of your Docker container? (Choose two.)
- A. Run only a single service in each container.
- B. Run all services in a single image.
- C. Use version tags for base images and dependencies.
- D. Use Kali Linux as a base image.
- E. Download images over HTTPS supporting sites.
Answer:
ce
Question 9
A DevOps engineer has built a container to host a web-server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?
-
A.
ENTRYPOINT
- B. ENTRYPOINT ["/usr/sbin/apache2ctl", "-D", "FOREGROUND"]
- C. ENTRYPOINT ["BACKGROUND", "-D", "/usr/sbin/apache2ctl"]
- D. ENTRYPOINT {usr/sbin/apache2ctl}
Answer:
b
Question 10
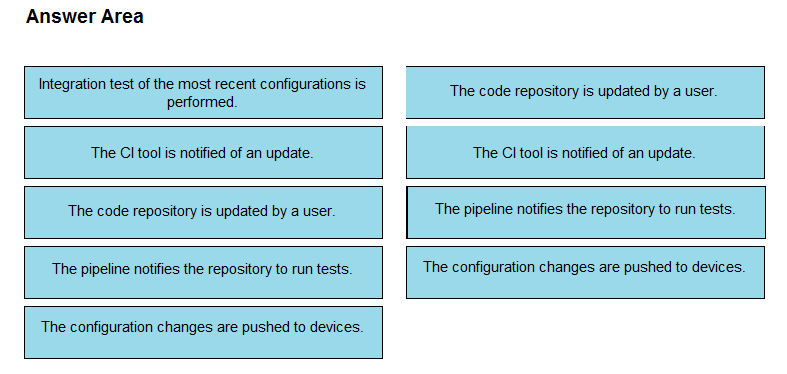
DRAG DROP The IaC configuration for an application is being deployed using a CI/CD pipeline. Drag and drop the steps for this pipeline from the left into the correct order that they would be executed on the right. Not all options are used.
Select and Place: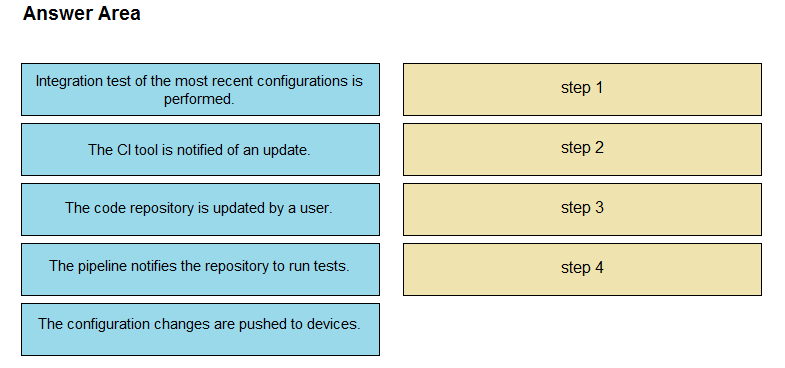
Answer: