cisco 300-910 practice test
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)
Question 1
DRAG DROP
Refer to the Exhibit.
The IaC configuration for an application is being deployed using a CI/CD pipeline. Drag and drop the
steps for this pipeline from the left into the correct order that they would be executed on the right.
Not all options are used.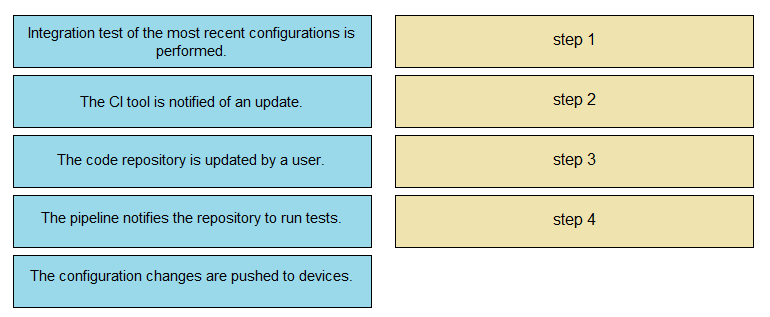
Answer:
Explanation:
- The code repository is updated by a user.
- The CI tool is notified of an update.
- Integration test of the most recent configurations is performed
- The configuration changes are pushed to devices.
Question 2
A DevOps engineer must validate the working state of the network before implementing a CI/CD
pipeline model. Which configuration management tool is designed to accomplish this?
- A. Jenkins
- B. Genie CLI
- C. Travis CI
- D. Python YAML data libraries
Answer:
B
Explanation:
Genie CLI is a configuration management tool that is designed to validate the working state of the
network before implementing a CI/CD pipeline model. Genie CLI provides a set of commands that
can be used to check the state of the network, view logs, and make changes to network
configurations. It is a powerful tool for validating the state of the network before making changes,
and can help avoid costly mistakes or unexpected issues.
Question 3
Which two practices help make the security of an application a more integral part of the software
development lifecycle? (Choose two.)
- A. Add a step to the CI/CD pipeline that runs a dynamic code analysis tool during the pipeline execution.
- B. Add a step to the CI/CD pipeline that runs a static code analysis tool during the pipeline execution.
- C. Use only software modules that are written by the internal team.
- D. Add a step to the CI/CD pipeline to modify the release plan so that updated versions of the software are made available more often.
- E. Ensure that the code repository server has enabled drive encryption and stores the keys on a Trusted Platform Module or Hardware Security Module.
Answer:
AB
Explanation:
Adding a step to the CI/CD pipeline that runs a dynamic code analysis tool and a static code analysis
tool during the pipeline execution helps make the security of an application a more integral part of
the software development lifecycle. Dynamic code analysis tools search for coding errors and
vulnerabilities while the application is running, while static code analysis tools scan the source code
for potential errors and vulnerabilities. This ensures that any security issues are identified and
addressed before the application is deployed. Additionally, using automated tools helps to reduce
the amount of manual effort required for security testing and can reduce the risk of security flaws
being introduced.
Question 4
A CI/CD pipeline that builds infrastructure components using Terraform must be designed. A step in
the pipeline is needed that checks for errors in any of the .tf files in the working directory. It also
checks the existing state of the defined infrastructure.
Which command does the pipeline run to accomplish this goal?
- A. terraform plan
- B. terraform check
- C. terraform fmt
- D. terraform validate
Answer:
A
Explanation:
https://www.terraform.io/docs/cli/commands/validate.html "use the terraform plan command
instead, which includes an implied validation check."
Question 5
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all
of the modules in the source code that were developed using TDD?
- A. soak testing
- B. unit testing
- C. load testing
- D. volume testing
Answer:
B
Question 6
Refer to the exhibit.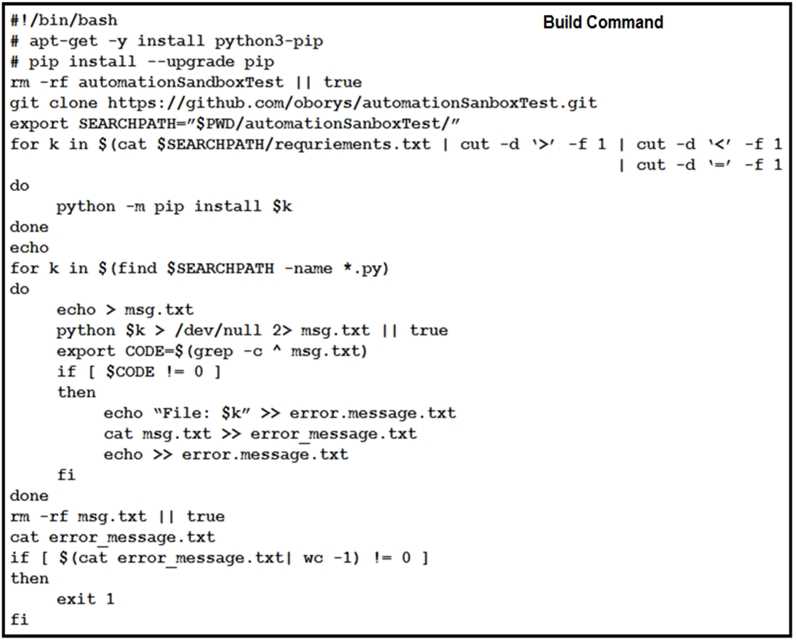
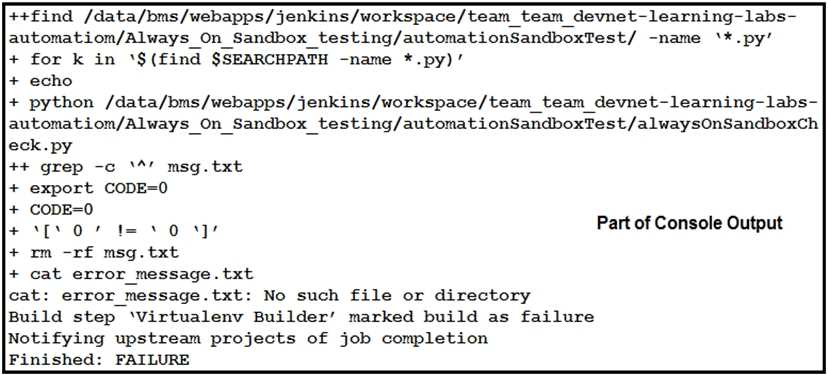
How should the Jenkins job be troubleshooted based on the error provided?
- A. Verify what the responding file created.
- B. Update pip.
- C. Install dependencies.
- D. Place the code in a container and run the job again.
Answer:
A
Question 7
Configuration changes to the production network devices are performed by a CI/CD pipeline. The
code repository and the CI tool are running on separate servers. Some configuration changes are
pushed to the code repository, but the pipeline did not start.
Why did the pipeline fail to start?
- A. The CI server was not configured as a Git remote for the repository.
- B. The webhook call from the code repository did not reach the CI server.
- C. Configuration changes must be sent to the pipeline, which then updates the repository.
- D. The pipeline must be started manually after the code repository is updated.
Answer:
B
Explanation:
A webhook is basically a callback URL that is triggered when certain events occur, such as a code
commit. If the webhook call from the code repository does not reach the CI server, then the pipeline
will not start. According to the Cisco Implementing DevOps Solutions and Practices using Cisco
Platforms (DEVOPS) Study Manual, "A webhook is a web-based feature that enables a remote service
to communicate with a local service, usually through a web server. Webhooks are used to trigger an
action when a specific event occurs, usually in a remote service or application."
Question 8
A new version of an application is being released by creating a separate instance of the application
that is running the new code. Only a small portion of the user base will be directed to the new
instance until that version has been proven stable. Which deployment strategy is this example of?
- A. recreate
- B. blue/green
- C. rolling
- D. canary
Answer:
D
Question 9
Which description of a canary deployment is true?
- A. deployment by accident
- B. deployment that is rolled back automatically after a configurable amount of minutes
- C. deployment relating to data mining development
- D. deployment to a limited set of servers or users
Answer:
D
Question 10
Refer to the exhibit.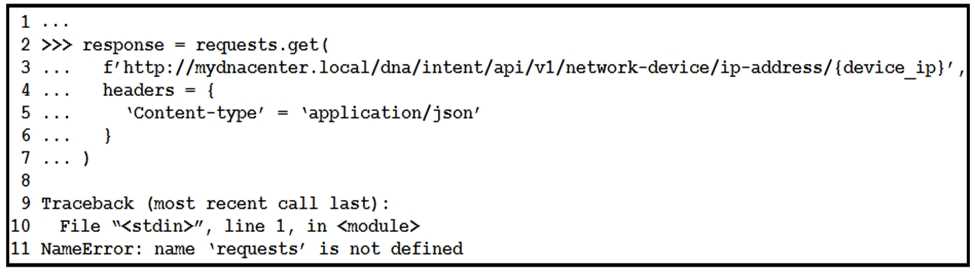
What is causing the requests code to fail?
- A. Rython3 is not compatible with requests.
- B. The requests library is not imported.
- C. The requests library is not installed.
- D. The requests coming into stdin fail because device_ip cannot be parsed.
Answer:
B
Question 11
DRAG DROP
Drag and drop the operations from the left into the correct order on the right when using CI/CD,
assuming that there are no failures or conflicts.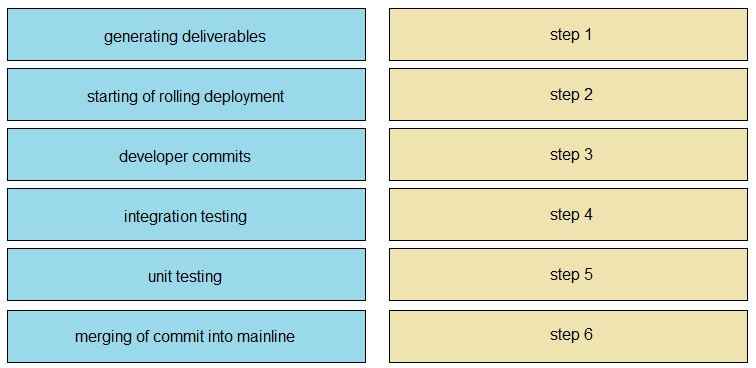
Answer:
Explanation:
developer commits
unit testing
integration testing
merging of commit into mainline
generating deliverables
starting of rolling deployment
Question 12
A DevOps engineering wants to build an application implementation based on the CI/CD pipeline
model. Which service should be used to provide hosted continuous service for open and private
projects?
- A. Ansible
- B. pyATS
- C. Genie CLI
- D. Travis CI
Answer:
D
Question 13
A DevOps engineer has built a new container and must open port 8080 for intercontainer
communication. Which command must be added in a Dockerfile to accomplish this goal?
- A. EXPOSE 8080
- B. FIREWALL ADD-PORT 8080
- C. PORT 8080
- D. OPEN PORT 8080
Answer:
A
Question 14
Which two actions help limit the attack surface of your Docker container? (Choose two.)
- A. Run only a single service in each container.
- B. Run all services in a single image.
- C. Use version tags for base images and dependencies.
- D. Use Kali Linux as a base image.
- E. Download images over HTTPS supporting sites.
Answer:
AC
Explanation:
Running only a single service in each container and using version tags for base images and
dependencies helps limit the attack surface of your Docker container. This ensures that only the
necessary services are running and that you always have the latest versions of the base images and
their dependencies, reducing the risk of malicious code being included in the container image.
Reference: Docker Documentation, Security Best Practices.
Question 15
A DevOps engineer has built a container to host a web-server and it must run as an executable.
Which command must be configured in a Dockerfile to accomplish this goal?
- A. ENTRYPOINT <usr/sbin/apache2ctl>
- B. ENTRYPOINT [“/usr/sbin/apache2ctl”, “-D”, “FOREGROUND”]
- C. ENTRYPOINT [“BACKGROUND”, “-D”, “/usr/sbin/apache2ctl”]
- D. ENTRYPOINT {usr/sbin/apache2ctl}
Answer:
B