cisco 300-810 practice test
Implementing Cisco Collaboration Applications (CLICA)
Question 1
Which authentication method allows a user to log in to an SSO-enabled Cisco Unified
Communications application by utilizing a Microsoft Windows login, thereby not requiring any
credentials to be entered?
- A. Smart Card
- B. OAuth
- C. form-based
- D. Kerberos
Answer:
B
Explanation:
https://www.cisco.com/c/en/us/support/docs/unified-communications/jabber-windows/118773-configure-kerberos-00.html
The main advantage of Kerberos authentication compared to the other authentication methods is
that you do not need to provide your credentials when you log in to Cisco Jabber. If you use Kerberos,
the client does not prompt users for credentials, because authentication was already provided to
gain access to the Windows desktop. This authentication method allows you to log in to Cisco Jabber
with your Microsoft Windows login.
Question 2
When Cisco IM and Presence is configured to use automatic fallback, how long does the Server
Recovery Manager service wait for a failed service/server to remain active before an automatic
fallback is initiated?
- A. 10 minutes
- B. 20 minutes
- C. 30 minutes
- D. 1 hour
Answer:
C
Explanation:
Reference:
https://www.cisco.com/c/en/us/support/docs/unified-communications/unified-communications-manager-im-presence-service/200958-IM-and-Presence-Server-High-Availability.html
Automatic Fallback
Automatic fallback takes place when the server monitors the services and the Server Recovery
Manager(SRM) service will automatically fallback users to their homed nodes. The key in this
configuration is that the Server Recovery Manager(SRM) service will wait 30 minutes for a failed
service/server to remain active before an automatic fallback is initiated. Once this 30 minute up time
is established, user sessions are moved back to their homed nodes. The Jabber client will apply the
re-log in upper and lower limits for the fallback. Automatic fallback is not the default configuration,
but it can be enabled. To enable automatic fallback, change the Enable Automatic Fallback
parameter in the Server Recovery Manager Service Parameters to value True.
Question 3
Which entity is a standard component used for authentication by SAML 2.0?
- A. identity provider
- B. session broker
- C. Internet service provider
- D. client access server
Answer:
A
Question 4
An engineer must configure a test user mailbox in a newly deployed Cisco Unity Express module.
Which console command set reflects the correct configuration in this scenario?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Question 5
Which two command line arguments can you specify when installing Cisco Jabber for windows?
(Choose two.)
- A. CISCO_UDS_DOMAIN
- B. TFTP_ADDRESS
- C. VOICEMAIL_SERVER_ADDRESS
- D. SERVICES_DOMAIN
- E. TFTP
Answer:
D, E
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/jabber/11_0/
CJAB_BK_D657A25F_00_deployment-installation-guide-jabber-110/CJAB_BK_D657A25F_00_deployment-installation-guide-jabber-110_chapter_01100.html#JABW_RF_CE43EF4C_00
Question 6
Which description of an IdP server is true?
- A. authenticates user credentials
- B. provides user authorization
- C. is an authentication request that is generated by a Cisco Unified Communications application
- D. consists of pieces of security information that are transferred to the service provider for user authentication
Answer:
A
Explanation:
SSO uses Security Assertion Markup Language (SAML) to exchange authentication details between an
Identity Provider (IdP) and a service provider. The identity provider authenticates user credentials
and issues SAML assertions, which are pieces of security information transferred from the identity
provider to the service provider for user authentication. Each assertion is an XML document that
contains trusted statements about a subject including, for example, username and privileges. SAML
assertions are usually digitally signed to ensure their authenticity.
Reference:
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/cust_contact/contact_center/crs/express_11_6_2/features/guide/uccx_b_features-guide-1162/uccx_b_features-guide-1162_chapter_010.html#concept_D4C0DDEE975FE5C9416479AB5D778237
Question 7
Refer to the exhibit.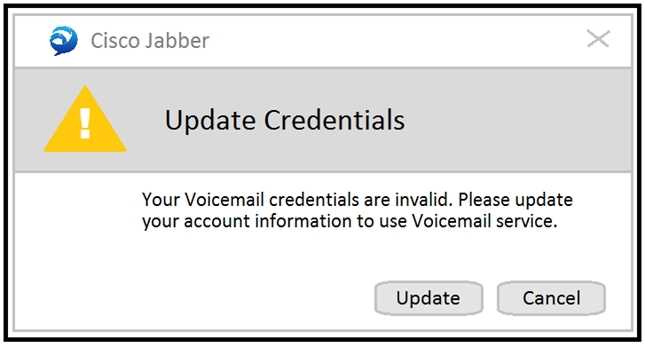
Which action allows a remote Cisco Jabber user utilizing Mobile and Remote Access to automatically
log in to a Cisco Unity Connection voicemail box via OAuth?
- A. Add CUCM under System Settings > Authz Servers in Cisco Expressway-E.
- B. Add CUCM under System Settings > Authz Servers in Cisco Expressway-C.
- C. Add CUCM under System Settings > Authz Servers in Cisco Unity.
- D. Add CUCM under System Settings > Authz Servers in Cisco Unity Connection.
Answer:
D
Explanation:
Reference: https://community.cisco.com/t5/unified-communications/jabber-mra-unity-voice-mail-
integration- issue/td-p/3195653
Question 8
Refer to the exhibit.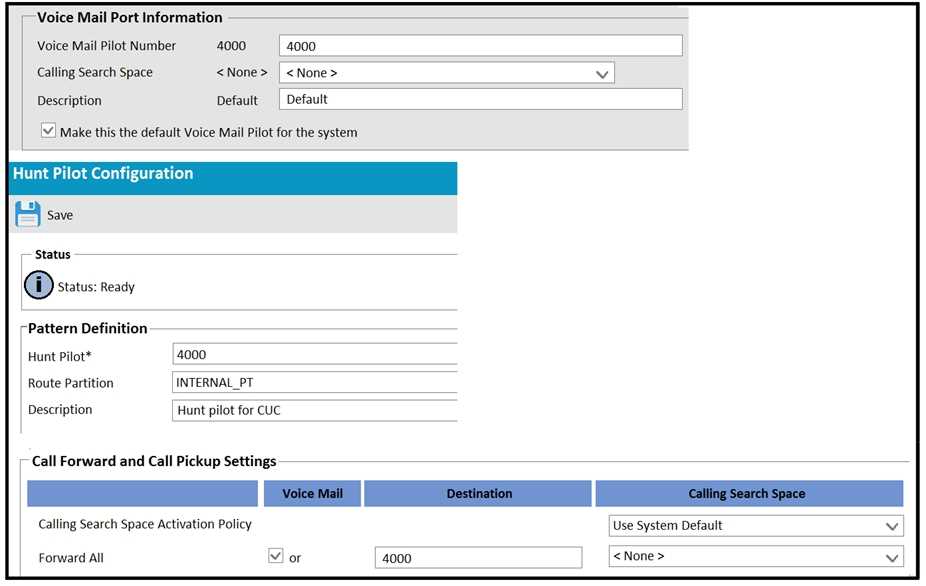
Cisco Unity Connection and Cisco Unified Communications Manager are integrated by using SCCP.
The Voice Mail Ports are registered. Users report that calls fail when forwarded to voicemail. Which is
a cause of the issue?
- A. The call forward and call pickup settings do not have a CSS on Forward All.
- B. The Voice Mail Port partition on the CSS of the phone is missing.
- C. The Voice Mail Pilot is not configured with a CSS that contains the INTERNAL_PT.
- D. The CSS on the Voice Mail Pilot is missing partitions for user phones.
Answer:
C
Question 9
Refer to the exhibit.
Which end-user option can resolve this issue?
- A. Standard CTI Reception of SRTP Key Material
- B. Standard CTI Allow Calling Number Modification
- C. Standard CTI Allow Control of Phones Supporting Rollover Mode
- D. Standard CTI Allow Call Monitoring
Answer:
C
Explanation:
https://community.cisco.com/t5/collaboration-applications/jabber-for-windows-cannot-control-
8841-desk-phone/td-p/2569503
Question 10
Which function of the Cisco IM and Presence high availability solution is true?
- A. When the server has been restored to a normal state, user sessions remain on the backup server.
- B. When an event takes place, the end user sessions are not moved from the failed server to the backup.
- C. When the server has been restored, the server automatically fails back.
- D. When a high availability event takes place, the end user sessions are moved from the failed server to the backup.
Answer:
D
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/unified-communications/unified-communications-manager-im-presence-service/200958-IM-and-Presence-Server-High-Availability.html
Question 11
Which Cisco IM and Presence service must be activated and running for IM Presence to successfully
integrate with Cisco Unified Communications Manager?
- A. Cisco DHCP Monitor Service
- B. Cisco AXL Web Service
- C. Self-Provisioning IVR
- D. Cisco XCP Authentication Service
Answer:
B
Explanation:
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/cucm/im_presence/configAdminGuide/12_0_1/cup0_b_config-admin-guide-imp-1201/cup0_b_config-admin-guide-imp-1201_chapter_0100.html
Question 12
Refer to the exhibit.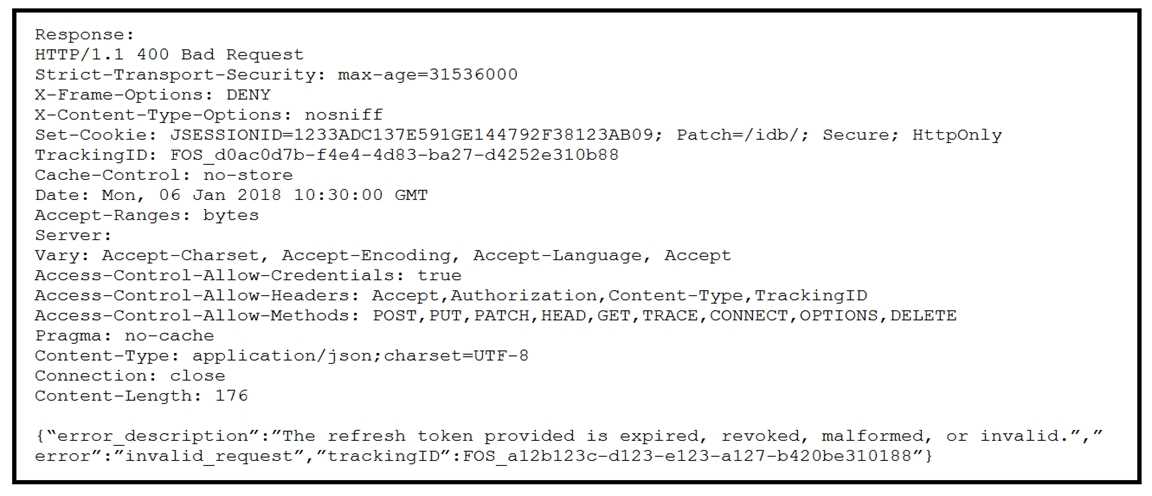
Apple Push Notification integration is configured in a Cisco Unified IM and Presence deployment and
has been working property. Administrators now report the error “Push notification settings cannot be
configured. 400 Bad Request.” in the GUI, and HTTP logs are displaying the errors that are shown in
the exhibit. Which action solves this issue?
- A. Fix the network connectivity to Apple iCloud.
- B. Reboot the IM&P cluster.
- C. Change the HTTP proxy settings to remove errors in request syntax.
- D. Update Refresh Token Manually.
Answer:
D
Explanation:
Reference:
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/cucm/push_notifications/cucm_b_push-
notifications-deployment-guide.pdf
Question 13
Which two methods does Cisco Jabber use for contact searching in an on-premises deployment
model? (Choose two.)
- A. HTTP
- B. XMPP
- C. UDS
- D. LDAP
- E. SIP
Answer:
CD
Explanation:
Reference:
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/cucm/srnd/collab11/collab11/presence.ht
ml
Question 14
What is the maximum number of Cisco Unity Connection locations connected in a HTTPS network?
- A. 50
- B. 25
- C. 200
- D. 10
Answer:
B
Explanation:
Reference:
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/connection/10x/https_networking/
guide/10xcuchttpsnetx/10xcuchttpsnet010.html
Question 15
What is the primary mechanism in Cisco Unity Connection that is used for toll fraud prevention?
- A. restriction tables
- B. fraud tables
- C. transfer rules
- D. calling search spaces
Answer:
A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/connection/10x/security/
guide/10xcucsecx/10xcucsec020.pdf