cisco 300-740 practice test
Designing and Implementing Secure Cloud Access for Users and Endpoints
Question 1
According to Cisco Security Reference Architecture, which solution provides threat intelligence and
malware analytics?
- A. Cisco pxGrid
- B. Cisco XDR
- C. Cisco Talos
- D. Cisco Umbrella
Answer:
C
Explanation:
Comprehensive and Detailed Explanation From Exact Extract:
Cisco Talos is Cisco’s threat intelligence organization, delivering real-time threat intelligence and
malware analytics to help organizations detect and prevent threats before they impact the network.
According to the SCAZT guide, Talos provides comprehensive coverage of threat data including
signatures, indicators of compromise, and context-driven analytics. This intelligence feeds into Cisco
security platforms such as Cisco SecureX and Cisco Secure Endpoint to enhance detection,
investigation, and response capabilities. Talos is explicitly referenced in the Threat Response section
as the primary source of threat intelligence and malware analytics that supports cloud and endpoint
security frameworks.
Reference: Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) Study
Guide, Section 6: Threat Response, Pages 112-115.
Question 2
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
- A. Reactive and heuristic-based
- B. Stochastic and event-based
- C. Correlative and feedback-based
- D. Adaptive and behavioral-based
Answer:
D
Explanation:
Comprehensive and Detailed Explanation From Exact Extract:
According to the SCAZT documentation, web application firewalls (WAFs) designed to protect against
zero-day Distributed Denial of Service (DDoS) attacks leverage adaptive and behavioral-based
algorithms. These algorithms dynamically analyze traffic patterns, baseline normal behavior, and
detect anomalies that could indicate novel or zero-day attacks. Unlike signature-based detection,
adaptive and behavioral methods adjust in real-time to emerging threats, learning from ongoing
traffic without relying on pre-defined rules. This proactive approach enables rapid detection and
mitigation of unknown DDoS vectors, critical for cloud and network security where threats evolve
constantly.
Reference: Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) Study
Guide, Section 3: Network and Cloud Security, Pages 75-77.
Question 3
An administrator must deploy an endpoint posture policy for all users. The organization wants to
have all endpoints checked against antimalware definitions and operating system updates and
ensure that the correct Secure Client modules are installed properly. How must the administrator
meet the requirements?
- A. Configure the WLC to provide local posture services, and configure Cisco ISE to receive the compliance verification from the WLC to be used in an authorization policy.
- B. Create an ASA Firewall posture policy, upload the Secure Client images to the NAD, and create a local client provisioning portal.
- C. Create the required posture policy within Cisco ISE, configure redirection on the NAD, and ensure that the client provisioning policy is correct.
- D. Identify the antimalware being used, create an endpoint script to ensure that it is updated, and send the update log to Cisco ISE for processing.
Answer:
C
Question 4
Refer to the exhibit.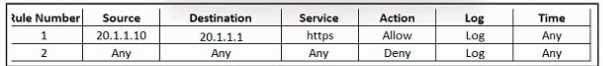
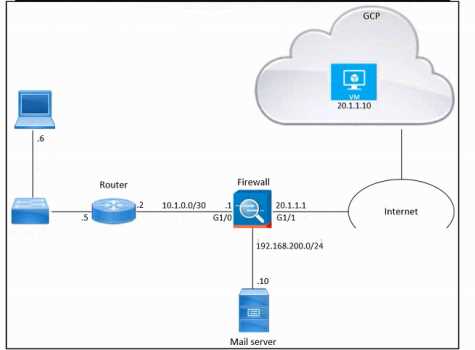
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual
machine to the on-premises mail server. All other connections from the virtual machine to the mail
server must be blocked. The indicated rules were applied to the firewall; however, the virtual
machine cannot access the mail server. Which two actions should be performed on the firewall to
meet the requirement? (Choose two.)
- A. Set IP address 192.168.200.10 as the destination in rule 1.
- B. Move up rule 2.
- C. Set IP address 20.1.1.1 as the source in rule 1.
- D. Configure a NAT rule.
- E. Configure a security group.
Answer:
A, D
Question 5
Refer to the exhibit.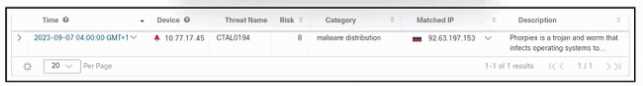
Refer to the exhibit. A security engineer deployed Cisco Secure XDR, and during testing, the log entry
shows a security incident. Which action must the engineer take first?
- A. Uninstall the malware.
- B. Block IP address 10.77.17.45.
- C. Isolate the endpoint.
- D. Rebuild the endpoint.
Answer:
C
Question 6
Refer to the exhibit.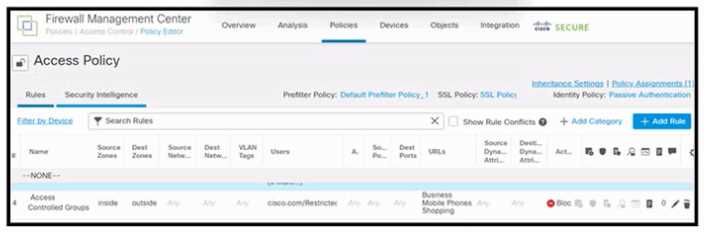
Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to
prevent restricted users from being able to browse any business or mobile phone shopping websites.
The indicated policy was applied; however, the restricted users still can browse on the mobile phone
shopping websites during business hours. What should be done to meet the requirement?
- A. Set Dest Zones to Business Mobile Phones Shopping.
- B. Set Dest Networks to Business Mobile Phones Shopping.
- C. Set Time Range for rule 4 of Access Controlled Groups to All.
- D. Move rule 4 Access Controlled Groups to the top.
Answer:
D
Question 7
Refer to the exhibit.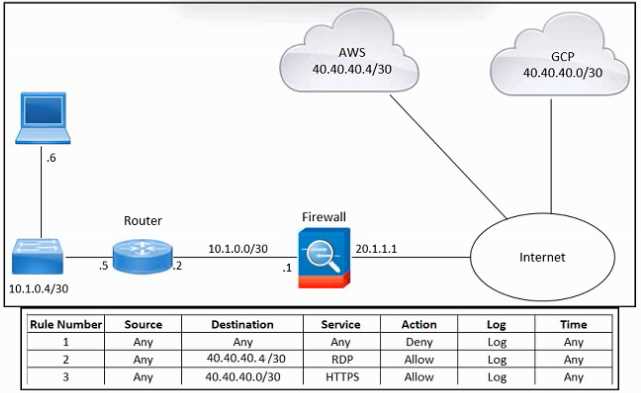
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS
access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The
indicated rules were applied to the firewall; however, none of the virtual machines in AWS and
Google Cloud Platform are accessible. What should be done to meet the requirement?
- A. Move rule 2 to the first position.
- B. Configure a NAT overload rule
- C. Configure a virtual private cloud firewall rule
- D. Move rule 1 to the last position
Answer:
A
Question 8
Refer to the exhibit.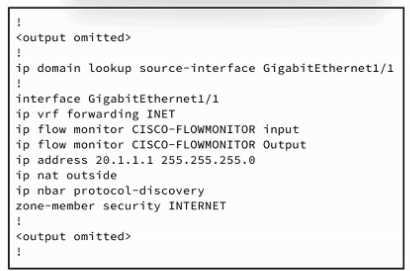
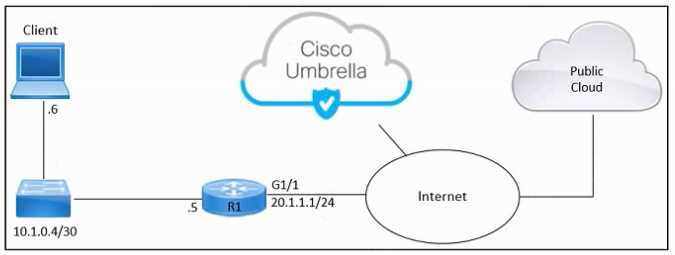
Refer to the exhibit. An engineer must connect an on-premises network to the public cloud using
Cisco Umbrella as a Cloud Access Security Broker. The indicated configuration was applied to router
R1; however, connectivity to Umbrella fails with this error: %OPENDNS-3-DNS_RES_FAILURE. Which
action must be taken on R1 to enable the connection?
- A. Configure the Open DNS servers with the ip name-server command.
- B. Configure a DHCP scope using the ip dhcp pool command.
- C. Add the opendns in command to the interface configuration.
- D. Add the opendns out command to the interface configuration.
Answer:
B
Question 9
Which mitigation technique does a web application firewall use to protect a web server against DDoS
attacks?
- A. Source-specific ACL
- B. Standard ACL
- C. Packet filtering
- D. Rate-based rules
Answer:
D
Question 10
Refer to the exhibit.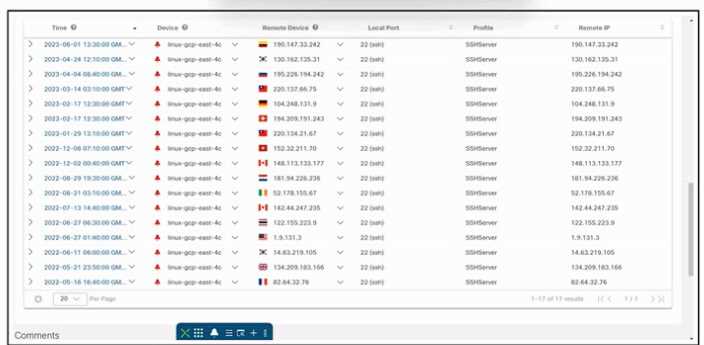
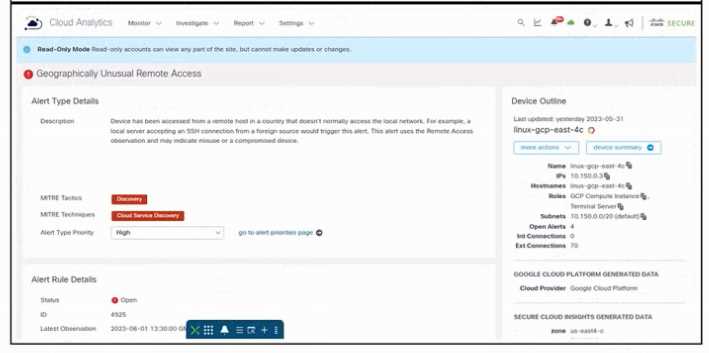
Refer to the exhibit. An engineer is investigating an issue by using Cisco Secure Cloud Analytics. The
engineer confirms that the connections are unauthorized and informs the incident management
team. Which two actions must be taken next? (Choose two.)
- A. Reinstall the host from a recent backup.
- B. Quarantine the host
- C. Reinstall the host from scratch.
- D. Create a firewall rule that has a source of linux-gcp-east-4c, a destination of Any, and a protocol of SSH.
- E. Create a firewall rule that has a source of Any, a destination of linux-gcp-east-4c, and a protocol of SSH.
Answer:
B, E
Question 11
In the zero-trust network access model, which criteria is used for continuous verification to modify
trust levels?
- A. System patching status
- B. Detected threat levels
- C. User and device behavior
- D. Network traffic patterns
Answer:
C
Question 12
Refer to the exhibit.
Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to
block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed.
What should be done to meet the requirement?
- A. Change consumer_filter_ref to HTTP Consumer.
- B. Add HTTP to 14_params.
- C. Decrease the priority of the template to 50.
- D. Increase the priority of the template to 200.
Answer:
B
Question 13
Refer to the exhibit.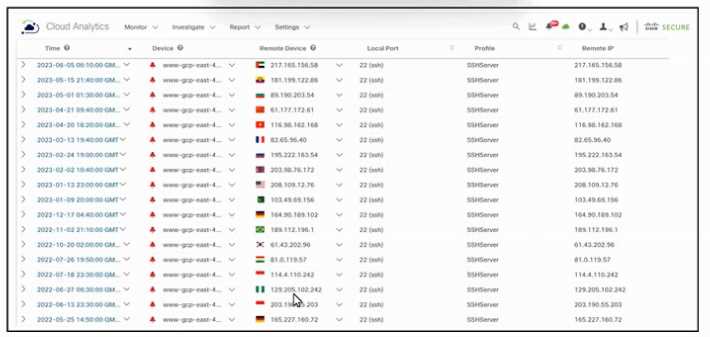
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is
occurring?
- A. Persistent remote-control connections
- B. Distributed DDoS attack
- C. Geographically unusual remote access
- D. Memory exhaustion attempt toward port 22
Answer:
C
Question 14
Refer to the exhibit.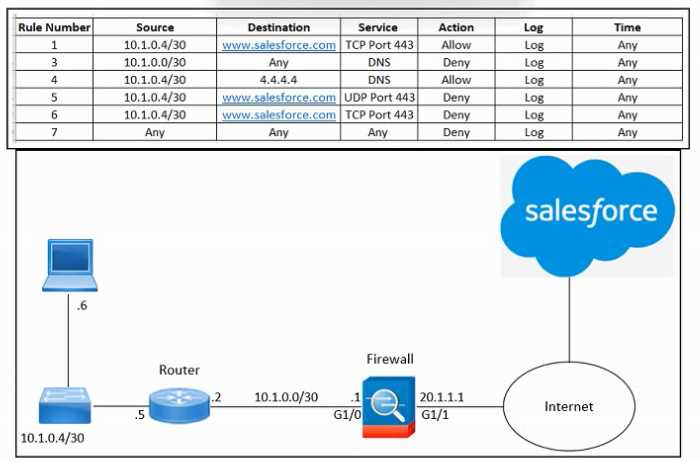
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP
address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated
configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution;
however, the client still cannot access the URL. What should be done to meet the requirements?
- A. Remove rule 3
- B. Move rule 5 to the top
- C. Remove rule 7
- D. Move rule 6 to the top
Answer:
A
Question 15
Refer to the exhibit.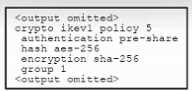
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use
AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall;
however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the
requirement? (Choose two.)
- A. encryption aes-256
- B. ipsec-proposal sha-256-aes-256
- C. integrity aes-256
- D. ipsec-proposal AES256-SHA256
- E. hash sha-256
Answer:
A, E