cisco 300-735 practice test
automating cisco security solutions (sauto)
Question 1
Which two URI parameters are needed for the Cisco Stealthwatch Top Alarm Host v1 API? (Choose two.)
- A. startAbsolute
- B. externalGeos
- C. tenantId
- D. intervalLength
- E. tagID
Answer:
ce
Question 2
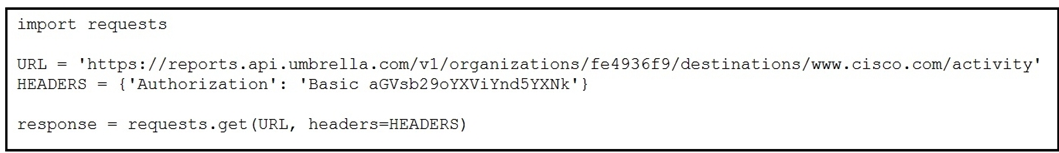
Refer to the exhibit. The script outputs too many results when it is queried against the Cisco Umbrella Reporting API.
Which two configurations restrict the returned result to only 10 entries? (Choose two.)
- A. Add params parameter in the get and assign in the {"return": "10"} value.
- B. Add ?limit=10 to the end of the URL string.
- C. Add params parameter in the get and assign in the {"limit": "10"} value.
- D. Add ?find=10 to the end of the URL string.
- E. Add ?return=10 to the end of the URL string.
Answer:
bc
Question 3
After changes are made to the Cisco Firepower Threat Defense configuration using the Cisco Firepower Device Manager API, what must be done to ensure that the new policy is activated?
- A. Submit a POST to the /api/fdm/latest/operational/deploy URI.
- B. Submit a GET to the /api/fdm/latest/operational/deploy URI.
- C. Submit a PUT to the /api/fdm/latest/devicesettings/pushpolicy URI.
- D. Submit a POST to the /api/fdm/latest/devicesettings/pushpolicy URI.
Answer:
a
Question 4
In Cisco AMP for Endpoints, which API queues to find the list of endpoints in the group Finance Hosts, which has a GUID of 6c3c2005-4c74-4ba7-8dbb- c4d5b6bafe03?
- A. https://api.amp.cisco.com/v1/endpoints?group[]=6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
- B. https://api.amp.cisco.com/v1/computers?group_guid[]=6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
- C. https://api.amp.cisco.com/v1/computers?group_guid-6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
- D. https://api.amp.cisco.com/v1/endpoints?group-6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03
Answer:
b
Question 5
DRAG DROP A Python script is being developed to return the top 10 identities in an organization that have made a DNS request to www.cisco.com.
Drag and drop the code to complete the Cisco Umbrella Reporting API query to return the top identities. Not all options are used.
Select and Place: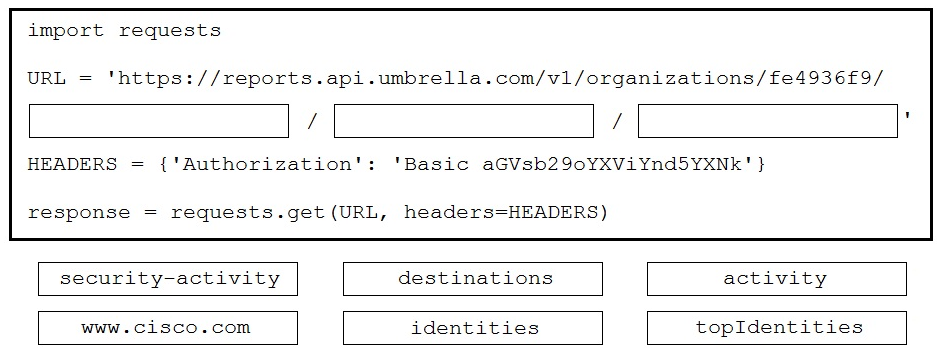
Answer:
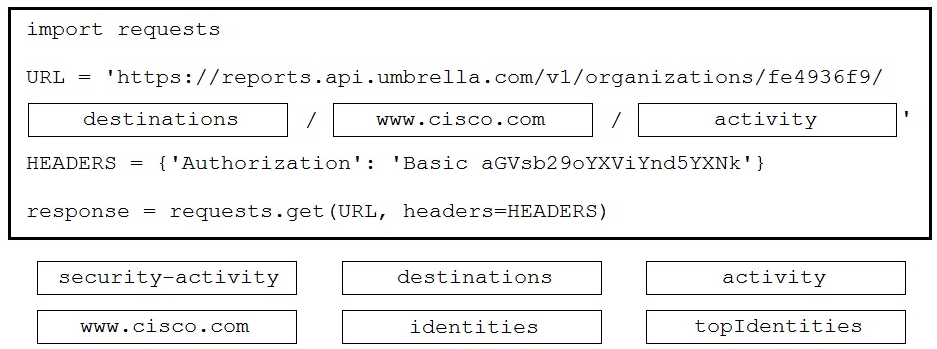
Reference:
https://docs.umbrella.com/umbrella-api/docs/reporting-destinations-most-recent-requests
Question 6
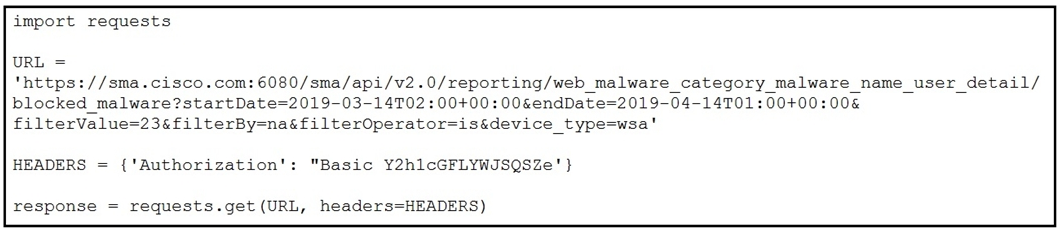
Refer to the exhibit.
What must be present in a Cisco Web Security Appliance before the script is run?
- A. reporting group with the name web_malware_category_malware_name_user_detail
- B. data for specified dates
- C. reporting group with the name blocked_malware
- D. data in the queried category
Answer:
a
Question 7
Which URI string is used to create a policy that takes precedence over other applicable policies that are configured on Cisco Stealthwatch?
- A. /tenants/{tenantId}/policy/system/host-policy
- B. /tenants/{tenantId}/policy/system/role-policy
- C. /tenants/{tenantId}/policy/system
- D. /tenants/{tenantId}/policy/system/{policyId}
Answer:
a
Question 8
If the goal is to create an access policy with the default action of blocking traffic, using Cisco Firepower Management Center REST APIs, which snippet is used?
A.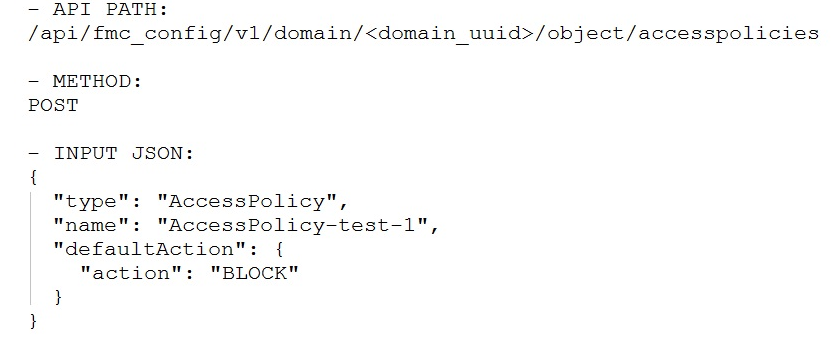
B.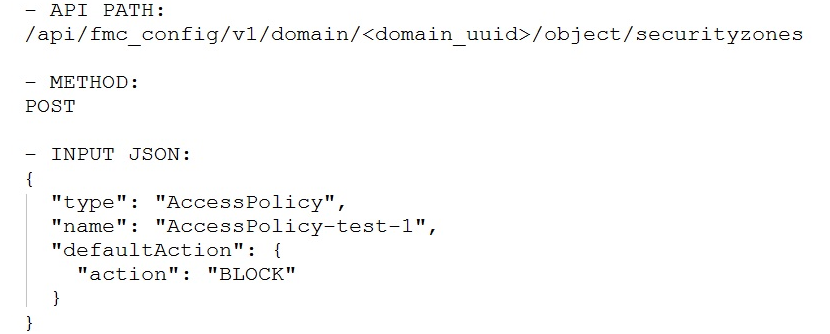
C.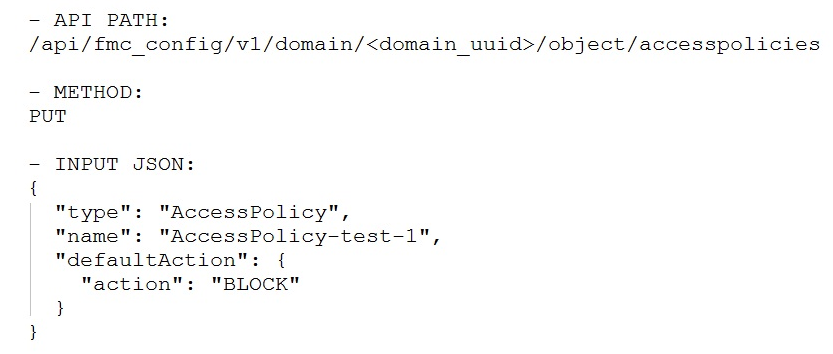
D.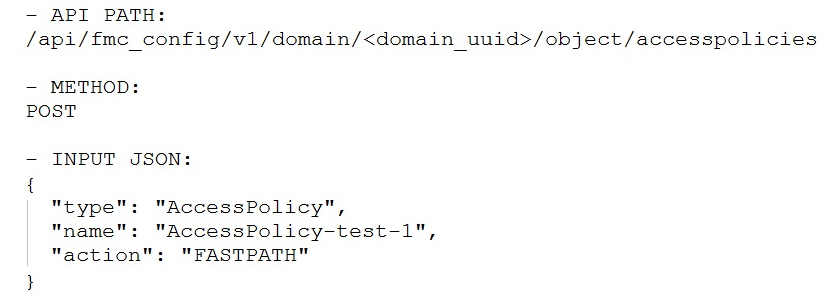
Answer:
d
Question 9
Which query parameter is required when using the reporting API of Cisco Security Management Appliances?
- A. device_type
- B. query_type
- C. filterValue
- D. startDate + endDate
Answer:
d
Question 10
DRAG DROP Drag and drop the code to complete the script to search Cisco ThreatGRID and return all public submission records associated with cisco.com. Not all options are used.
Select and Place: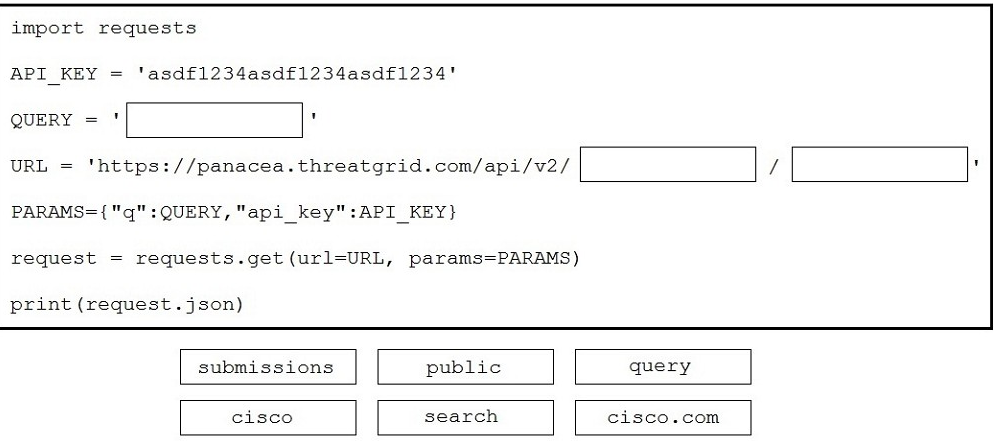
Answer:
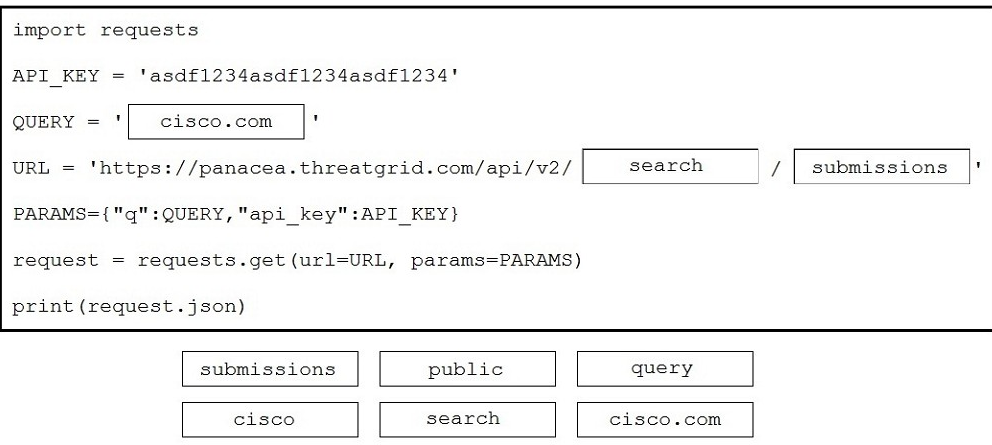
Reference:
https://community.cisco.com/t5/endpoint-security/amp-threat-grid-api/m-p/3538319