cisco 300-735 practice test
Automating Cisco Security Solutions (SAUTO)
Question 1
Which description of synchronous calls to an API is true?
- A. They can be used only within single-threaded processes.
- B. They pause execution and wait for the response.
- C. They always successfully return within a fixed time.
- D. They can be used only for small requests.
Answer:
B
Question 2
DRAG DROP
Drag and drop the code to complete the script to search Cisco ThreatGRID and return all public
submission records associated with cisco.com. Not all options are used.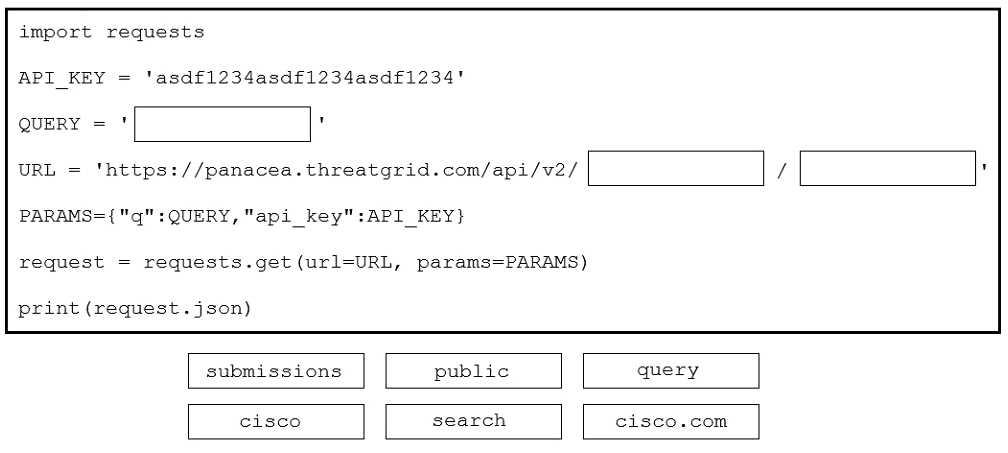
Answer:
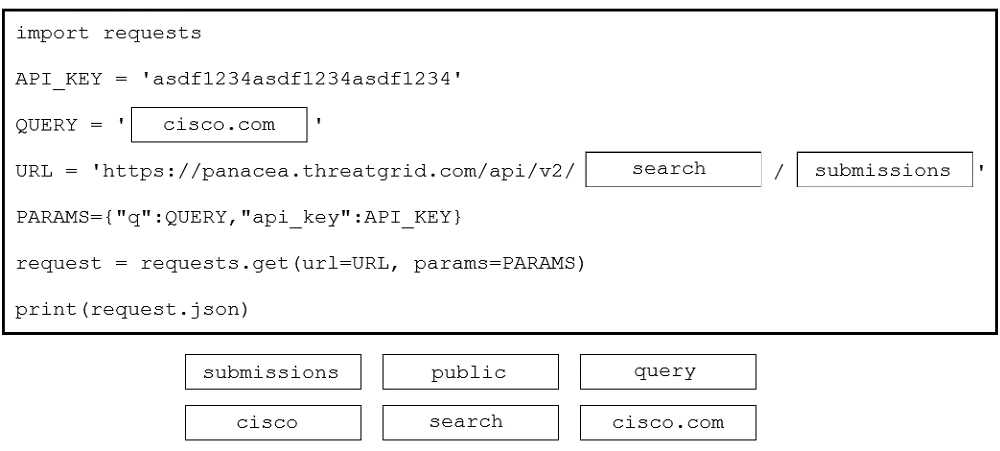
Reference:
https://community.cisco.com/t5/endpoint-security/amp-threat-grid-api/m-p/3538319
Question 3
Refer to the exhibit.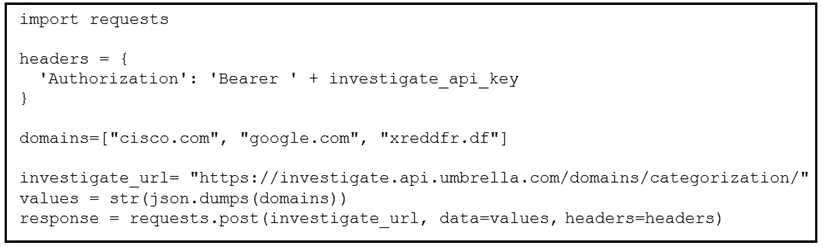
What does the response from the API contain when this code is executed?
- A. error message and status code of 403
- B. newly created domains in Cisco Umbrella Investigate
- C. updated domains in Cisco Umbrella Investigate
- D. status and security details for the domains
Answer:
D
Question 4
Refer to the exhibit.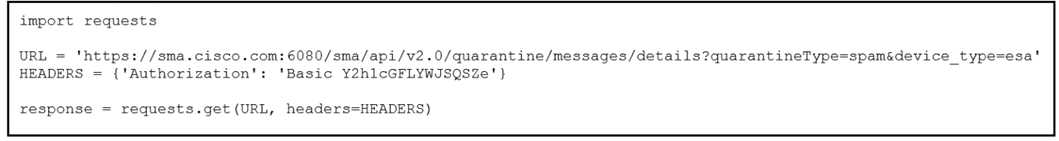
A security engineer attempts to query the Cisco Security Management appliance to retrieve details
of a specific message.
What must be added to the script to achieve the desired result?
- A. Add message ID information to the URL string as a URI.
- B. Run the script and parse through the returned data to find the desired message.
- C. Add message ID information to the URL string as a parameter.
- D. Add message ID information to the headers.
Answer:
C
Question 5
DRAG DROP
Drag and drop the code to complete the API call to query all Cisco Stealthwatch Cloud observations.
Not all options are used.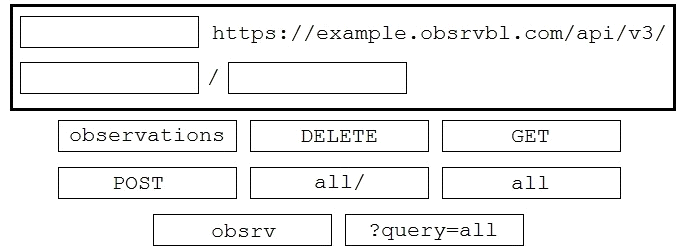
Answer:
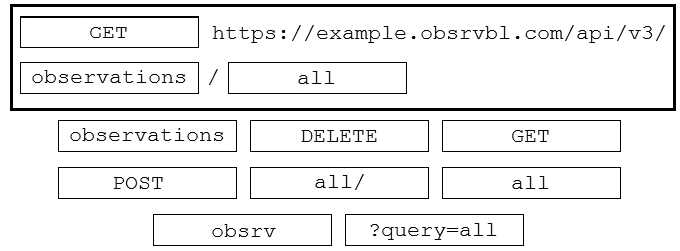
Question 6
Refer to the exhibit.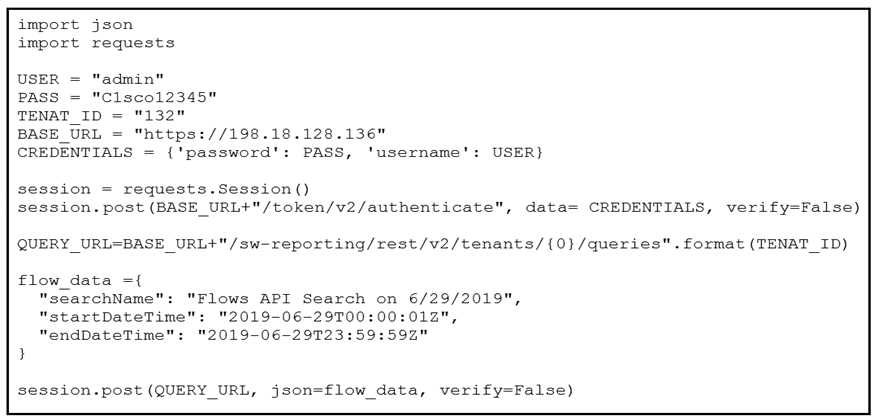
A network operator must generate a daily flow report and learn how to act on or manipulate
returned dat
a. When the operator runs the script, it returns an enormous amount of information.
Which two actions enable the operator to limit returned data? (Choose two.)
- A. Add recordLimit. followed by an integer (key:value) to the flow_data.
- B. Add a for loop at the end of the script, and print each key value pair separately.
- C. Add flowLimit, followed by an integer (key:value) to the flow_data.
- D. Change the startDateTime and endDateTime values to include smaller time intervals.
- E. Change the startDate and endDate values to include smaller date intervals.
Answer:
AB
Question 7
Refer to the exhibit.
Which expression prints the text "802.1x"?
- A. print(quiz[0]['choices']['b'])
- B. print(quiz['choices']['b'])
- C. print(quiz[0]['choices']['b']['802.1x'])
- D. print(quiz[0]['Question:']['choices']['b'])
Answer:
A
Question 8
DRAG DROP
Refer to the exhibit.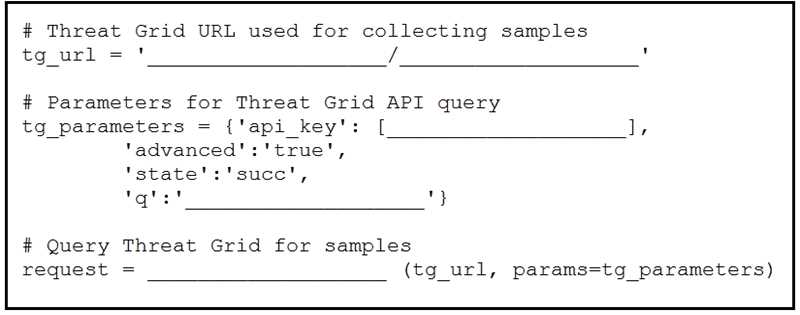
Drag and drop the elements from the left onto the script on the right that queries Cisco ThreatGRID
for indications of compromise.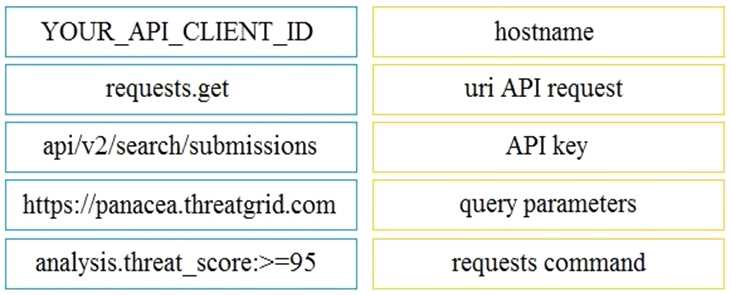
Answer:
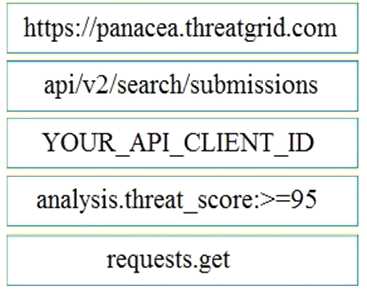
Reference:
https://community.cisco.com/t5/endpoint-security/amp-threat-grid-api/m-p/3538319
Question 9
What are two advantages of Python virtual environments? (Choose two.)
- A. Virtual environments can move compiled modules between different platforms.
- B. Virtual environments permit non-administrative users to install packages.
- C. The application code is run in an environment that is destroyed upon exit.
- D. Virtual environments allow for stateful high availability.
- E. Virtual environments prevent packaging conflicts between multiple Python projects.
Answer:
CE
Question 10
DRAG DROP
Drag and drop the code to complete the curl query to the Umbrella Reporting API that provides a
detailed report of blocked security activity events from the organization with an organizationId of
"12345678" for the last 24 hours. Not all options are used.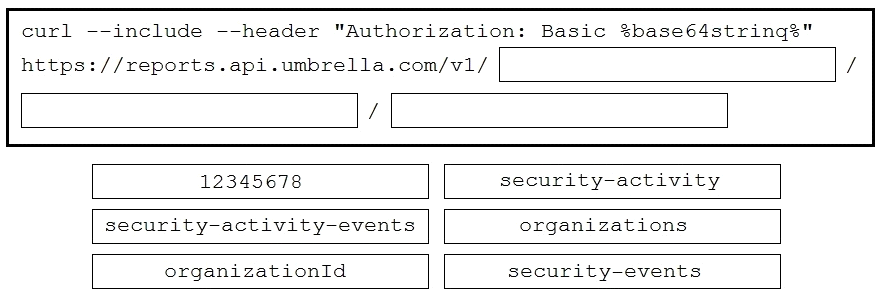
Answer:
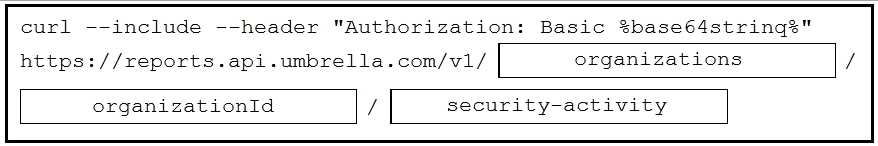
Reference:
https://docs.umbrella.com/umbrella-api/docs/security-activity-report
Question 11
When
the
URI
"/api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-
6d9ed49b625f/policy/accesspolicies" is used to make a POST request, what does "e276abec-e0f2-
11e3-8169-6d9ed49b625f" represent?
- A. API token
- B. domain UUID
- C. access policy UUID
- D. object UUID
Answer:
B
Question 12
Which snippet is used to create an object for network 10.0.69.0/24 using Cisco Firepower
Management Center REST APIs?
A)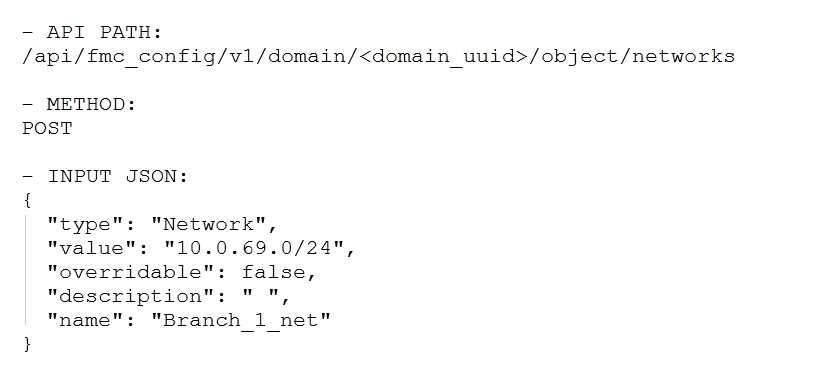
B)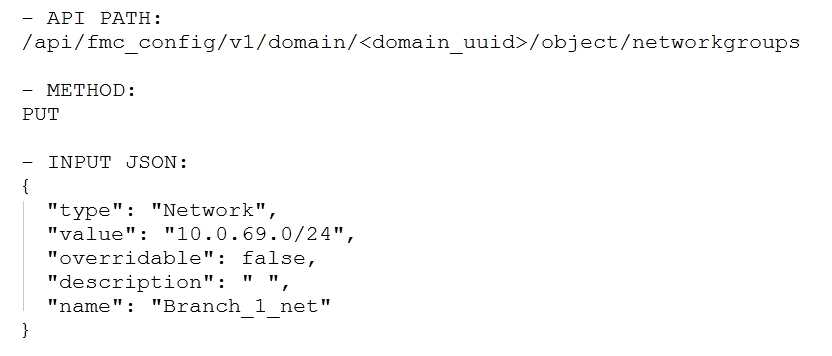
C)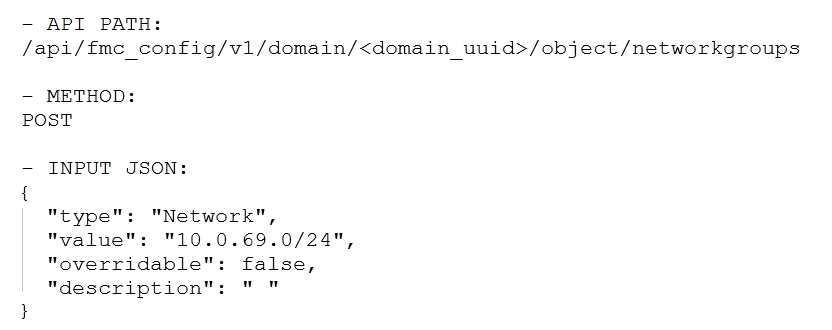
D)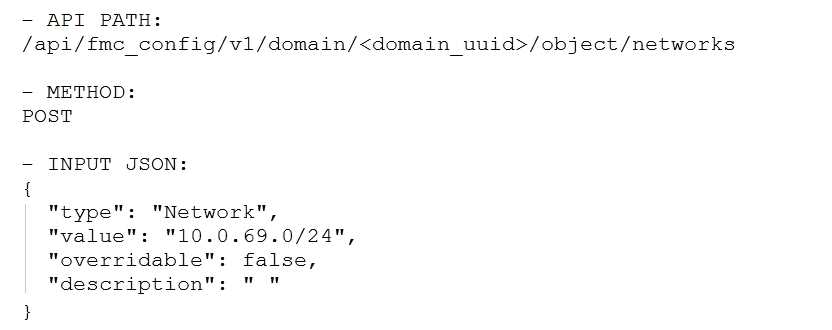
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Question 13
DRAG DROP
Drag and drop the code to complete the curl command to query the Cisco Umbrella Investigate API
for the umbrella popularity list. Not all options are used.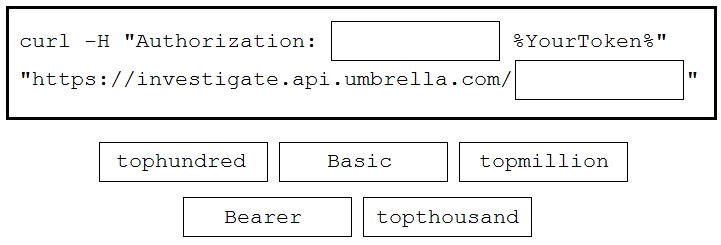
Answer:
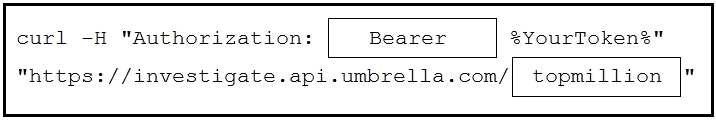
Reference:
https://docs.umbrella.com/investigate-api/reference
Question 14
DRAG DROP
Drag and drop the items to complete the ThreatGRID API call to return a curated feed of sinkholed-
ip-dns in stix format. Not all options are used.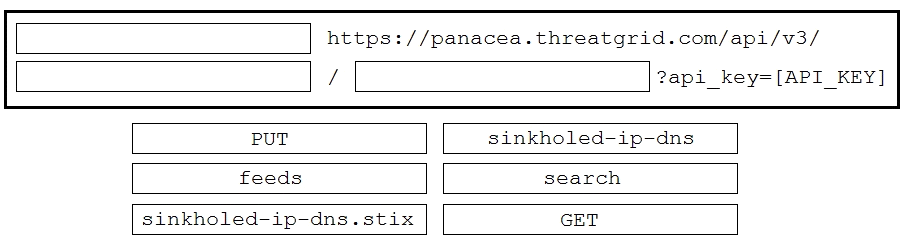
Answer:
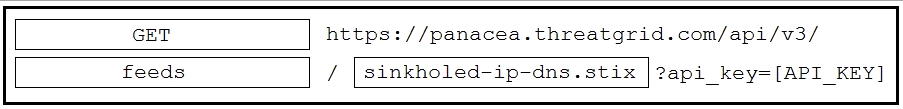
Reference:
https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2019/pdf/DEVNET-2164.pdf
Question 15
In Cisco AMP for Endpoints, which API queues to find the list of endpoints in the group "Finance
Hosts," which
has a GUID of 6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03?
A.
https://api.amp.cisco.com/v1/endpoints?group[]=6c3c2005-4c74-4ba7-8dbb
- c4d5b6bafe03
B.
https://api.amp.cisco.com/v1/computers?group_guid[]=6c3c2005-4c74-4ba7-8dbb
- c4d5b6bafe03
C.
https://api.amp.cisco.com/v1/computers?group_guid-6c3c2005-4c74-4ba7-8dbb
- c4d5b6bafe03
D.
https://api.amp.cisco.com/v1/endpoints?group-6c3c2005-4c74-4ba7-8dbb
- c4d5b6bafe03
Answer:
B