cisco 300-730 practice test
Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)
Question 1
DRAG DROP
Drag and drop the correct commands from the night onto the blanks within the code on the left to
implement a design that allow for dynamic spoke-to-spoke communication. Not all comments are
used.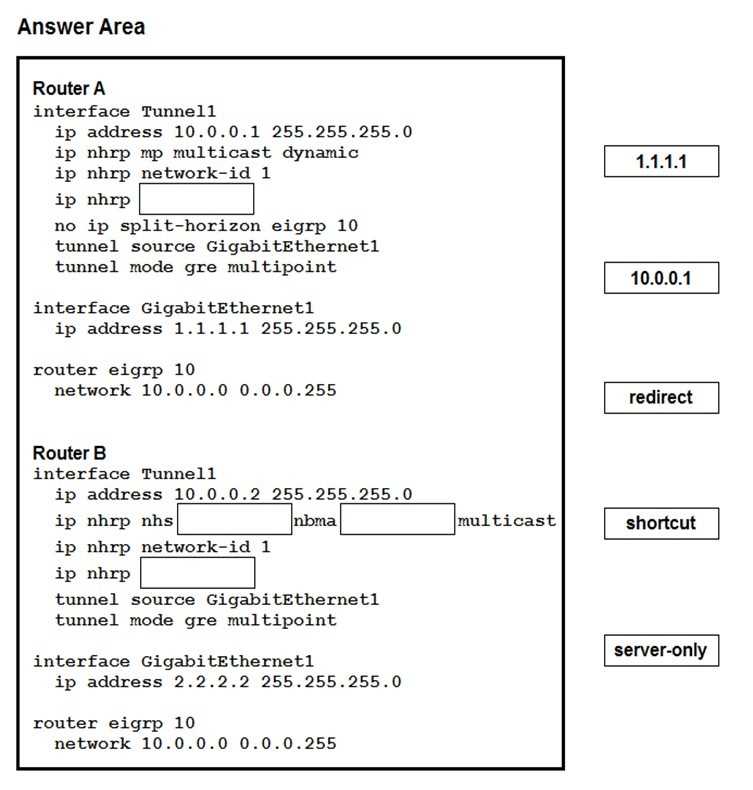
Answer:
Explanation: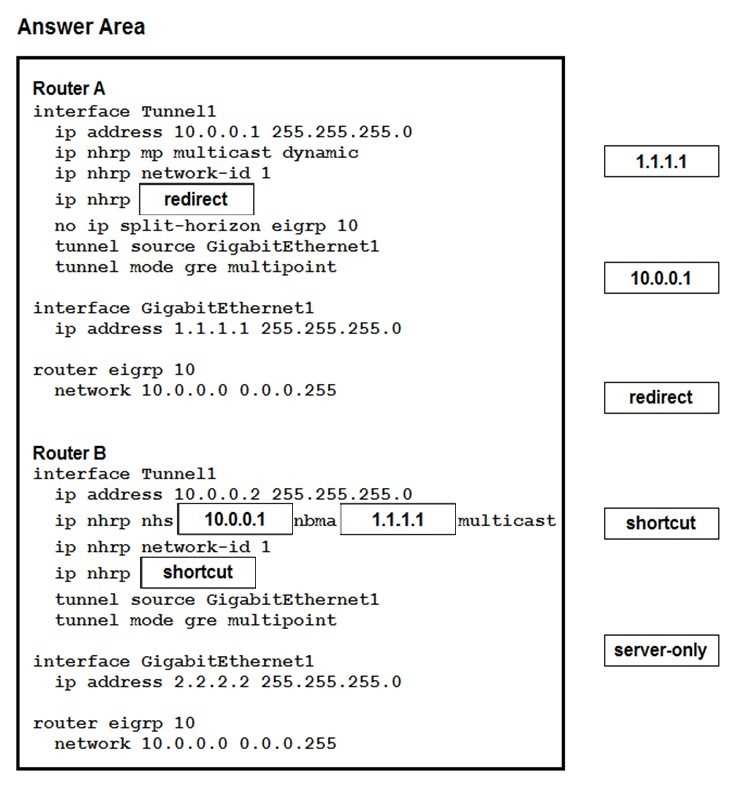
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_dmvpn/configuration/xe-16/sec-conn-dmvpn-xe-16-book/sec-conn-dmvpn-summ-maps.html
Question 2
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2 packet
will contain details of the exchange?
- A. IKEv2 IKE_SA_INIT
- B. IKEv2 INFORMATIONAL
- C. IKEv2 CREATE_CHILD_SA
- D. IKEv2 IKE_AUTH
Answer:
C
Explanation:
The IKEv2 CREATE_CHILD_SA packet is used to establish a new security association (SA) between
two peers. This packet contains the details of the exchange, including the traffic selectors, the
cryptographic algorithms and keys to be used, and any other relevant information
Question 3
Refer to the exhibit.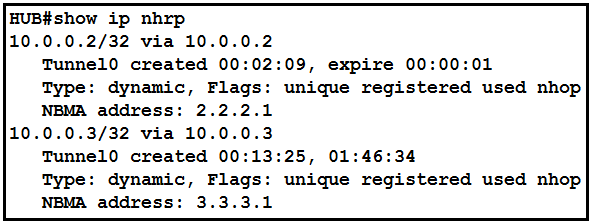
The DMVPN tunnel is dropping randomly and no tunnel protection is configured. Which spoke
configuration mitigates tunnel drops?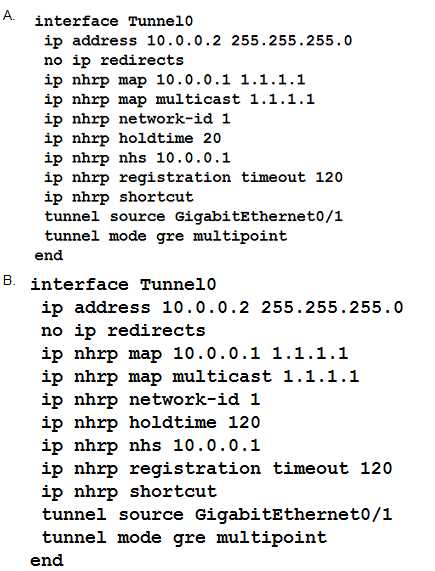
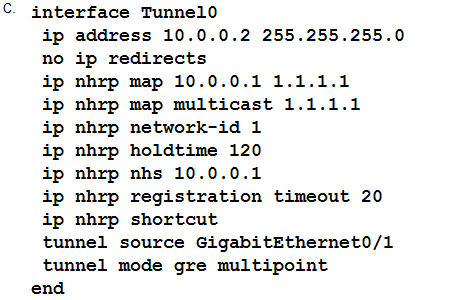
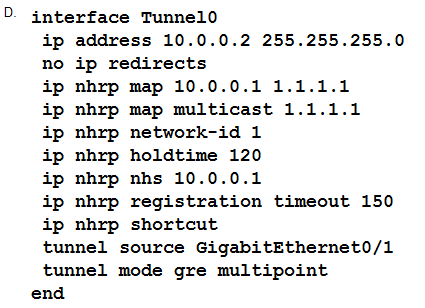
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Explanation:
https://www.globalknowledge.com/us-en/resources/resource-library/articles/understanding-next-
hop-resolution-protocol-commands/
Question 4
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed, which
command is needed for the hub to be able to terminate FlexVPN tunnels?
- A. interface virtual-access
- B. ip nhrp redirect
- C. interface tunnel
- D. interface virtual-template
Answer:
D
Explanation:
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed, the command
that is needed for the hub to be able to terminate FlexVPN tunnels is interface virtual-template. The
interface virtual-template command is used to configure a virtual template interface which provides
a secure tunnel for FlexVPN connections. The other commands listed - interface virtual-access, ip
nhrp redirect, and interface tunnel - are not related to FlexVPN and are not used to terminate
FlexVPN tunnels.
Question 5
Which statement about GETVPN is true?
- A. The configuration that defines which traffic to encrypt originates from the key server.
- B. TEK rekeys can be load-balanced between two key servers operating in COOP.
- C. The pseudotime that is used for replay checking is synchronized via NTP.
- D. Group members must acknowledge all KEK and TEK rekeys, regardless of configuration.
Answer:
A
Explanation:
KS (key server) is ‘caretaker’ of the GM group. Group registrations and authentication of GMs is taken
care of by KS server. Any GM who wants to join the group is required to be successfully authenticated
in the group and sends encryption keys and policy to be used within the group.
===
https://ipwithease.com/introduction-to-getvpn/
Question 6
Refer to the exhibit.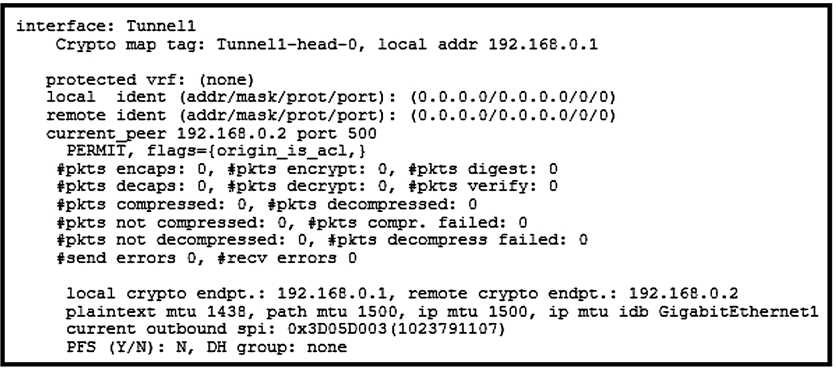
Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
- A. crypto map
- B. DMVPN
- C. GRE
- D. FlexVPN
- E. VTI
Answer:
BE
Question 7
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP
is configured? (Choose two.)
- A. Add NHRP shortcuts on the hub.
- B. Add NHRP redirects on the spoke.
- C. Disable EIGRP next-hop-self on the hub.
- D. Enable EIGRP next-hop-self on the hub.
- E. Add NHRP redirects on the hub.
Answer:
DE
Explanation:
DMVPN disables the EIRGP next-hop-self with "no ip next-hop-self eigrp xxx" in DMVPN phase 2, and
to go from Phase 2 to 3 you need use the NHRP protocol, and again enable EIRGP next-hop-self with
"ip next-hop-self eigrp 134" under the tunnel interface
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_dmvpn/configuration/15-mt/sec-conn-dmvpn-15-mt-book/sec-conn-dmvpn-dmvpn.html#GUID-BF561439-BCC0-4AAF-80D9-1F7876CB7B81
Question 8
Refer to the exhibit.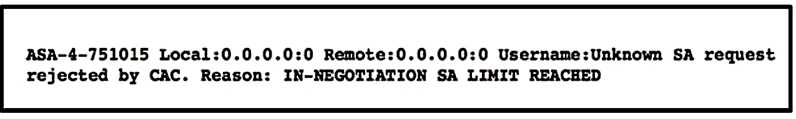
A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based
on the syslog message, which action brings up the VPN tunnel?
- A. Reduce the maximum SA limit on the local Cisco ASA.
- B. Increase the maximum in-negotiation SA limit on the local Cisco ASA.
- C. Remove the maximum SA limit on the remote Cisco ASA.
- D. Correct the crypto access list on both Cisco ASA devices.
Answer:
B
Explanation:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_ikevpn/configuration/xe-3s/sec-ike-for-ipsec-vpns-xe-3s-book/sec-call-addmsn-ike.html
Question 9
Which two parameters help to map a VPN session to a tunnel group without using the tunnel-group
list? (Choose two.)
- A. group-alias
- B. certificate map
- C. optimal gateway selection
- D. group-url
- E. AnyConnect client version
Answer:
AD
Explanation:
https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/98580-enable-group-dropdown.html
Question 10
Which method dynamically installs the network routes for remote tunnel endpoints?
- A. policy-based routing
- B. CEF
- C. reverse route injection
- D. route filtering
Answer:
C
Explanation:
Reverse route injection (RRI) is a method that dynamically installs the network routes for remote
tunnel endpoints. The RRI feature allows the router to automatically learn the routes for the remote
networks and automatically install these routes into the routing table. This eliminates the need for
the administrator to manually configure and maintain the routes for the remote networks. This
feature is commonly used in VPN environments, where the router at the VPN endpoint needs to
learn the routes for the remote networks behind the other VPN endpoint. The other options such as
policy-based routing, CEF, and route filtering are not used to dynamically install the network routes
for remote tunnel endpoints
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/12-4t/sec-vpn-availability-12-4t-book/sec-rev-rte-inject.html
Topic 2, Remote access VPNs
Question 11
Which command identifies a Cisco AnyConnect profile that was uploaded to the flash of an IOS
router?
- A. svc import profile SSL_profile flash:simos-profile.xml
- B. anyconnect profile SSL_profile flash:simos-profile.xml
- C. crypto vpn anyconnect profile SSL_profile flash:simos-profile.xml
- D. webvpn import profile SSL_profile flash:simos-profile.xml
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/anyconnect-secure-mobility-client/200533-AnyConnect-Configure-Basic-SSLVPN-for-I.html
Question 12
Refer to the exhibit.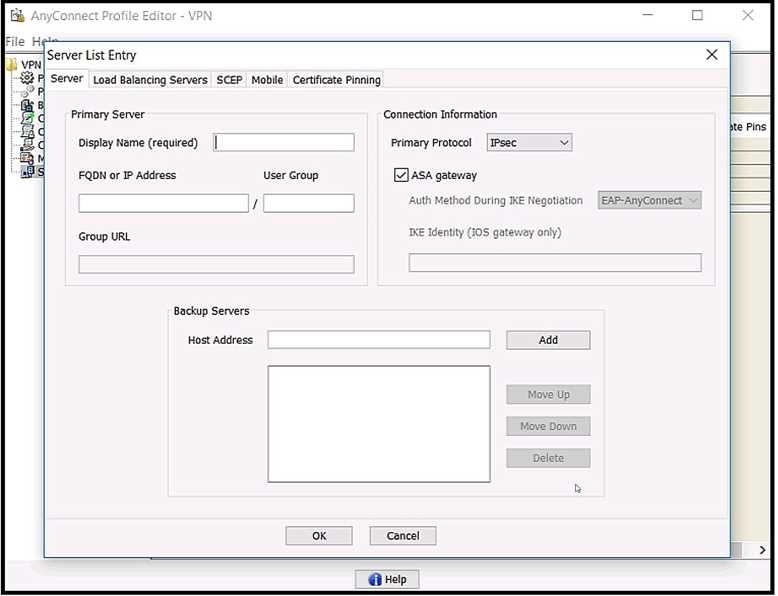
Which value must be configured in the User Group field when the Cisco AnyConnect Profile is created
to connect to an ASA headend with IPsec as the primary protocol?
- A. address-pool
- B. group-alias
- C. group-policy
- D. tunnel-group
Answer:
D
Explanation:
The user group is used in conjunction with Host Address to form a group-based URL. If you specify
the Primary Protocol as IPsec, the User Group must be the exact name of the connection profile
(tunnel group). For SSL, the user group is the group-url of the connection profile.
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect40/administration/guide/b_AnyConnect_Administrator_Guide_4-0/anyconnect-profile-editor.html#ID-1430-
0000026c
Reference: https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect41/administration/guide/b_AnyConnect_Administrator_Guide_4-1/configure-vpn.html
Question 13
Refer to the exhibit.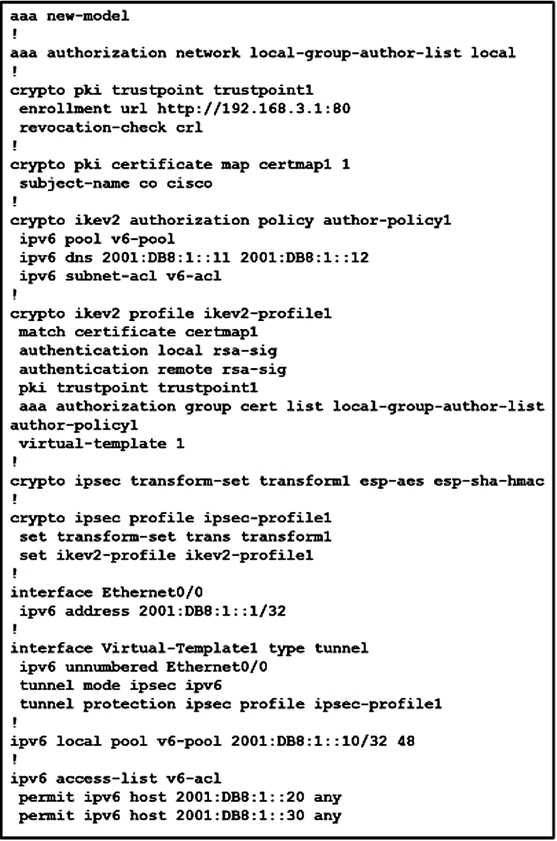
What is configured as a result of this command set?
- A. FlexVPN client profile for IPv6
- B. FlexVPN server to authorize groups by using an IPv6 external AAA
- C. FlexVPN server for an IPv6 dVTI session
- D. FlexVPN server to authenticate IPv6 peers by using EAP
Answer:
C
Explanation:
https://www.cisco.com/c/en/us/support/docs/security/flexvpn/116528-config-flexvpn-00.html
Question 14
Which two types of web resources or protocols are enabled by default on the Cisco ASA Clientless
SSL VPN portal? (Choose two.)
- A. HTTP
- B. ICA (Citrix)
- C. VNC
- D. RDP
- E. CIFS
Answer:
AE
Explanation:
HTTP (Hypertext Transfer Protocol) is used for transferring web resources, such as web pages and
HTML documents, across the internet. CIFS (Common Internet File System) is used for sharing files
and printers between computers on a network. ICA (Citrix), VNC (Virtual Network Computing), and
RDP (Remote Desktop Protocol) are not enabled by default on the Cisco ASA Clientless SSL VPN
portal.
https://www.cisco.com/c/en/us/td/docs/security/asa/asa94/config-guides/cli/vpn/asa-94-vpn-config/webvpn-configure-gateway.html
Question 15
Which configuration construct must be used in a FlexVPN tunnel?
- A. EAP configuration
- B. multipoint GRE tunnel interface
- C. IKEv1 policy
- D. IKEv2 profile
Answer:
D
Explanation:
The correct answer is D. IKEv2 profile. A FlexVPN tunnel requires an IKEv2 profile to define the
parameters for the IKEv2 negotiation and the IPsec security association. The IKEv2 profile references
the IKEv2 keyring, the authentication method, the identity of the peers, and other options.
The IKEv2
profile is then applied to a virtual tunnel interface (VTI) or a dynamic virtual tunnel interface (DVTI)
to protect the tunnel with IPsec12
.
An EAP configuration is used for authentication with Extensible
Authentication Protocol (EAP), which is optional for FlexVPN3
. A multipoint GRE tunnel interface is
used for DMVPN, not FlexVPN. An IKEv1 policy is used for IKEv1, not IKEv2, which is the protocol for
FlexVPN.