cisco 300-720 practice test
securing email with cisco email security appliance (300-720 sesa)
Question 1
An administrator manipulated the subnet mask but was still unable to access the user interface. How must the administrator access the appliance to perform the initial configuration?
- A. Use the data 2 port.
- B. Use the serial or console port.
- C. Use the data 1 port.
- D. Use the management port.
Answer:
b
Question 2
What are two phases of the Cisco ESA email pipeline? (Choose two.)
- A. reject
- B. workqueue
- C. action
- D. delivery
- E. quarantine
Answer:
bd
Reference:
https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-1/user_guide/b_ESA_Admin_Guide_12_1/b_ESA_Admin_Guide_12_1_chapter_011.pdf
(p.1)
Question 3
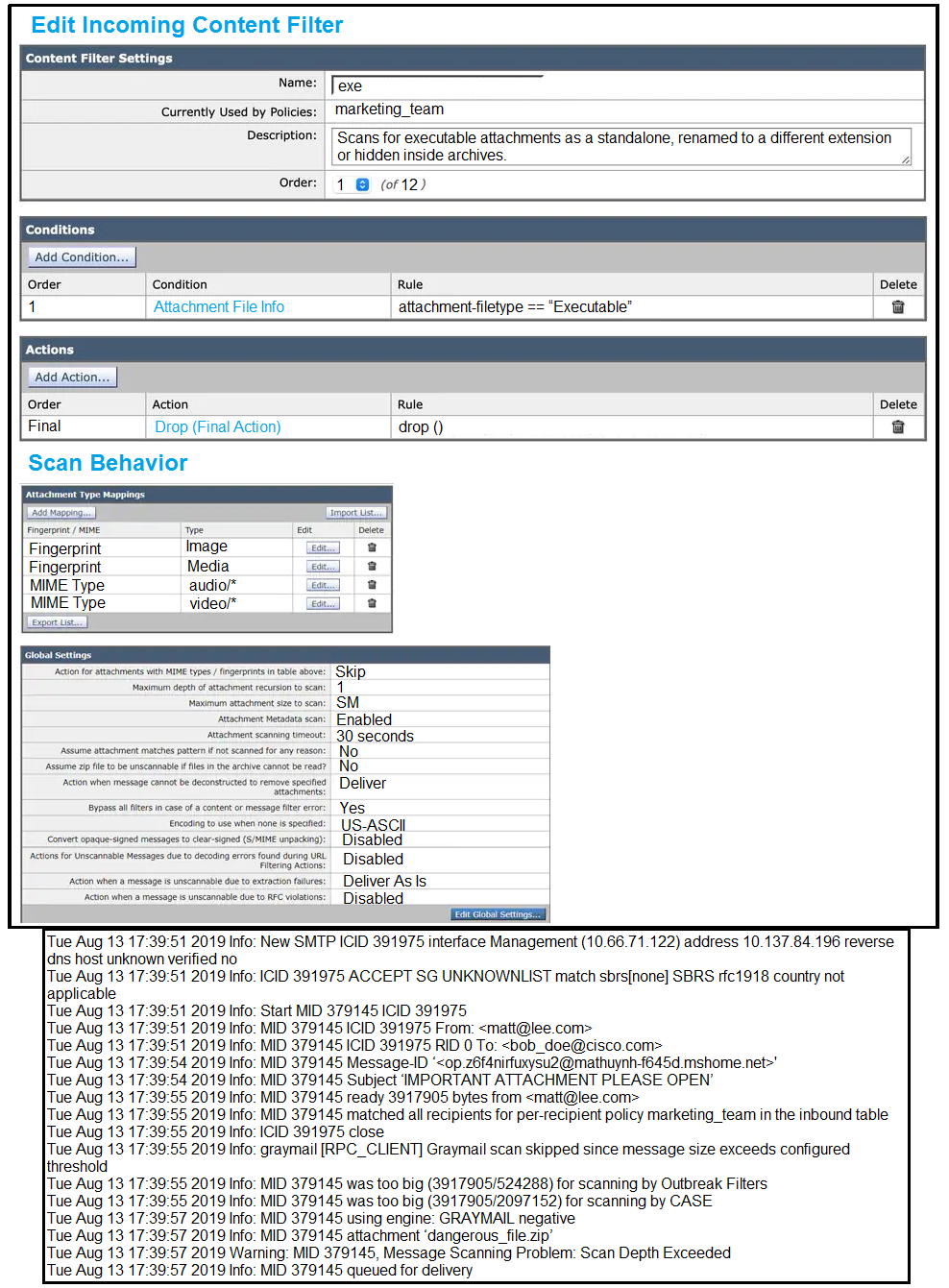
Refer to the exhibit. Which configuration allows the Cisco ESA to scan for executables inside the zip and apply the action as per the content filter?
- A. Modify the content filter to look for .exe filename instead of executable filetype.
- B. Configure the recursion depth to a higher value.
- C. Configure the maximum attachment size to a higher value.
- D. Modify the content filter to look for attachment filetype of compressed.
Answer:
c
Question 4
An administrator notices that the Cisco ESA delivery queue is consistently full. After further investigation, it is determined that the IP addresses currently in use by the Cisco ESA are being rate-limited by some destinations. The administrator creates a new interface with an additional IP address using virtual gateway technology, but the issue is not solved. Which configuration change resolves the issue?
- A. Use the CLI command alt-src-host to set the new interface as a possible delivery candidate.
- B. Use the CLI command loadbalance auto to enable mail delivery over all interfaces.
- C. Use the CLI command deliveryconfig to set the new interface as the primary interface for mail delivery.
- D. Use the CLI command altsrchost to set the new interface as the source IP address for all mail.
Answer:
b
Question 5
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
- A. Enable outbreak filters.
- B. Enable email relay.
- C. Enable antispam scanning.
- D. Enable port bouncing.
- E. Enable antivirus scanning.
Answer:
ac
Reference:
https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-0/user_guide/b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_chapter_01111.html
Question 6
Which setting affects the aggressiveness of spam detection?
- A. protection level
- B. spam threshold
- C. spam timeout
- D. maximum depth of recursion scan
Answer:
b
Reference:
https://www.cisco.com/c/en/us/support/docs/security/email-security-appliance/118220-technote-esa-00.html
Question 7
What is the default behavior of any listener for TLS communication?
- A. preferred-verify
- B. off
- C. preferred
- D. required
Answer:
b
Reference:
https://www.cisco.com/c/en/us/support/docs/security/email-security-appliance/118954-config-esa-00.html
Question 8
What is the purpose of checking the CRL during SMTP authentication on a Cisco ESA?
- A. Check if the certificate is not revoked.
- B. Confirm that corresponding CA is present.
- C. Verify the common name matches user ID.
- D. Validate the date to check if the certificate is still valid.
Answer:
a
Question 9
How does the graymail safe unsubscribe feature function?
- A. It strips the malicious content of the URI before unsubscribing.
- B. It checks the URI reputation and category and allows the content filter to take an action on it.
- C. It redirects the end user who clicks the unsubscribe button to a sandbox environment to allow a safe unsubscribe.
- D. It checks the reputation of the URI and performs the unsubscribe process on behalf of the end user.
Answer:
d
Reference:
https://www.cisco.com/c/en/us/support/docs/security/email-security-appliance/200383-Graymail-Detection-and-Safe-Unsubscribin.html
Question 10
A company security policy requires that the finance department have an easy way to apply encryption to their outbound messages that contain sensitive data. Users must be able to flag the messages that require encryption versus a Cisco ESA scanning all messages and automatically encrypting via detection. Which action enables this capability?
- A. Create an outgoing content filter with no conditions and with the Encrypt and Deliver Now action configured with [SECURE] in the Subject setting.
- B. Create a DLP policy manager message action with encryption enabled and apply it to active DLP policies for outgoing mail.
- C. Create an encryption profile with [SECURE] in the Subject setting and enable encryption on the mail flow policy.
- D. Create an encryption profile and an outgoing content filter that includes \[SECURE\] within the Subject Header: Contains condition along with the Encrypt and Deliver Now action.
Answer:
d