cisco 300-715 practice test
Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)
Question 1
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose
two)
- A. updates
- B. remediation actions
- C. Client Provisioning portal
- D. conditions
- E. access policy
Answer:
B, D
Question 2
What is a method for transporting security group tags throughout the network?
- A. by enabling 802.1AE on every network device
- B. by the Security Group Tag Exchange Protocol
- C. by embedding the security group tag in the IP header
- D. by embedding the security group tag in the 802.1Q header
Answer:
B
Question 3
Which two ports must be open between Cisco ISE and the client when you configure posture on Cisco
ISE? (Choose two).
- A. TCP 8443
- B. TCP 8906
- C. TCP 443
- D. TCP 80
- E. TCP 8905
Answer:
A, E
Question 4
Which profiling probe collects the user-agent string?
- A. DHCP
- B. AD
- C. HTTP
- D. NMAP
Answer:
C
Question 5
Which supplicant(s) and server(s) are capable of supporting EAP-CHAINING?
- A. Cisco AnyConnect NAM and Cisco Identity Service Engine
- B. Cisco AnyConnect NAM and Cisco Access Control Server
- C. Cisco Secure Services Client and Cisco Access Control Server
- D. Windows Native Supplicant and Cisco Identity Service Engine
Answer:
A
Question 6
Which two values are compared by the binary comparison (unction in authentication that is based on
Active Directory?
- A. subject alternative name and the common name
- B. MS-CHAPv2 provided machine credentials and credentials stored in Active Directory
- C. user-presented password hash and a hash stored in Active Directory
- D. user-presented certificate and a certificate stored in Active Directory
Answer:
A
Explanation:
Basic certificate checking does not require an identity source. If you want binary comparison
checking for the certificates, you must select an identity source. If you select Active Directory as an
identity source, subject and common name and subject alternative name (all values) can be used
to
look
up
a
user.
https://www.cisco.com/c/en/us/td/docs/security/ise/1-3/admin_guide/b_ise_admin_guide_13/b_ise_admin_guide_sample_chapter_01110.html
Question 7
Which three default endpoint identity groups does cisco ISE create? (Choose three)
- A. Unknown
- B. whitelist
- C. end point
- D. profiled
- E. blacklist
Answer:
A, D , E
Explanation:
Default Endpoint Identity Groups Created for Endpoints
Cisco ISE creates the following five endpoint identity groups by default: Blacklist, GuestEndpoints,
Profiled, RegisteredDevices, and Unknown. In addition, it creates two more identity groups, such as
Cisco-IP-Phone and Workstation, which are associated to the Profiled (parent) identity group. A
parent group is the default identity group that exists in the system.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_010101.html#ID1678
Question 8
DRAG DROP
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.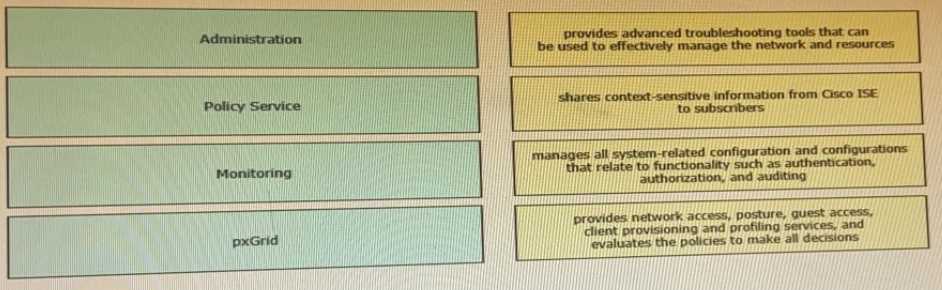
Answer:

Monitoring = provides advanced monitoring and troubleshooting tools that you can use to effectively
manage your network and resources
Policy Service = provides network access, posture, guest access, client provisioning, and profiling
services. This persona evaluates the policies and makes all the decisions.
Administration = manages all system-related configuration and configurations that relate to
functionality such as authentication, authorization, auditing, and so on
pxGrid = shares context-sensitive information from Cisco ISE to subscribers
//www.cisco.com/c/en/us/td/docs/security/ise/1-
4/admin_guide/b_ise_admin_guide_14/b_ise_admin_guide_14_chapter_011.html#ID57
Question 9
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting
to the network?
- A. personas
- B. qualys
- C. nexpose
- D. posture
Answer:
D
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010110.html
Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state,
also known as posture, of all the endpoints that are connecting to a network for compliance with
corporate security policies. This allows you to control clients to access protected areas of a network.
Question 10
Which default endpoint identity group does an endpoint that does not match any profile in Cisco ISE
become a member of?
- A. Endpoint
- B. unknown
- C. blacklist
- D. white list
- E. profiled
Answer:
B
Explanation:
If you do not have a matching profiling policy, you can assign an unknown profiling policy. The
endpoint is therefore profiled as Unknown. The endpoint that does not match any profile is grouped
within the Unknown identity group. The endpoint profiled to the Unknown profile requires that you
create a profile with an attribute or a set of attributes collected for that endpoint.
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_identities.html
Question 11
Refer to the exhibit: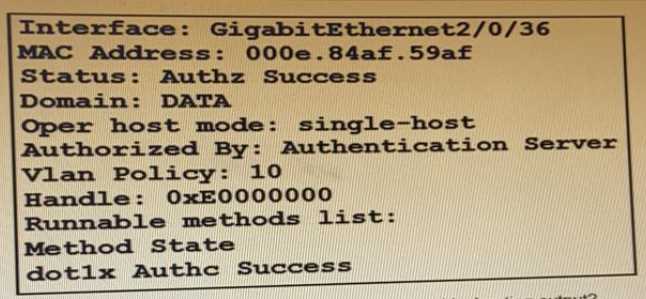
Which command is typed within the CU of a switch to view the troubleshooting output?
- A. show authentication sessions mac 000e.84af.59af details
- B. show authentication registrations
- C. show authentication interface gigabitethemet2/0/36
- D. show authentication sessions method
Answer:
A
Question 12
What must be configured on the Cisco ISE authentication policy for unknown MAC
addresses/identities for successful authentication?
- A. pass
- B. reject
- C. drop
- D. continue
Answer:
D
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_id_stores.html
Question 13
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so
that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
- A. NetFlow
- B. SNMP
- C. HTTP
- D. DHCP
- E. RADIUS
Answer:
D, E
Explanation:
Cisco ISE implements an ARP cache in the profiling service, so that you can reliably map the IP
addresses and the MAC addresses of endpoints. For the ARP cache to function, you must enable
either the DHCP probe or the RADIUS probe. The DHCP and RADIUS probes carry the IP addresses
and the MAC addresses of endpoints in the payload data. The dhcp-requested address attribute in
the DHCP probe and the Framed-IP-address attribute in the RADIUS probe carry the IP addresses of
endpoints, along with their MAC addresses, which can be mapped and stored in the ARP cache.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010100.html
Question 14
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from
the Cisco ISE node?
- A. session timeout
- B. idle timeout
- C. radius-server timeout
- D. termination-action
Answer:
B
Explanation:
When the inactivity timer is enabled, the switch monitors the activity from authenticated endpoints.
When the inactivity timer expires, the switch removes the authenticated session. The inactivity timer
for MAB can be statically configured on the switch port, or it can be dynamically assigned using the
RADIUS Idle-Timeout attribute
Question 15
What must match between Cisco ISE and the network access device to successfully authenticate
endpoints?
- A. SNMP version
- B. shared secret
- C. certificate
- D. profile
Answer:
B
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_network_devices.html