cisco 300-710 practice test
securing networks with cisco firepower (300-710 sncf)
Question 1
An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside interfaces to the outside interfaces. They are unable to gather information about neighboring Cisco devices or use multicast in their environment. What must be done to resolve this issue?
- A. Create a firewall rule to allow CDP traffic
- B. Create a bridge group with the firewall interfaces
- C. Change the firewall mode to transparent
- D. Change the firewall mode to routed
Answer:
d
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/623/configuration/guide/fpmc-config-guide-v623/ transparent_or_routed_firewall_mode_for_firepower_threat_defense.html
Question 2
A security engineer is adding three Cisco FTD devices to a Cisco FMC. Two of the devices have successfully registered to the Cisco FMC. The device that is unable to register is located behind a router that translates all outbound traffic to the routers WAN IP address. Which two steps are required for this device to register to the Cisco FMC? (Choose two.)
- A. Reconfigure the Cisco FMC to use the devices private IP address instead of the WAN address.
- B. Configure a NAT ID on both the Cisco FMC and the device.
- C. Reconfigure the Cisco FMC to use the devices hostname instead of IP address.
- D. Remove the IP address defined for the device in the Cisco FMC.
- E. Add the port number being used for PAT on the router to the devices IP address in the Cisco FMC.
Answer:
bd
Question 3
Encrypted Visibility Engine (EVE) is enabled under which tab on an access control policy in Cisco Secure Firewall Management Center?
- A. Network Analysis Policy
- B. SSL
- C. Advanced
- D. Security Intelligence
Answer:
c
Question 4
An engineer is configuring multiple Cisco FTD appliances for use in the network. Which rule must the engineer follow while defining interface objects in Cisco FMC for use with interfaces across multiple devices?
- A. Two security zones can contain the same interface.
- B. Interface groups can contain interfaces from many devices.
- C. An interface cannot belong to a security zone and an interface group.
- D. Interface groups can contain multiple interface types.
Answer:
c
Question 5
Due to an increase in malicious events, a security engineer must generate a threat report to include intrusion events, malware events, and security intelligence events. How is this information collected in a single report?
- A. Run the default Firepower report.
- B. Create a Custom report.
- C. Generate a malware report.
- D. Export the Attacks Risk report.
Answer:
b
Question 6
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
- A. transparent inline mode
- B. TAP mode
- C. strict TCP enforcement
- D. propagate link state
Answer:
d
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/ inline_sets_and_passive_interfaces_for_firepower_threat_defense.html
Question 7
An engineer configures an access control rule that deploys file policy configurations to security zone or tunnel zones, and it causes the device to restart. What is the reason for the restart?
- A. Source or destination security zones in the access control rule matches the security zones that are associated with interfaces on the target devices.
- B. The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the destination policy.
- C. Source or destination security zones in the source tunnel zone do not match the security zones that are associated with interfaces on the target devices.
- D. The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the source policy.
Answer:
a
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/623/configuration/guide/fpmc-config-guide-v623/policy_management.html
Question 8
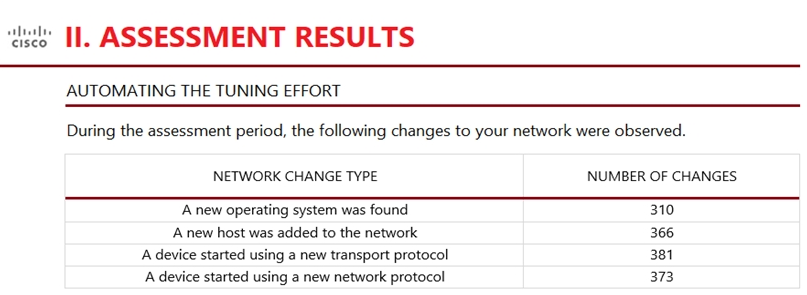
Refer to the exhibit. An engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network. How is the Firepower configuration updated to protect these new operating systems?
- A. The administrator manually updates the policies.
- B. The administrator requests a Remediation Recommendation Report from Cisco Firepower.
- C. Cisco Firepower gives recommendations to update the policies.
- D. Cisco Firepower automatically updates the policies.
Answer:
c
Question 9
An engineer is troubleshooting a file that is being blocked by a Cisco FTD device on the network. The user is reporting that the file is not malicious. Which action does the engineer take to identify the file and validate whether or not it is malicious?
- A. Identify the file in the intrusion events and submit it to Threat Grid for analysis.
- B. Use FMC file analysis to look for the file and select Analyze to determine its disposition.
- C. Use the context explorer to find the file and download it to the local machine for investigation.
- D. Right click the connection event and send the file to AMP for Endpoints to see if the hash is malicious.
Answer:
a
Question 10
Which command is run on an FTD unit to associate the unit to an FMC manager that is at IP address 10.0.0.10, and that has the registration key Cisco123?
- A. configure manager local 10.0.0.10 Cisco123
- B. configure manager add Cisco123 10.0.0.10
- C. configure manager local Cisco123 10.0.0.10
- D. configure manager add 10.0.0.10 Cisco123
Answer:
d
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/misc/fmc-ftd-mgmt-nw/fmc-ftd-mgmt-nw.html#id_106101