cisco 300-215 practice test
conducting forensic analysis and incident response using cisco cyberops technologies (cbrfir)
Question 1
What are YARA rules based upon?
- A. binary patterns
- B. HTML code
- C. network artifacts
- D. IP addresses
Answer:
a
Reference:
https://en.wikipedia.org/wiki/YARA#:~:text=YARA%20is%20the%20name%20of,strings%20and%20a%20boolean%20expression
.
Question 2
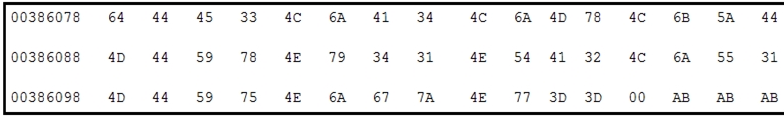
Refer to the exhibit. Which encoding technique is represented by this HEX string?
- A. Unicode
- B. Binary
- C. Base64
- D. Charcode
Answer:
b
Reference:
https://www.suse.com/c/making-sense-hexdump/
Question 3
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
- A. Introduce a priority rating for incident response workloads.
- B. Provide phishing awareness training for the fill security team.
- C. Conduct a risk audit of the incident response workflow.
- D. Create an executive team delegation plan.
- E. Automate security alert timeframes with escalation triggers.
Answer:
ae
Question 4
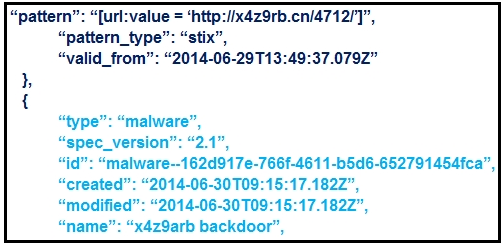
Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?
- A. malware; "http://x4z9arb.cn/4712/'
- B. malware; x4z9arb backdoor
- C. x4z9arb backdoor; http://x4z9arb.cn/4712/
- D. malware; malware--162d917e-766f-4611-b5d6-652791454fca
- E. stix; "http://x4z9arb.cn/4712/'
Answer:
d
Question 5
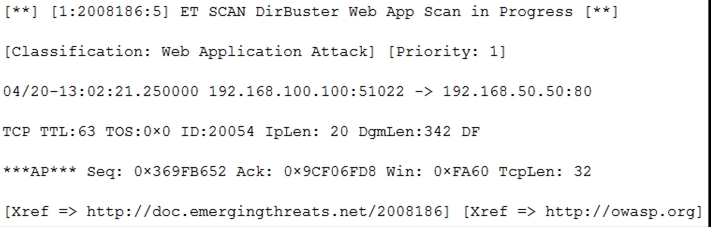
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?
- A. brute-force attack against the web application user accounts
- B. XSS attack against the target webserver
- C. brute-force attack against directories and files on the target webserver
- D. SQL injection attack against the target webserver
Answer:
c
Question 6

Refer to the exhibit. Which type of code is being used?
- A. Shell
- B. VBScript
- C. BASH
- D. Python
Answer:
d
Question 7
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
- A. Restore to a system recovery point.
- B. Replace the faulty CPU.
- C. Disconnect from the network.
- D. Format the workstation drives.
- E. Take an image of the workstation.
Answer:
ae
Question 8
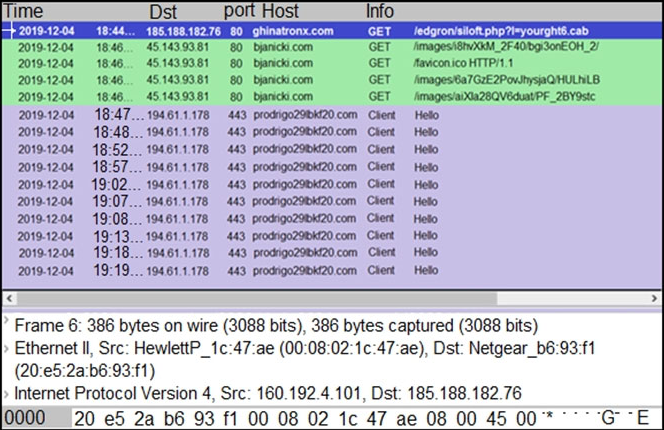
Refer to the exhibit. A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
- A. http.request.un matches
- B. tls.handshake.type ==1
- C. tcp.port eq 25
- D. tcp.window_size ==0
Answer:
b
Reference:
https://www.malware-traffic-analysis.net/2018/11/08/index.html https://unit42.paloaltonetworks.com/wireshark-tutorial-examining-ursnif-infections/
Question 9
An employee receives an email from a trusted person containing a hyperlink that is malvertising. The employee clicks the link and the malware downloads. An information analyst observes an alert at the SIEM and engages the cybersecurity team to conduct an analysis of this incident in accordance with the incident response plan. Which event detail should be included in this root cause analysis?
- A. phishing email sent to the victim
- B. alarm raised by the SIEM
- C. information from the email header
- D. alert identified by the cybersecurity team
Answer:
b
Question 10
What is the steganography anti-forensics technique?
- A. hiding a section of a malicious file in unused areas of a file
- B. changing the file header of a malicious file to another file type
- C. sending malicious files over a public network by encapsulation
- D. concealing malicious files in ordinary or unsuspecting places
Answer:
a
https://blog.eccouncil.org/6-anti-forensic-techniques-that-every-cyber-investigator-dreads/