cisco 200-901 practice test
DevNet Associate (DEVASC)
Question 1
Which type of threat occur when an attacker can send hostile data to an interpreter within an
application?
- A. Cross-site scripting
- B. Sensitive data exposure
- C. Broken authentication
- D. Injection
Answer:
D
Explanation:
Injection attacks occur when untrusted data is sent to an interpreter as part of a command or query.
The attacker's hostile data can trick the interpreter into executing unintended commands or
accessing data without proper authorization. Common types of injection attacks include SQL
injection, command injection, and LDAP injection. These types of attacks exploit vulnerabilities in
how an application processes input data, allowing attackers to inject malicious commands or queries
into the system.
Reference:
Cisco DevNet Associate Certification Guide: Chapter on Security, specifically on common web
application vulnerabilities.
OWASP (Open Web Application Security Project) Top Ten Web Application Security Risks: Injection.
Question 2
Refer to the exhibit.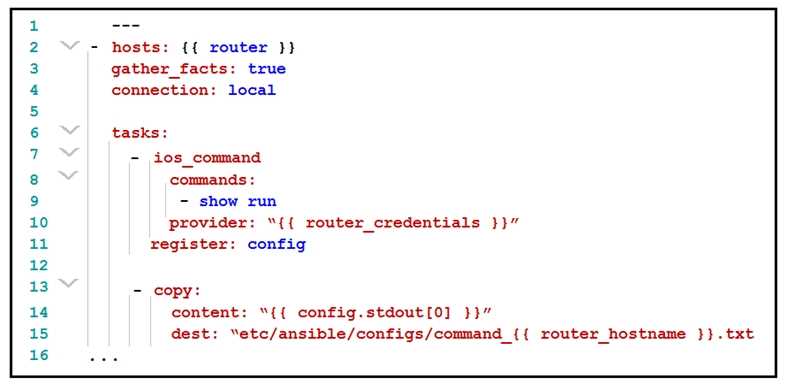
What is the effect of this Ansible playbook on an IOS router?
- A. A new running configuration is pushed to the IOS router.
- B. The current running configuration of the IOS router is backed up.
- C. The start-up configuration of the IOS router is copied to a local folder.
- D. A new start-up configuration is copied to the IOS router.
Answer:
B
Explanation:
The provided Ansible playbook is designed to connect to an IOS router and execute the "show run"
command to retrieve the current running configuration. The configuration is then registered in a
variable called config. The next task copies the output stored in the config variable to a file in a
specified directory on the local machine. The file is named based on the router's hostname.
Here are the steps:
Define the hosts: The playbook targets the {{ router }} group or host.
Gather facts: Enabled with gather_facts: true to collect useful information about the target devices.
Connection type: Local, meaning the playbook runs on the local machine where Ansible is invoked.
Task 1 - ios_command:
Executes the "show run" command.
Uses the provided router credentials.
Registers the command output to the config variable.
Task 2 - copy:
Takes the first element from config.stdout (the output of the "show run" command).
Copies this content to a file in /etc/ansible/configs/, naming the file command_{{ router_hostname
}}.txt.
Reference:
Cisco DevNet Associate Certification Guide: Chapter on Automation and Programmability, specifically
on using Ansible for network automation.
Ansible Documentation: Module ios_command and copy.
Question 3
Which two statement describe the role of an artifact repository in a CI/CD pipeline? (Choose two.)
- A. An artifact repository allows to compare and merge changes in the source code of files involved in a build process.
- B. An artifact repository is needed only for CI/CD pipeline executed on a public cloud infrastructure.
- C. An artifact repository provides traceability, search, and management of binary files.
- D. An artifact repository is needed only for managing open source software.
- E. An artifact repository stores files needed and generated during the build process.
Answer:
CE
Explanation:
An artifact repository is a key component in a CI/CD pipeline, used to manage binary files and other
artifacts produced and consumed during the build process. It helps in organizing and tracking these
artifacts through various stages of the pipeline.
Provides Traceability, Search, and Management of Binary Files:
Artifact repositories store binary files and metadata, allowing developers to trace back to the source
and understand the context in which an artifact was produced.
These repositories often come with search functionalities to locate specific versions of binaries
quickly.
Examples include JFrog Artifactory, Nexus Repository, and AWS CodeArtifact.
Stores Files Needed and Generated During the Build Process:
Artifact repositories store intermediate and final build outputs, dependencies, libraries, and other
necessary files.
These repositories support the storage and distribution of build artifacts, ensuring consistent
deployment in different environments (e.g., staging, production).
Reference:
Cisco DevNet Associate Certification Guide: Chapter on CI/CD pipeline tools and practices.
General CI/CD documentation and best practices from continuous integration and delivery tools
(e.g., Jenkins, GitLab CI/CD).
Question 4
DRAG DROP
Drag and drop the network component names from the left onto the correct descriptions on the
right. Not all options are used.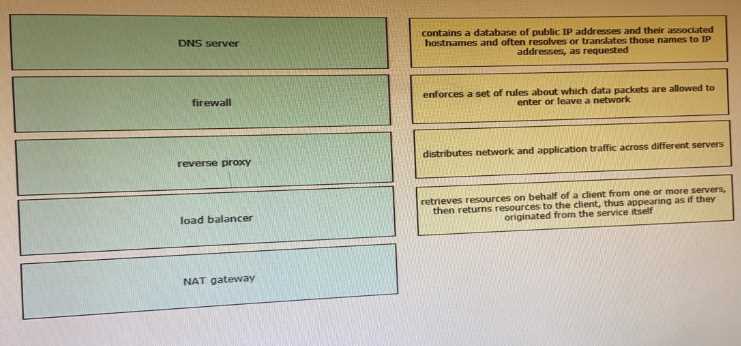
Answer:
Explanation:
1 – A, 2 – B, 3 – D, 4 – C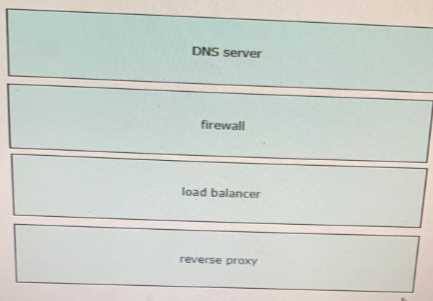
Question 5
What is the purpose of the Cisco VIRL software tool?
- A. To verify configurations against compliance standards
- B. To simulate and model networks
- C. To automate API workflows
- D. To test performance of an application
Answer:
B
Explanation:
Reference:
https://www.speaknetworks.com/cisco-virl-better-gns3/
Cisco VIRL (Virtual Internet Routing Lab) is a powerful network simulation platform designed to
simulate and model networks. It allows users to create and test network topologies, run simulations,
and visualize network behavior in a controlled virtual environment. This tool is particularly valuable
for network engineers and administrators to test configurations, troubleshoot issues, and validate
network designs without the need for physical hardware.
Reference: Cisco VIRL Overview
Question 6
Which detail is included in a routing table?
- A. IP protocol
- B. Broadcast address
- C. TCP or UDP port number
- D. Destination next hop or outgoing interface
Answer:
D
Explanation:
A routing table contains critical information used by routers to determine the best path for
forwarding packets. The essential details included in a routing table are:
Destination network: The IP address of the destination network.
Next hop: The IP address of the next hop router or the outgoing interface to reach the destination
network.
Metric: The cost associated with the path to the destination network, used to select the best route.
Route type: The type of route (e.g., directly connected, static, dynamic).
Reference: Cisco Routing Table Information
Question 7
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco
DNA center API.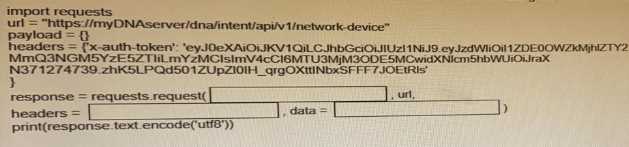
Answer:
“GET”,
headers, payload
Explanation:
This Python script uses the Cisco DNA Center API to retrieve a list of network devices. The steps are:
Import the required libraries: requests for making HTTP requests and json for handling JSON data.
Define the API endpoint URL for retrieving network devices from Cisco DNA Center.
Set up the request headers, including the content type and the authentication token (X-Auth-Token).
Send a GET request to the API endpoint.
Check the response status code to ensure the request was successful.
If successful, parse and print the JSON response containing the list of network devices. Otherwise,
print an error message.
Reference: Cisco DNA Center API Documentation
Solution as below.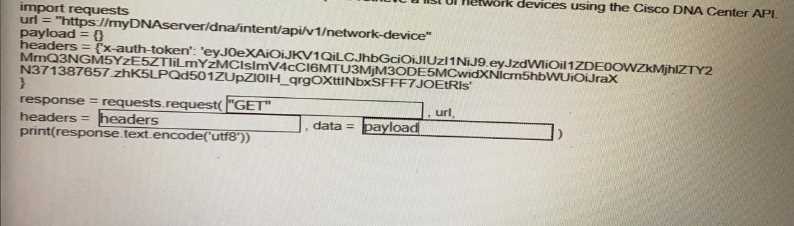
Question 8
Which statement about authentication a RESTCONF API session with a router that runs Cisco IOS XE
software is true?
- A. OAuth must be used.
- B. A token must be retrieved and the associated string must be embedded in the X-Auth-Token header.
- C. Basic authentication must be used.
- D. No authentication is required.
Answer:
C
Explanation:
When authenticating a RESTCONF API session with a router running Cisco IOS XE software, basic
authentication is commonly used. Basic authentication involves sending the username and password
in the HTTP header encoded in base64 format. This method is straightforward and widely supported,
though it is less secure compared to token-based authentication and should be used with HTTPS to
ensure the credentials are encrypted in transit.
Reference: Cisco RESTCONF API Documentation
Question 9
Which mechanism is used to consume a RESTful API design when large amounts of data are
returned?
- A. Data sets
- B. Scrolling
- C. Blobs
- D. Pagination
Answer:
D
Explanation:
When consuming a RESTful API that returns large amounts of data, pagination is commonly used to
divide the data into manageable chunks. Pagination helps reduce the load on the server and the
client by providing only a subset of the total data in each response. The client can request the next
set of data using parameters such as page or limit.
Reference:
Cisco DevNet Associate Certification Guide: Chapter on API Design and RESTful Services, specifically
on handling large data sets.
REST API documentation standards such as those from the OpenAPI Initiative and best practices.
Question 10
Which action does the Git command git merge allow the development to perform?
- A. Combine multiple sequence of commits into one unified history.
- B. Push changes to the remote repository
- C. Switch between branches
- D. Create, list, rename, and delete branches
Answer:
A
Explanation:
Reference:
https://www.atlassian.com/git/tutorials/using-branches/git-merge
The git merge command is used to combine the changes from one branch into another. This
command takes the contents of a source branch and integrates it with the target branch, effectively
merging the history of commits from both branches into one unified history.
Reference:
Cisco DevNet Associate Certification Guide: Chapter on Source Control with Git, specifically on
branch management and merging.
Git documentation: git merge command usage and examples.
Question 11
Refer to the exhibit.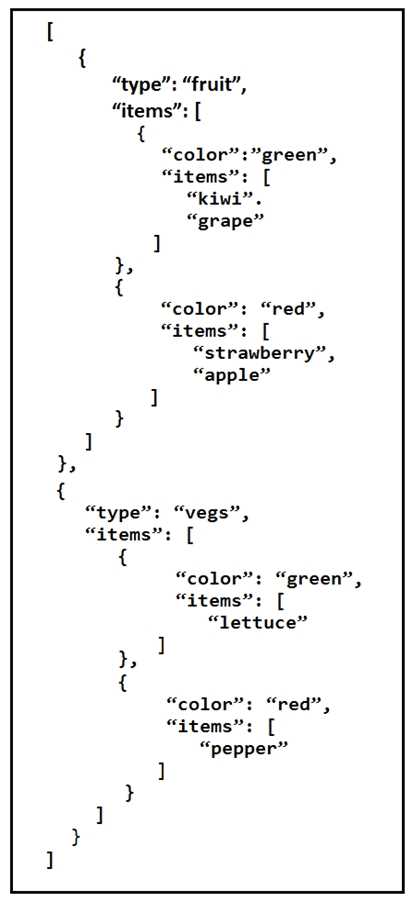
A REST API retune this JSON output for a GET HTTP request, Which has assigned to a variable called
“vegetables” Using python, which output is the result of this command?
- A. Lettuce
- B. Kiwi
- C. [‘kiwi’, ‘grape’]
- D. {‘color’: ‘green’, ‘items’: [‘kiwi’, ‘grape’]
Answer:
B
Explanation:
Understand the JSON Structure: The JSON data given in the exhibit consists of an array of objects.
Each object has a type and an items key. The items key contains an array of objects, each with a color
and another items key, which is an array of strings representing items of that color.
Analyze the Python Code: The Python code provided is:
print(filter(lambda l: l['type'] == 'fruit', vegetables)[0]['items'][0]['items'][0])
Break Down the Code:
filter(lambda l: l['type'] == 'fruit', vegetables): This line filters the JSON array vegetables to include
only objects where the type is 'fruit'.
filter(...)[0]: After filtering, this selects the first object in the filtered list, which is the fruit object.
['items'][0]: This accesses the first item in the items array of the fruit object. In this case, it refers to
the object where color is "green".
['items'][0]: This accesses the first item in the items array of the green object, which is "kiwi".
Evaluate the Code:
The first object of type fruit in the JSON is found.
The first item in the items array for fruit with the color green is selected.
The first item in this nested items array is "kiwi".
Therefore, the output of the given Python command is "Kiwi".
Reference:
Python documentation on filter:
Python Docs - Filter
JSON structure understanding from DevNet Associate study materials on API interactions and data
parsing.
Question 12
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
- A. 400
- B. 403
- C. 405
- D. 429
Answer:
A
Explanation:
The HTTP status code 400 (Bad Request) is used by a REST API to indicate that the server cannot or
will not process the request due to something that is perceived to be a client error (e.g., malformed
request syntax, invalid request message framing, or deceptive request routing).
Reference:
Cisco DevNet Associate Certification Guide: Chapter on RESTful APIs and HTTP methods, specifically
on status codes.
HTTP/1.1 documentation: Status Code Definitions from the W3C.
Question 13
What is the purpose of a MAC address?
- A. To uniquely identify a router in a LAN
- B. To uniquely identify a network interface in a LAN
- C. To uniquely identify a device on the internet
- D. To uniquely identify a switch in a LAN
Answer:
B
Explanation:
A MAC (Media Access Control) address is a unique identifier assigned to a network interface card
(NIC) for communications at the data link layer of a network segment. MAC addresses are used
within local area networks (LANs) to ensure that data packets are delivered to the correct hardware
device. Every network interface on a device, such as a computer, router, or switch, has a unique MAC
address.
Reference: Cisco - MAC Addresses
Question 14
Which way should be used to safely the API keys?
- A. In an environment variable unique to the system database
- B. Encrypted in a configuration file that is separate from the code
- C. Encrypted in the code in a function
- D. Plain text in the code as a constant
Answer:
B
Explanation:
API keys should be stored securely to prevent unauthorized access. The best practice is to store them
encrypted in a configuration file that is separate from the code. This approach ensures that sensitive
information is not hardcoded in the source code, which could be exposed through version control or
other means. Keeping API keys in encrypted configuration files also allows for better management
and updating of keys without changing the application code.
Reference: Cisco Secure Coding Practices
Question 15
Refer to the exhibit.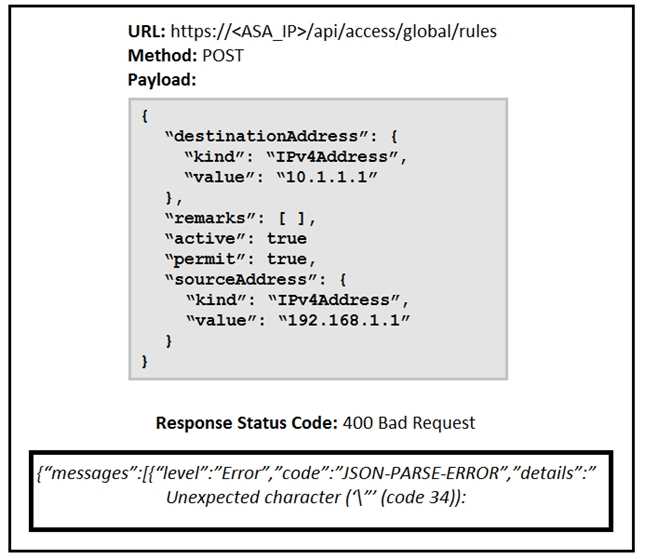
What caused the error in this API request?
- A. The API resource does not support the POST operation
- B. The API resource does not support JSON format payloads.
- C. The submitted JSON payload includes a field that is not supported by the API resource.
- D. The submitted JSON payload has a formatting issue
Answer:
D
Explanation:
The error message "JSON-PARSE-ERROR" and "Unexpected character ('"' (code 34))" indicates a
problem with the formatting of the JSON payload. Specifically, there are likely incorrect characters or
misplaced quotes within the JSON structure. JSON formatting issues are common errors that can
occur due to syntax mistakes such as missing commas, incorrect braces, or invalid characters.
To resolve this, carefully check the JSON structure for proper formatting, ensuring all fields are
correctly defined and that syntax rules are followed.
Reference: Cisco API Troubleshooting