cisco 200-201 practice test
understanding cisco cybersecurity operations fundamentals (cbrops)
Question 1
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
- A. social engineering
- B. eavesdropping
- C. piggybacking
- D. tailgating
Answer:
a
Question 2
What is the difference between inline traffic interrogation and traffic mirroring?
- A. Inline replicates the traffic to preserve integrity rather than modifying packets before sending them to other analysis tools.
- B. Traffic mirroring results in faster traffic analysis and inline is considerably slower due to latency.
- C. Inline interrogation is less complex as traffic mirroring applies additional tags to data.
- D. Traffic mirroring copies the traffic rather than forwarding it directly to the analysis tools.
Answer:
d
Question 3
Which regular expression matches color and colour?
- A. colo?ur
- B. col[08]+our
- C. colou?r
- D. col[09]+our
Answer:
c
Question 4
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within
48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
- A. company assets that are threatened
- B. customer assets that are threatened
- C. perpetrators of the attack
- D. victims of the attack
Answer:
c
Question 5
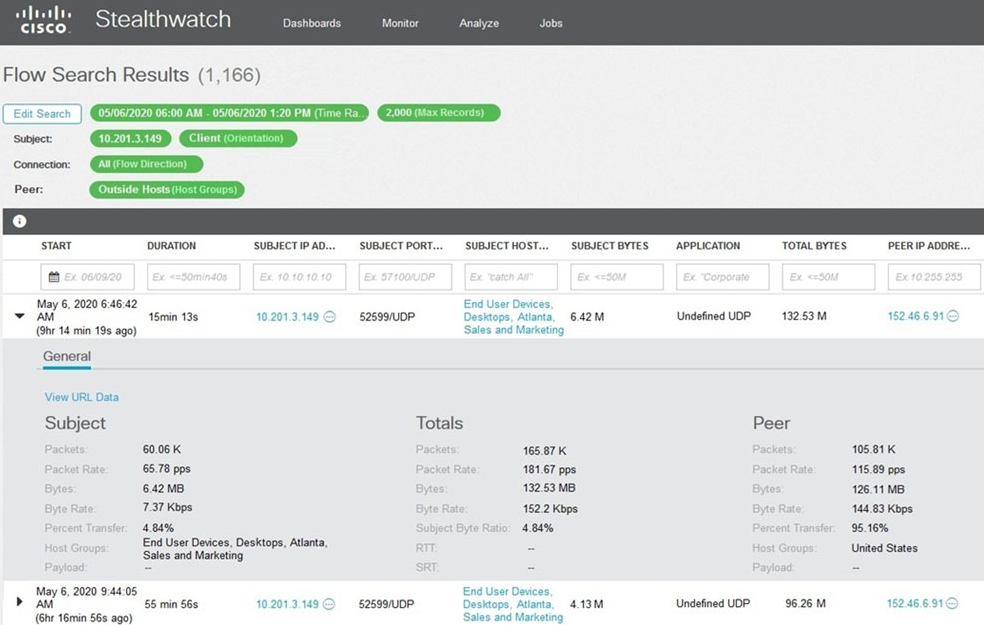
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
- A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
- B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
- C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
- D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
Answer:
d
Question 6
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
- A. detection and analysis
- B. post-incident activity
- C. vulnerability management
- D. risk assessment
- E. vulnerability scoring
Answer:
ab
Reference:
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Question 7
What describes the impact of false-positive alerts compared to false-negative alerts?
- A. A false negative is alerting for an XSS attack. An engineer investigates the alert and discovers that an XSS attack happened. A false positive is when an XSS attack happens and no alert is raised.
- B. A false positive is an event altering for an SQL injection attack. An engineer investigates the alert and discovers that an attack attempt was blocked by IPS. A false negative is when the attack gets detected but succeeds and results in a breach.
- C. A false positive is an event altering for a brute-force attack. An engineer investigates the alert and discovers that a legitimate user entered the wrong credential several times. A false negative is when a threat actor tries to brute-force attack a system and no alert is raised.
- D. A false negative is a legitimate attack triggering a brute-force alert. An engineer investigates the alert and finds out someone intended to break into the system. A false positive is when no alert and no attack is occurring.
Answer:
c
Question 8
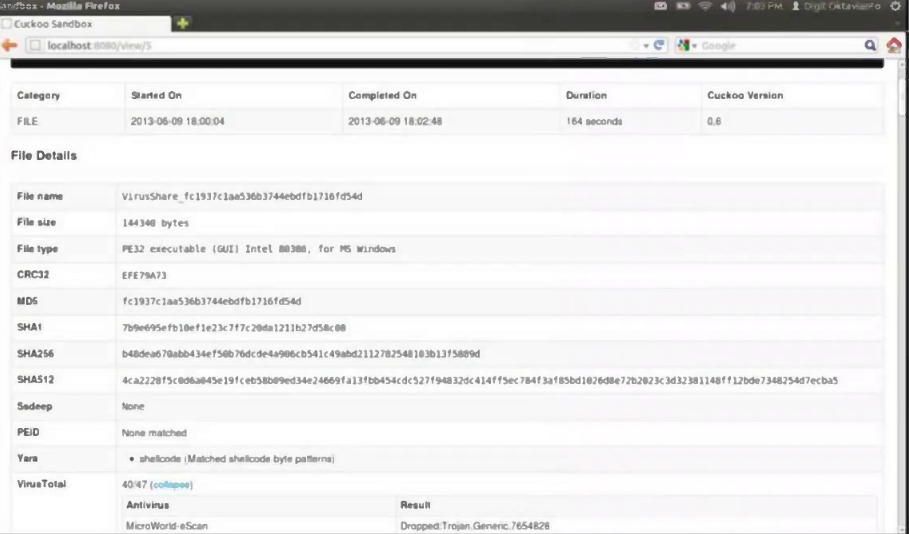
Refer to the exhibit. What does this Cuckoo sandbox report indicate?
- A. The file is ransomware.
- B. The file is spyware.
- C. The file will open unsecure ports when executed.
- D. The file will open a command interpreter when executed.
Answer:
b
Question 9
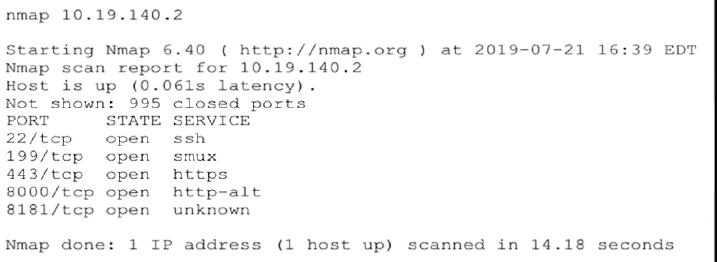
Refer to the exhibit. An attacker gained initial access to the companys network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data. Which two elements can an attacker identify from the scan? (Choose two.)
- A. workload and the configuration details
- B. functionality and purpose of the server
- C. number of users and requests that the server is handling
- D. running services
- E. user accounts and SID
Answer:
bd
Question 10
Which action prevents buffer overflow attacks?
- A. variable randomization
- B. using web based applications
- C. input validation
- D. using a Linux operating system
Answer:
c