CheckPoint 156-215-80 practice test
Check Point Certified Security Administrator R80 Exam
Question 1
When should you generate new licenses?
A. Before installing contract files.
B. After a device upgrade.
C. When the existing license expires, license is upgraded or the IP-address associated with
the license changes.
D. Only when the license is upgraded.
Answer:
B
Question 2
Which of the following situations would not require a new license to be generated and
installed?
- A. The Security Gateway is upgraded.
- B. The existing license expires.
- C. The license is upgraded.
- D. The IP address of the Security Management or Security Gateway has changed.
Answer:
A
Question 3
An administrator wishes to enable Identity Awareness on the Check Point firewalls. However
they allow users to use company issued or personal laptops. Since the administrator cannot
manage the personal laptops, which of the following methods would BEST suit this
company?
- A. AD Query
- B. Browser-Based Authentication
- C. Identity Agents
- D. Terminal Servers Agent
Answer:
B
Question 4
In ____________ NAT, the ____________ is translated.
- A. Hide; source
- B. Static; source
- C. Simple; source
- D. Hide; destination
Answer:
A
Question 5
When a Security Gateway sends its logs to an IP address other than its own, which
deployment option is installed?
- A. Distributed
- B. Standalone
- C. Bridge Mode
- D. Targeted
Answer:
A
Question 6
Which of the following is considered to be the more secure and preferred VPN authentication
method?
- A. Password
- B. Certificate
- C. MD5
- D. Pre-shared secret
Answer:
B
Question 7
To quickly review when Threat Prevention signatures were last updated, which Threat Tool
would an administrator use?
- A. Protections
- B. IPS Protections
- C. Profiles
- D. ThreatWiki
Answer:
B
Question 8
Which back up method uses the command line to create an image of the OS?
- A. System backup
- B. Save Configuration
- C. Migrate
- D. snapshot
Answer:
D
Question 9
Which repositories are installed on the Security Management Server by SmartUpdate?
- A. License and Update
- B. Package Repository and Licenses
- C. Update and License & Contract
- D. License & Contract and Package Repository
Answer:
D
Question 10
What data MUST be supplied to the SmartConsole System Restore window to restore a
backup?
- A. Server, Username, Password, Path, Version
- B. Username, Password, Path, Version
- C. Server, Protocol, Username, Password, Destination Path
- D. Server, Protocol, Username, Password, Path
Answer:
D
Question 11
View the rule below. What does the pen-symbol in the left column mean?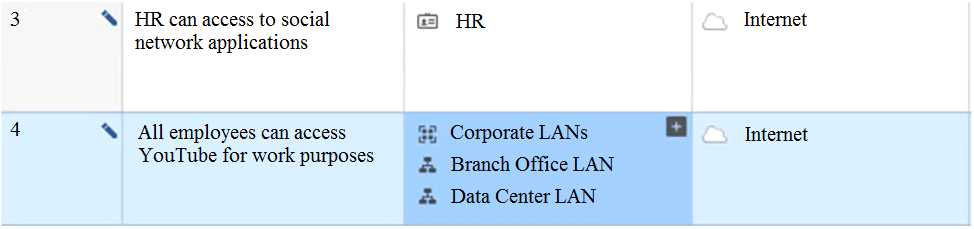
- A. Those rules have been published in the current session.
- B. Rules have been edited by the logged in administrator, but the policy has not been published yet.
- C. Another user has currently locked the rules for editing.
- D. The configuration lock is present. Click the pen symbol in order to gain the lock.
Answer:
B
Question 12
What object type would you use to grant network access to an LDAP user group?
- A. Access Role
- B. User Group
- C. SmartDirectory Group
- D. Group Template
Answer:
B
Question 13
Which of the following technologies extracts detailed information from packets and stores
that information in state tables?
- A. INSPECT Engine
- B. Next-Generation Firewall
- C. Packet Filtering
- D. Application Layer Firewall
Answer:
B
Question 14
An administrator is creating an IPsec site-to-site VPN between his corporate office and
branch office. Both offices are protected by Check Point Security Gateway managed by the
same Security Management Server (SMS). While configuring the VPN community to specify
the pre-shared secret, the administrator did not find a box to input the pre-shared secret. Why
does it not allow him to specify the pre-shared secret?
- A. The Gateway is an SMB device
- B. The checkbox “Use only Shared Secret for all external members” is not checked
- C. Certificate based Authentication is the only authentication method available between two Security Gateway managed by the same SMS
- D. Pre-shared secret is already configured in Global Properties
Answer:
C
Question 15
Which of the following is NOT a policy type available for each policy package?
- A. Threat Emulation
- B. Access Control
- C. Desktop Security
- D. Threat Prevention
Answer:
A