C. Change the order of the resources in the template so that the RDS resource is listed before the EC2 instance resource.
A company has a new requirement stating that all resources in AWS must be tagged according to a set policy.
Which AWS service should be used to enforce and continually identify all resources that are not in compliance with the
policy?
C
Explanation:
Reference: https://aws.amazon.com/config/
A company uses an AWS CloudFormation template to provision an Amazon EC2 instance and an Amazon RDS DB
instance. A SysOps administrator must update the template to ensure that the DB instance is created before the EC2
instance is launched.
What should the SysOps administrator do to meet this requirement?
B
C. Change the order of the resources in the template so that the RDS resource is listed before the EC2 instance resource.
A database is running on an Amazon RDS Multi-AZ DB instance. A recent security audit found the database to be out of
compliance because it was not encrypted.
Which approach will resolve the encryption requirement?
A
Explanation:
Reference: https://cloudkul.com/blog/how-to-encrypt-aws-rds-database/
A. Log in to the RDS console and select the encryption box to encrypt the database.
A company has an infernal web application that runs on Amazon EC2 instances behind an Application Load Balancer. The
instances run in an Amazon EC2 Auto Scaling group in a single Availability Zone. A SysOps administrator must make the
application highly available.
Which action should the SysOps administrator take to meet this requirement?
C
A development team recently deployed a new version of a web application to production. After the release, penetration
testing revealed a cross-site scripting vulnerability that could expose user data.
Which AWS service will mitigate this issue?
B
Explanation:
Reference: https://docs.aws.amazon.com/waf/latest/developerguide/waf-rule-statement-type-xss-match.html
A company using AWS Organizations requires that no Amazon S3 buckets in its production accounts should ever be
deleted.
What is the SIMPLEST approach the SysOps administrator can take to ensure S3 buckets in those accounts can never be
deleted?
B
The security team is concerned because the number of AWS Identity and Access Management (IAM) policies being used in
the environment is increasing. The team tasked a SysOps administrator to report on the current number of IAM policies in
use and the total available IAM policies.
Which AWS service should the administrator use to check how current IAM policy usage compares to current service limits?
A
Explanation:
Reference: https://docs.aws.amazon.com/awssupport/latest/user/trusted-advisor-check-reference.html#iam-policies
C. AWS Config
An organization with a large IT department has decided to migrate to AWS. With different job functions in the IT department,
it is not desirable to give all users access to all AWS resources. Currently the organization handles access via LDAP group
membership.
What is the BEST method to allow access using current LDAP credentials?
D
Explanation:
Reference: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_enable-console-saml.html
A company is testing Amazon Elasticsearch Service (Amazon ES) as a solution for analyzing system logs from a fleet of
Amazon EC2 instances. During the test phase, the domain operates on a singlenode cluster. A SysOps administrator needs
to transition the test domain into a highly available production-grade deployment.
Which Amazon ES configuration should the SysOps administrator use to meet this requirement?
B
A SysOps administrator is evaluating Amazon Route 53 DNS options to address concerns about high availability for an on-
premises website. The website consists of two servers: a primary active server and a secondary passive server. Route 53
should route traffic to the primary server if the associated health check returns 2xx or 3xx HTTP codes. All other traffic
should be directed to the secondary passive server. The failover record type, set ID, and routing policy have been set
appropriately for both primary and secondary servers.
Which next step should be taken to configure Route 53?
C
Explanation:
Reference: https://docs.aws.amazon.com/Route53/latest/DeveloperGuide/health-checks-how-route-53-chooses-records.html
An Amazon EC2 instance is running an application that uses Amazon Simple Queue Service (Amazon SQS) queues. A
SysOps administrator must ensure that the application can read, write, and delete messages from the SQS queues.
Which solution will meet these requirements in the MOST secure manner?
D
D. Create and associate an IAM role that allows EC2 instances to call AWS services. Attach an IAM policy to the role that allows the sqs:SendMessage permission, the sqs:ReceiveMessage permission, and the sqs:DeleteMessage permission to the appropriate queues.
A SysOps administrator needs to give users the ability to upload objects to an Amazon S3 bucket. The SysOps administrator
creates a presigned URL and provides the URL to a user, but the user cannot upload an object to the S3 bucket. The
presigned URL has not expired, and no bucket policy is applied to the S3 bucket.
Which of the following could be the cause of this problem?
B
Explanation:
Reference: https://docs.aws.amazon.com/AmazonS3/latest/userguide/example-bucket-policies.html
C. The SysOps administrator must apply a bucket policy to the S3 bucket to allow the user to upload the object.
An errant process is known to use an entire processor and run at 100%. A SysOps administrator wants to automate
restarting the instance once the problem occurs for more than 2 minutes.
How can this be accomplished?
B
Explanation:
Reference: https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/UsingAlarmActions.html
B. Create a CloudWatch alarm for the EC2 instance with detailed monitoring. Enable an action to restart the instance.
A company wants to track its expenditures for Amazon EC2 and Amazon RDS within AWS. The company decides to
implement more rigorous tagging requirements for resources in its AWS accounts. A SysOps administrator needs to identify
all noncompliant resources.
What is the MOST operationally efficient solution that meets these requirements?
C
Explanation:
Reference: https://docs.aws.amazon.com/config/latest/developerguide/required-tags.html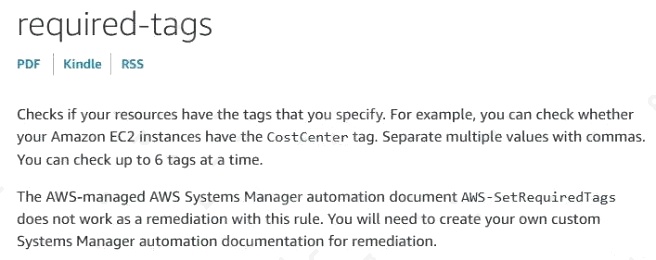
B. Create a rule in AWS Config that invokes a custom AWS Lambda function that will evaluate all resources for the specified tags.
A company is using an AWS KMS customer master key (CMK) with imported key material. The company references the
CMK by its alias in the Java application to encrypt data. The CMK must be rotated every 6 months.
What is the process to rotate the key?
B
Explanation:
Reference: https://aws.amazon.com/kms/faqs/
C . AWS Config